Overview
The API Catalog in AIM provides centralized visibility into every API and endpoint discovered across your organization.It combines analytics, exposure intelligence, and risk scoring to help teams understand their API landscape and mitigate risks proactively.
Overview
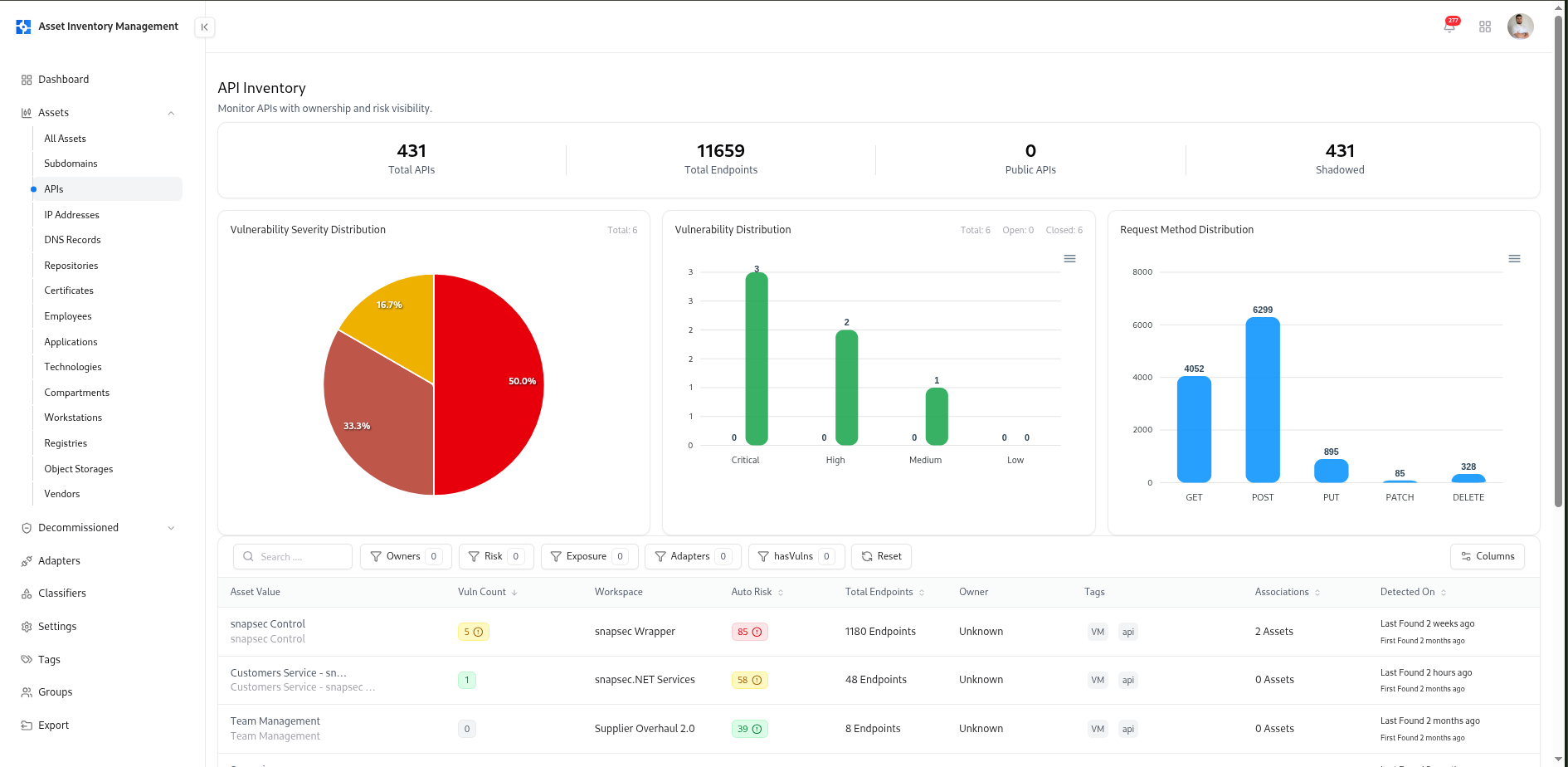
The API Catalog serves as a comprehensive inventory of all APIs identified through integrations, scanners, or adapters (such as Postman, VM, or TechDetect).It consolidates discovery, vulnerability data, request method analytics, and exposure indicators into one unified interface. This catalog empowers teams to monitor shadow APIs, enforce ownership, and ensure complete coverage across internal, external, and partner APIs.
Key Metrics and Analytics
Total APIs
Displays the total number of APIs discovered within your organization.
Total Endpoints
Shows the total number of individual endpoints across all APIs.
Shadowed APIs
Highlights APIs discovered outside approved inventories, often representing untracked or unmanaged services.
Vulnerability Severity Distribution
Pie chart visualization of vulnerability severities across all APIs — Critical, High, Medium, and Low.
Vulnerability Distribution
Bar chart displaying the number of open vs. resolved vulnerabilities for APIs.
Request Method Distribution
Analyzes the distribution of HTTP request methods (GET, POST, PUT, PATCH, DELETE), helping teams understand usage and potential risks.
Search, Filters, and Sorting
The API catalog supports multi-dimensional filtering for precise visibility and control:| Filter | Description |
|---|---|
| Owners | Filter by assigned API owner or responsible workspace. |
| Risk | Filter APIs based on calculated Auto Risk score. |
| Exposure | Show APIs that are exposed or shadowed. |
| Adapters | Filter APIs imported from specific adapters (e.g., Postman, VM, or TechDetect). |
| Tags | Filter APIs by technology or business tags (e.g., Postman, API). |
| hasVulns | Show APIs with linked vulnerabilities. |
| Date Range | Filter by first or last discovery date. |
API Table Columns
Each API record includes rich contextual data:| Column | Description |
|---|---|
| Asset Value | API name or workspace identifier. |
| Vuln Count | Number of vulnerabilities linked to the API. |
| Workspace | The Postman or internal workspace where the API resides. |
| Auto Risk | Automatically computed risk score based on vulnerabilities, exposure, and classification rules. |
| Total Endpoints | Total number of active endpoints within the API. |
| Owner | Assigned person or workspace responsible for the API. |
| Tags | Technology or discovery tags (e.g., Postman, API). |
| Associations | Related assets connected to the API. |
| Detected On | Timestamp of last discovery and first identification. |
API Full View
Each API in AIM is automatically enriched with vulnerability data, ownership, tags, and endpoint-level analytics.This detailed view enables continuous visibility into API health, endpoint exposure, and security posture.
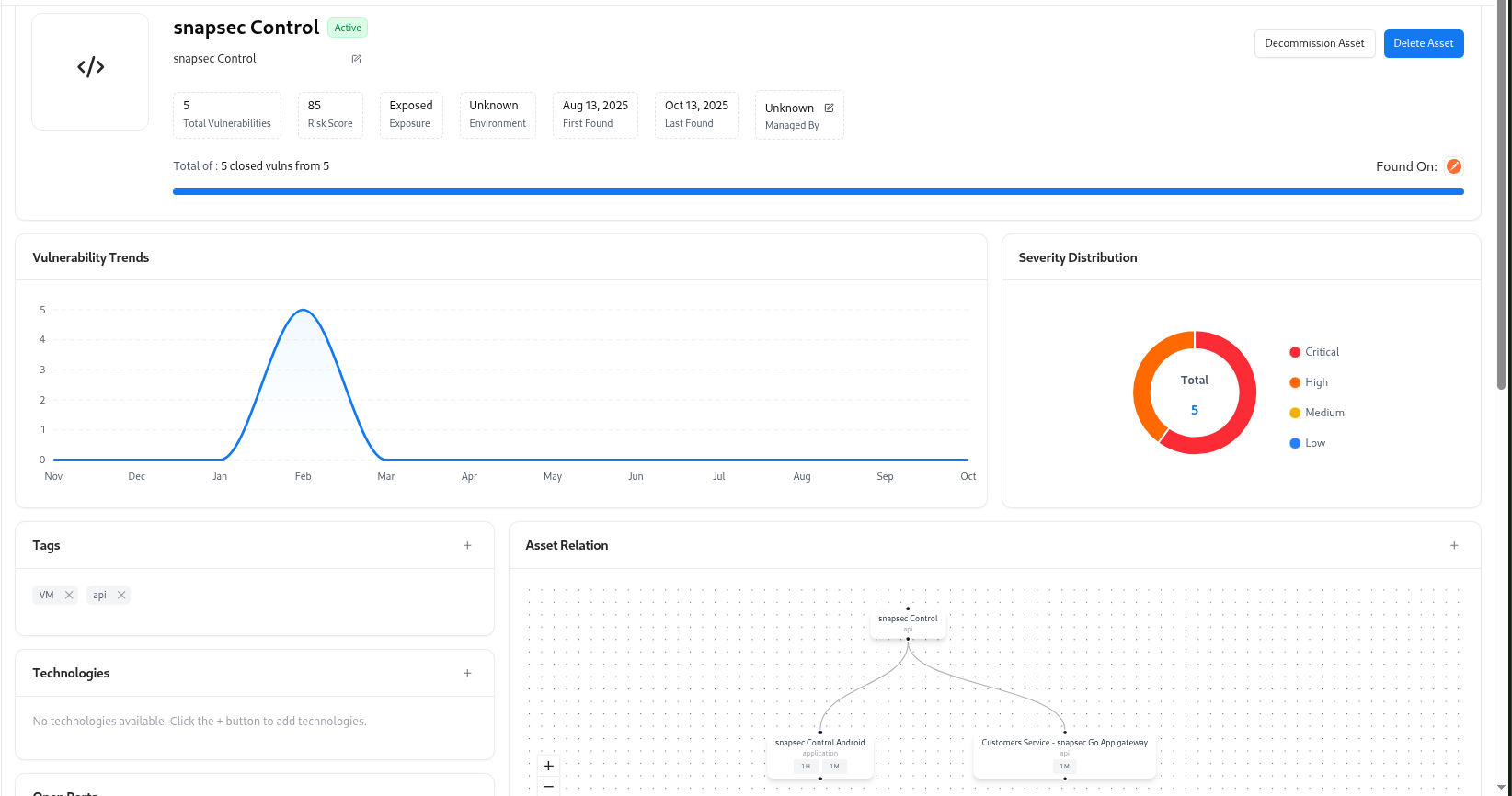
API Summary
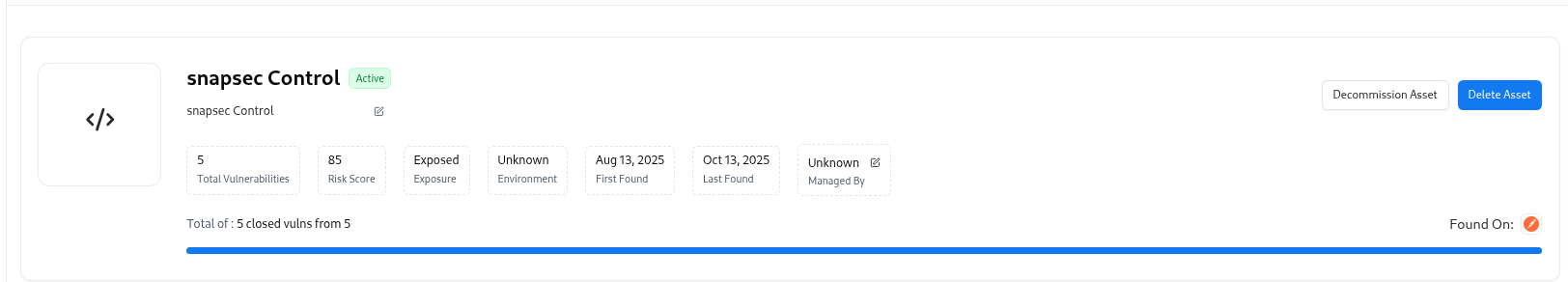
| Field | Description |
|---|---|
| API Name | Name of the API asset (e.g., snapsec Control). |
| Status | Indicates if the API is Active or Decommissioned. |
| Source | Displays which adapter or workspace provided the API (e.g., Postman). |
| Exposed | Marks whether the API is exposed to public networks. |
| Environment | Identifies the deployment environment (e.g., Production, Staging, Dev). |
| Risk Score | Shows the calculated Auto Risk value. |
| Managed By | Lists the assigned owner or team responsible for maintenance. |
| Detection History | Shows first and last detection timestamps. |
Vulnerability Insights
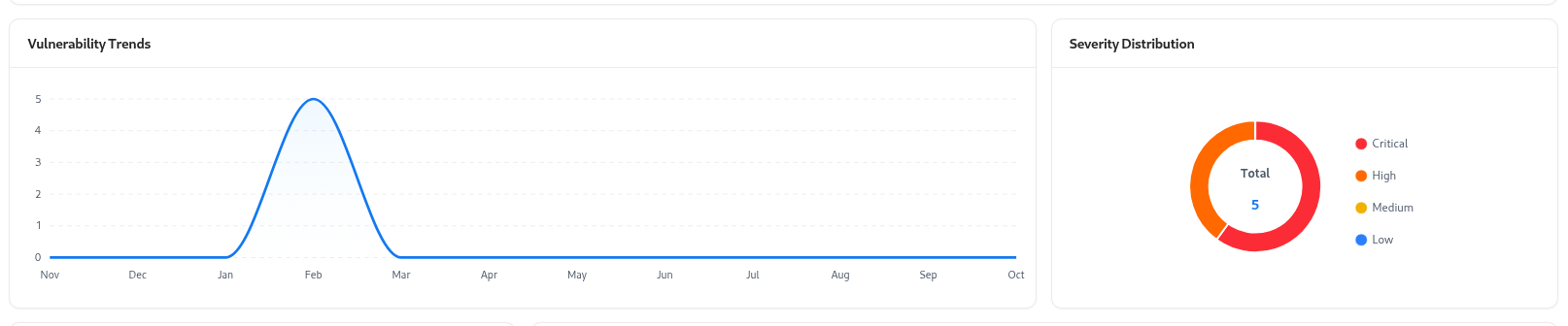
Vulnerability Trends
Visual representation of vulnerabilities over time for the selected API, showing how remediation affects the trend line.
Severity Distribution
Distribution chart showing vulnerabilities categorized as Critical, High, Medium, or Low.
- Vulnerability title
- Assessment source
- Severity
- State (
Resolved,In Review,Retest) - Detection history
Tags, Technologies, and Relations
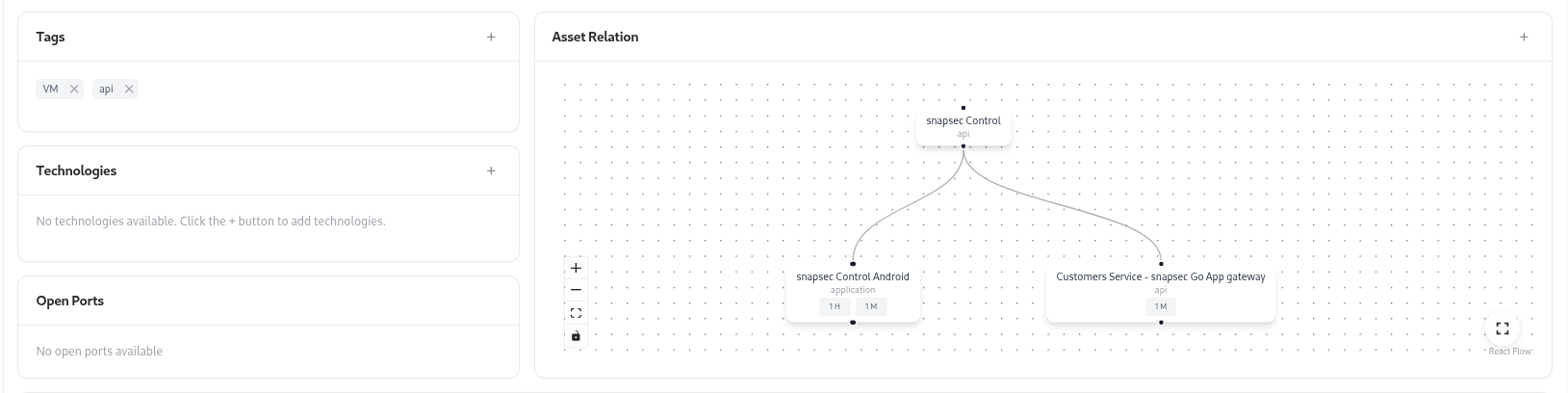
Tags
Tags applied automatically from adapters or manually by teams (e.g.,
Postman, API, Internal).Technologies
Lists backend technologies or services powering the API (e.g., Node.js, FastAPI, Flask).
Endpoints and Methods
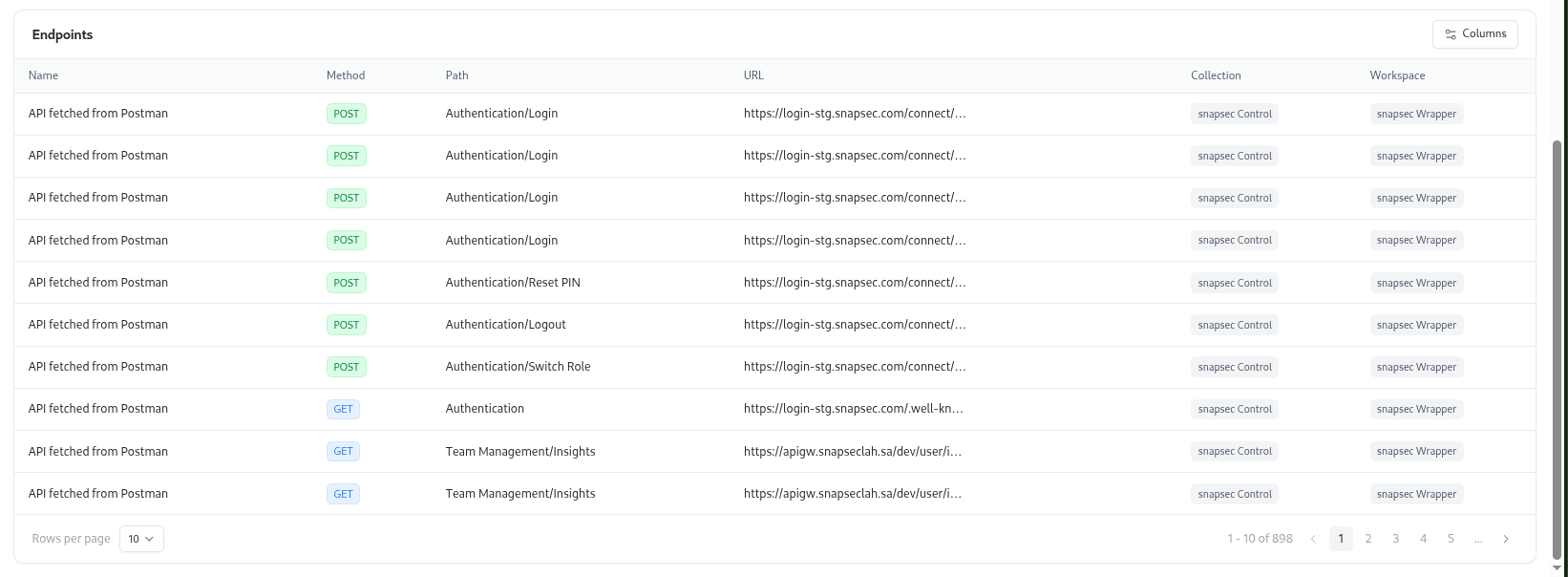
| Column | Description |
|---|---|
| Name | Endpoint or request title. |
| Method | HTTP method (GET, POST, PUT, PATCH, DELETE). |
| Path | API route or path identifier. |
| URL | Full request URL. |
| Collection | Postman collection or internal group reference. |
| Workspace | Workspace in which the API is registered. |
Ownership & Management Actions
Each API asset supports lifecycle operations:- Assign Owner – designate an individual or workspace owner.
- Decommission API – mark outdated APIs for archival or removal.
- Delete API – remove from active inventory.
How APIs Are Discovered
AIM continuously updates API data using connected adapters and integrations:- Postman Adapter – imports APIs and collections from workspaces.
- TechDetect Adapter – fingerprints API technologies and request methods.
- VM Adapter – enriches APIs with vulnerability data from security assessments.
Example Use Cases
- API Security Teams: Identify shadow or unmanaged APIs.
- Developers: Track active endpoints and ensure alignment with environment policies.
- Compliance Officers: Audit exposed APIs for data sensitivity and regulatory controls.
- Engineering Leads: Measure API growth and assess operational risks.
Explore Live Demo
Explore AIM Live — No Signup Needed
Instantly explore how Snapsec AIM discovers, enriches, and tracks every asset in real time — all without creating an account.