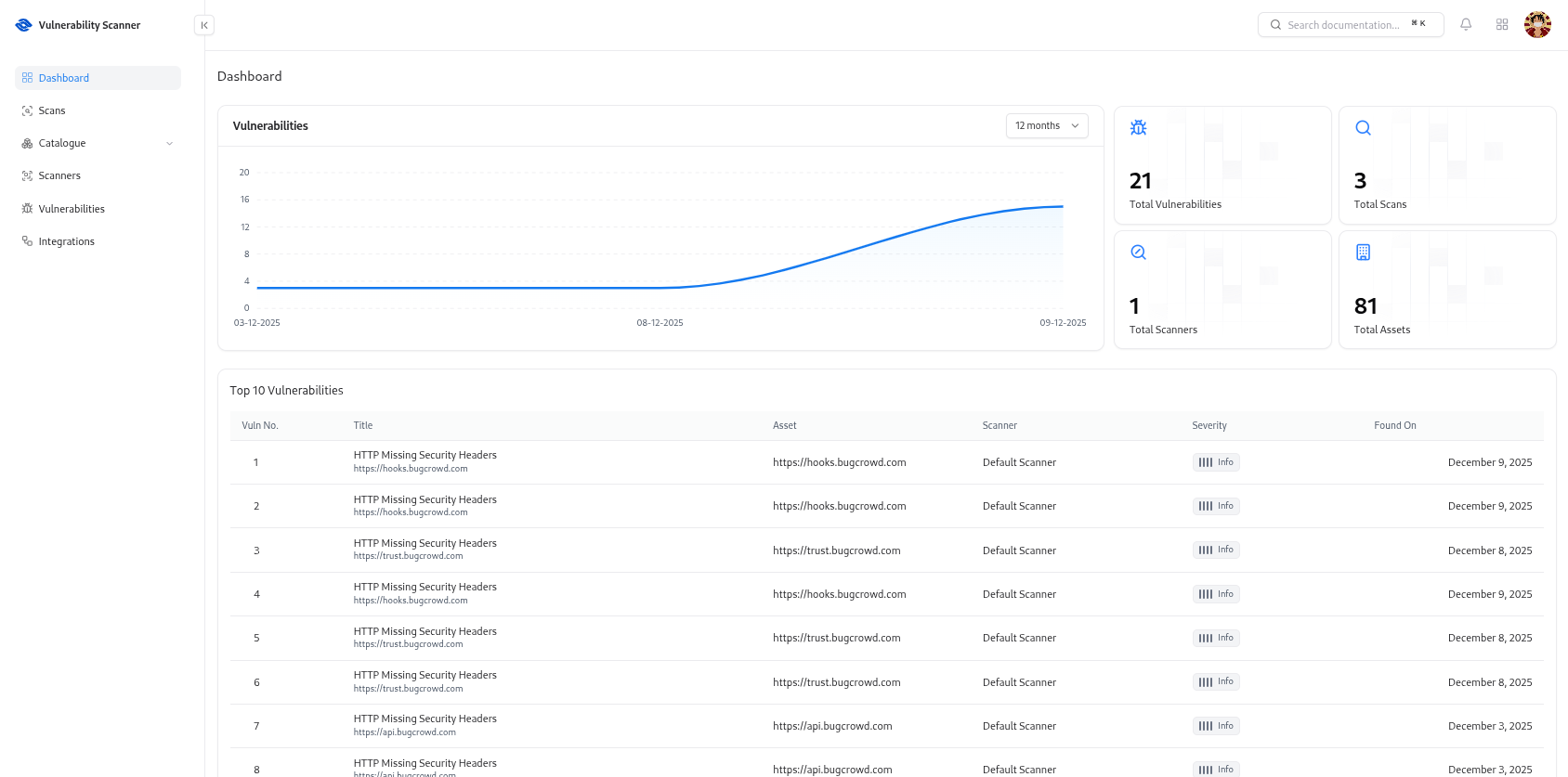
It serves as the command center for monitoring risk trends and prioritizing remediation.
Overview
The Dashboard consolidates insights from all scan engines and displays the current state of:- Total vulnerabilities detected
- Severity-level distribution
- Total scans performed
- Active scanners
- Asset coverage
Key Metrics & Analytics
Total Vulnerabilities
Displays the complete count of vulnerabilities detected across all assets.
Total Scans
Shows how many scans have been executed historically.
Active Scanners
Indicates how many scanner engines are connected and reporting.
Total Assets
Number of assets discovered in the scanner’s catalogue.
Coverage Trend
Tracks scan coverage improvements or declines over time.
Risk Visibility
Shows how much of your attack surface has been assessed.
Vulnerability Trend Graph
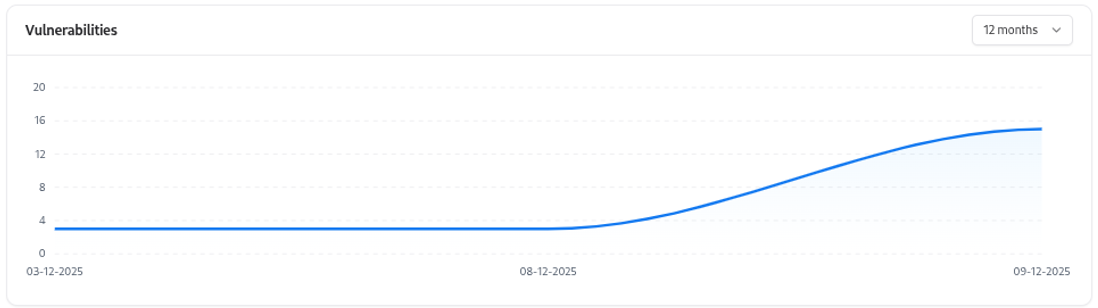
- Vulnerability spikes
- Reduction after remediation efforts
- Seasonal or deployment-related changes
- Scanner efficiency over time
Top 10 Vulnerabilities
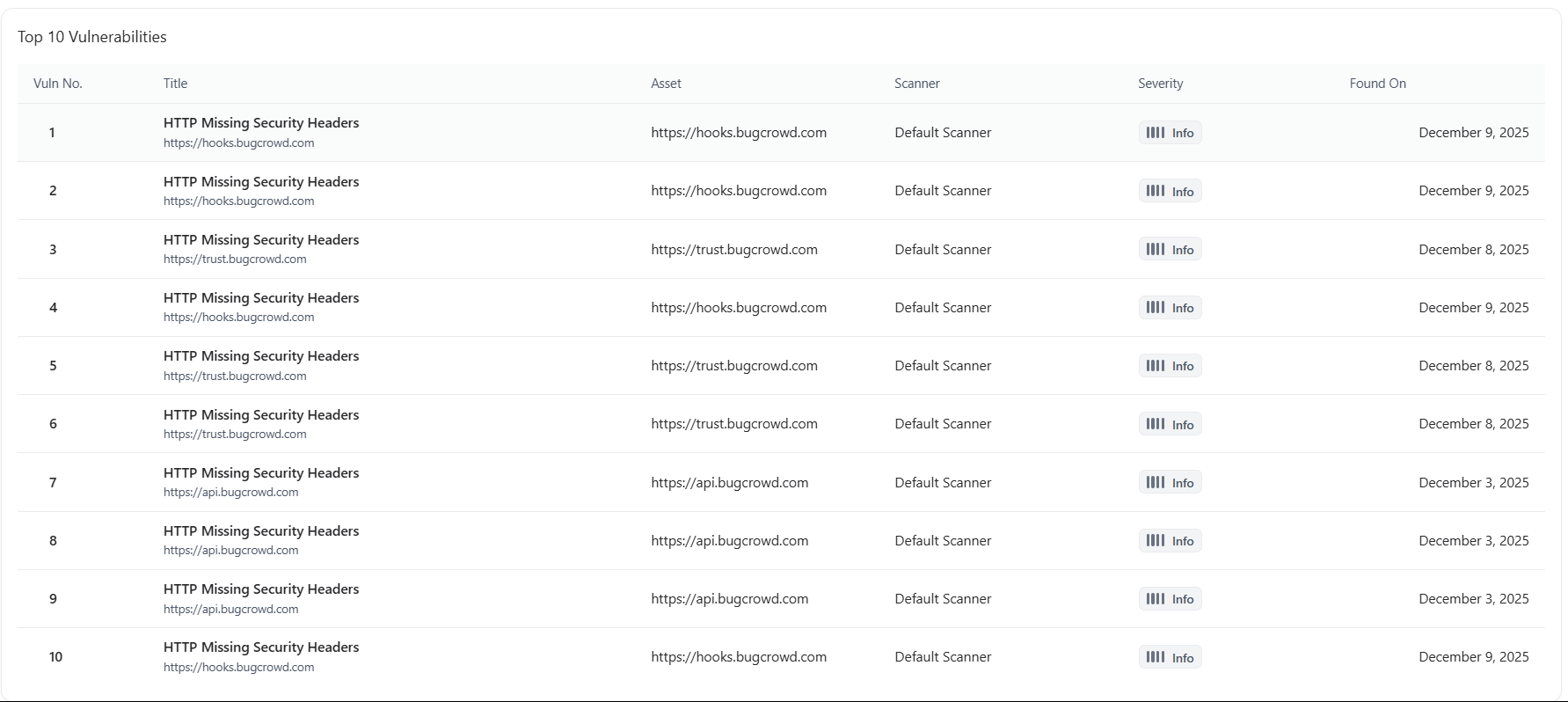
- Most common issues
- Repeated misconfigurations
- High-frequency weaknesses
- Vulnerabilities concentrated on specific assets
- Title
- Asset
- Scanner
- Severity
- Found On
Severity Snapshot
Critical
Count of critical severity vulnerabilities (currently may show 0 if none detected).
High
High severity issues requiring prompt remediation.
Medium
Moderate risks that may require patching or configuration fixes.
Low / Info
Low-risk findings such as missing headers or informational signals.
Asset Exposure & Coverage
The dashboard highlights:- Total discovered assets
- Assets with vulnerabilities
- Safe assets
- Percentage coverage
How to Use the Dashboard
Monitor Risk Posture
Track changes in vulnerability count and criticality over time.
Prioritize Fixes
Use severity, frequency, and asset importance to prioritize remediation.
Validate Scanning Health
Ensure scanners are active and scan cycles are running as expected.
Detect Anomalies
Identify sudden spikes that may indicate new vulnerabilities or exposed assets.
Next Steps
View Vulnerability Catalogue
Explore full vulnerability details, states, and remediation workflows.