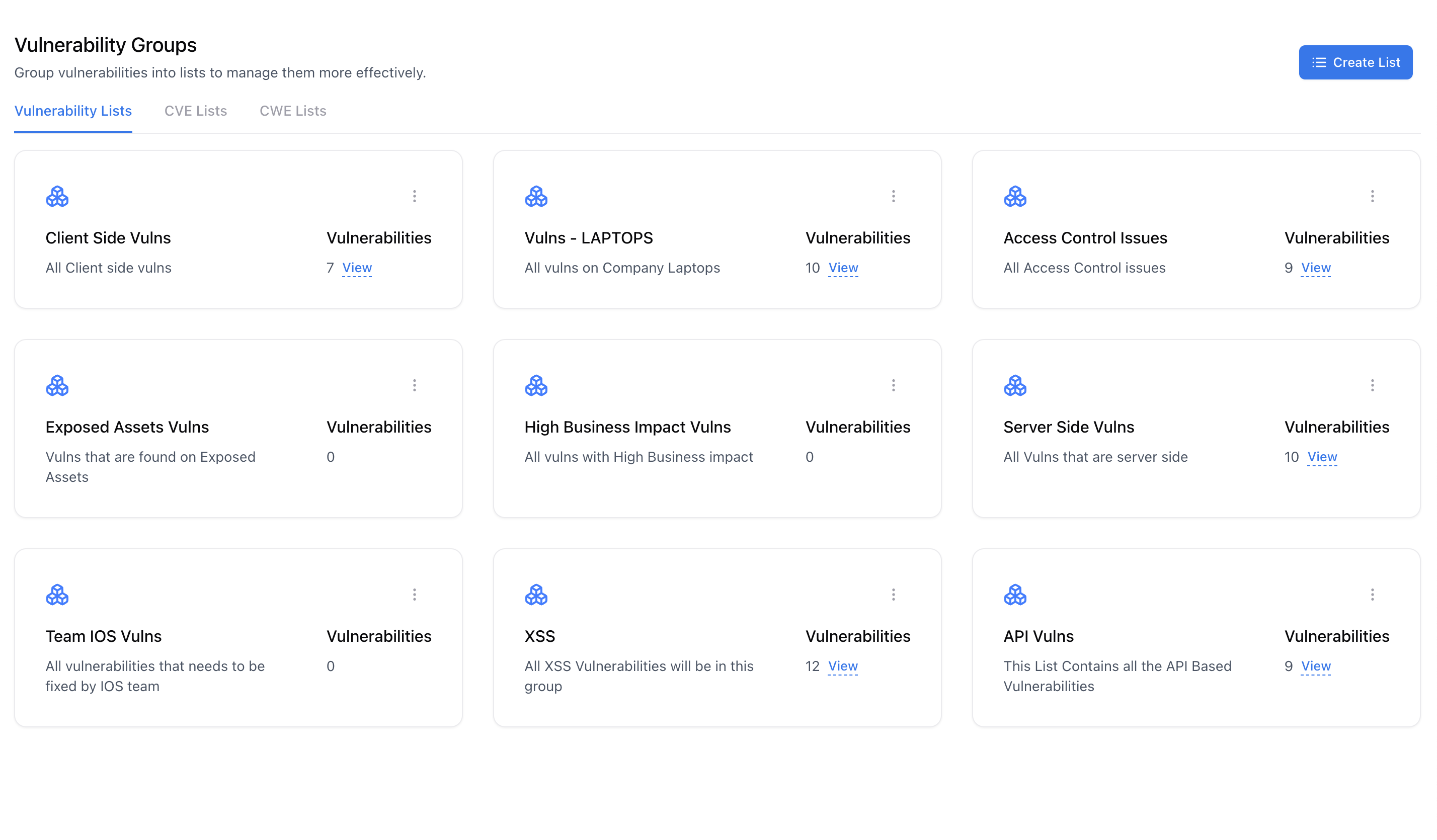
Overview
Vulnerability Groups enable you to organize vulnerabilities from multiple assets, assessments, and sources into logical collections — such as all Access Control issues or API-related vulnerabilities.This helps teams prioritize fixes, track themes, and export consolidated reports with ease. Groups can be defined by vulnerability types, impacted components, responsible teams, or business context. They act as dynamic workspaces to simplify remediation management across large vulnerability datasets.
Use Cases
- Group all Access Control or Authentication issues across multiple systems.
- Maintain separate vulnerability lists per team or department.
- Create category-based views (e.g., API Vulnerabilities, Web XSS Issues, Encryption Weaknesses).
- Generate consolidated reports for specific vulnerability families.
Creating or Updating a Group
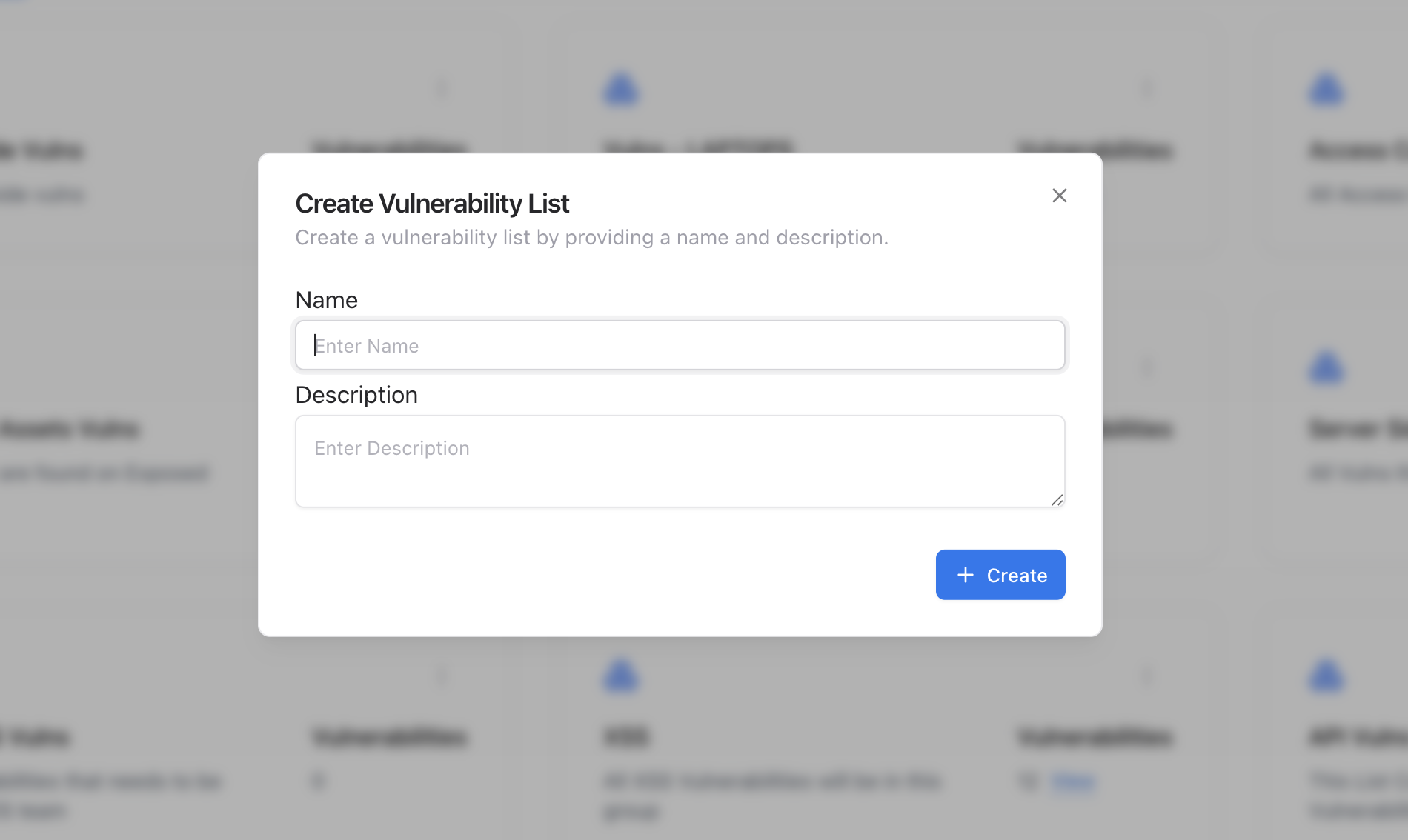
Click ‘Create Group’
Provide a name (e.g., “XSS” or “API Vulnerabilities”) and an optional description to help categorize the group.
Save Group
Once saved, your new group will appear in the list, ready to be populated with vulnerabilities.
Viewing Vulnerabilities in a Group
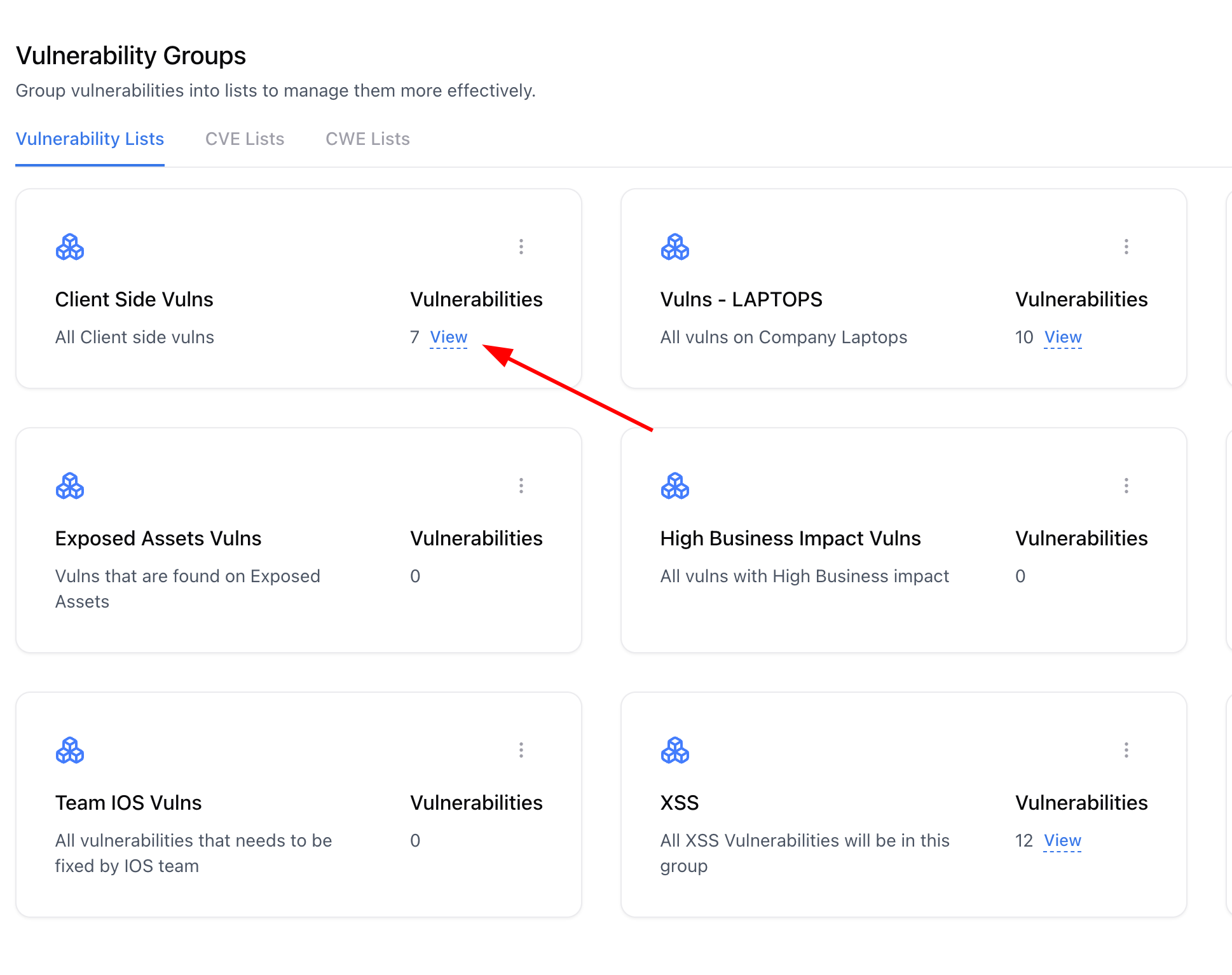
Review Grouped Vulnerabilities
View all vulnerabilities added to that group, along with their severity, state, and associated assessments.
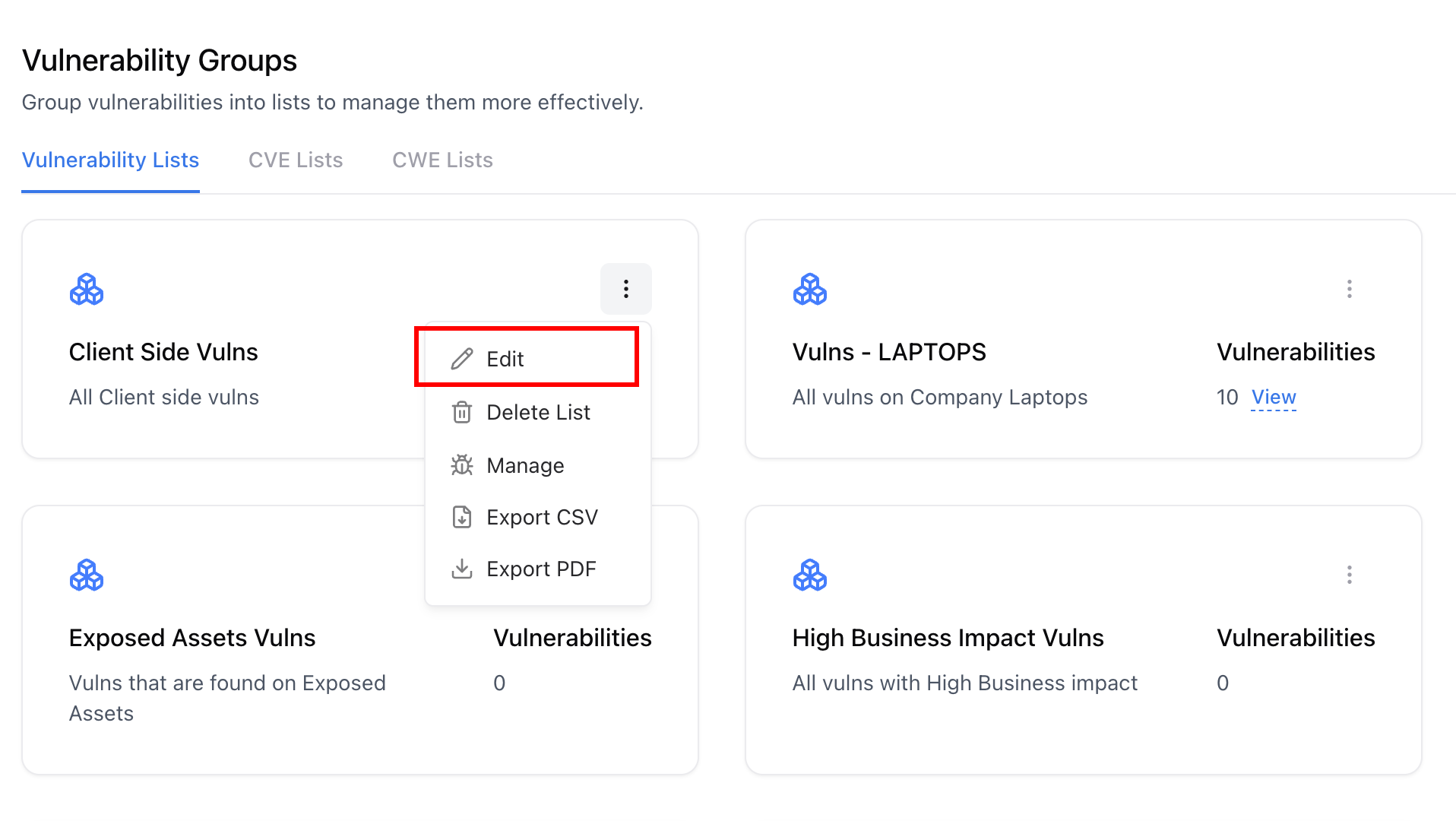
Adding or Removing Vulnerabilities
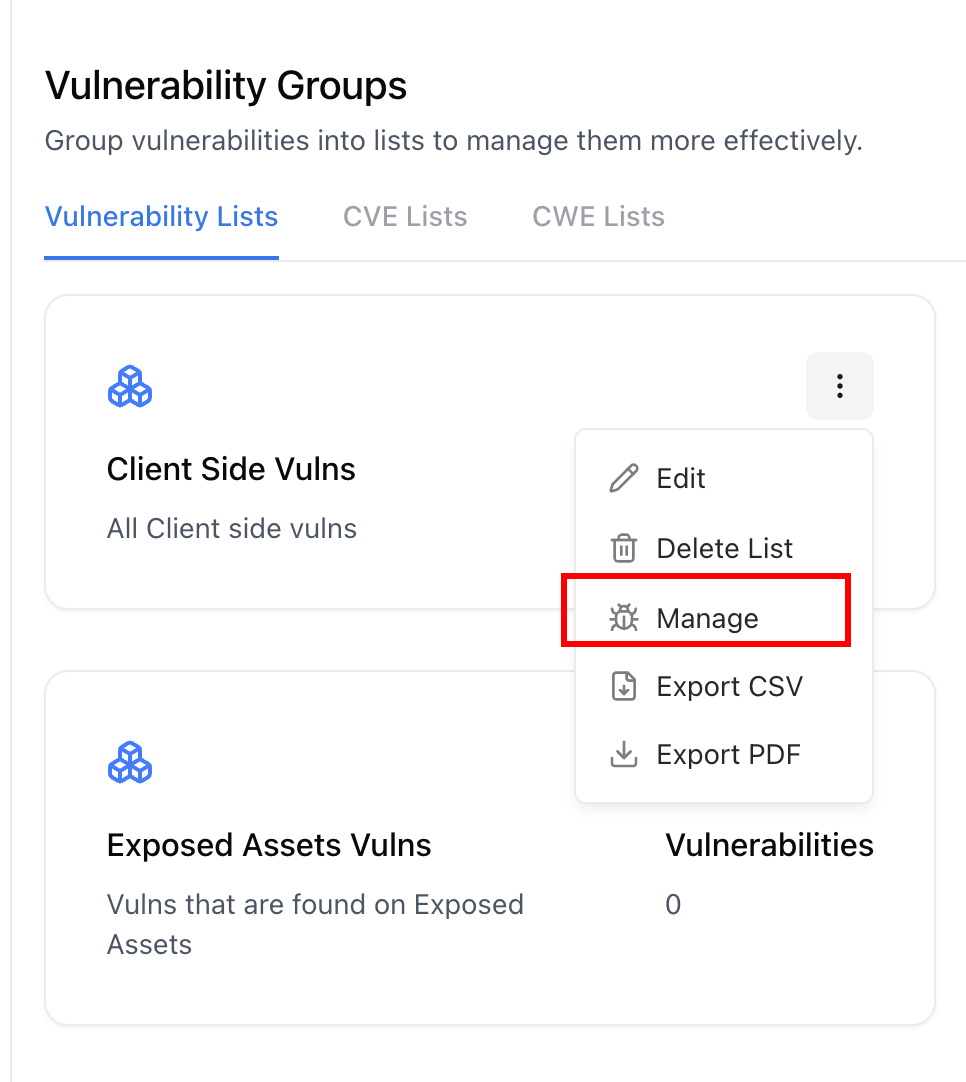
Add Vulnerabilities
Search across all vulnerabilities and select the ones you wish to add to the group.
Remove Vulnerabilities
To remove, deselect items or use the Remove button in the group management view.
Exporting Group Data
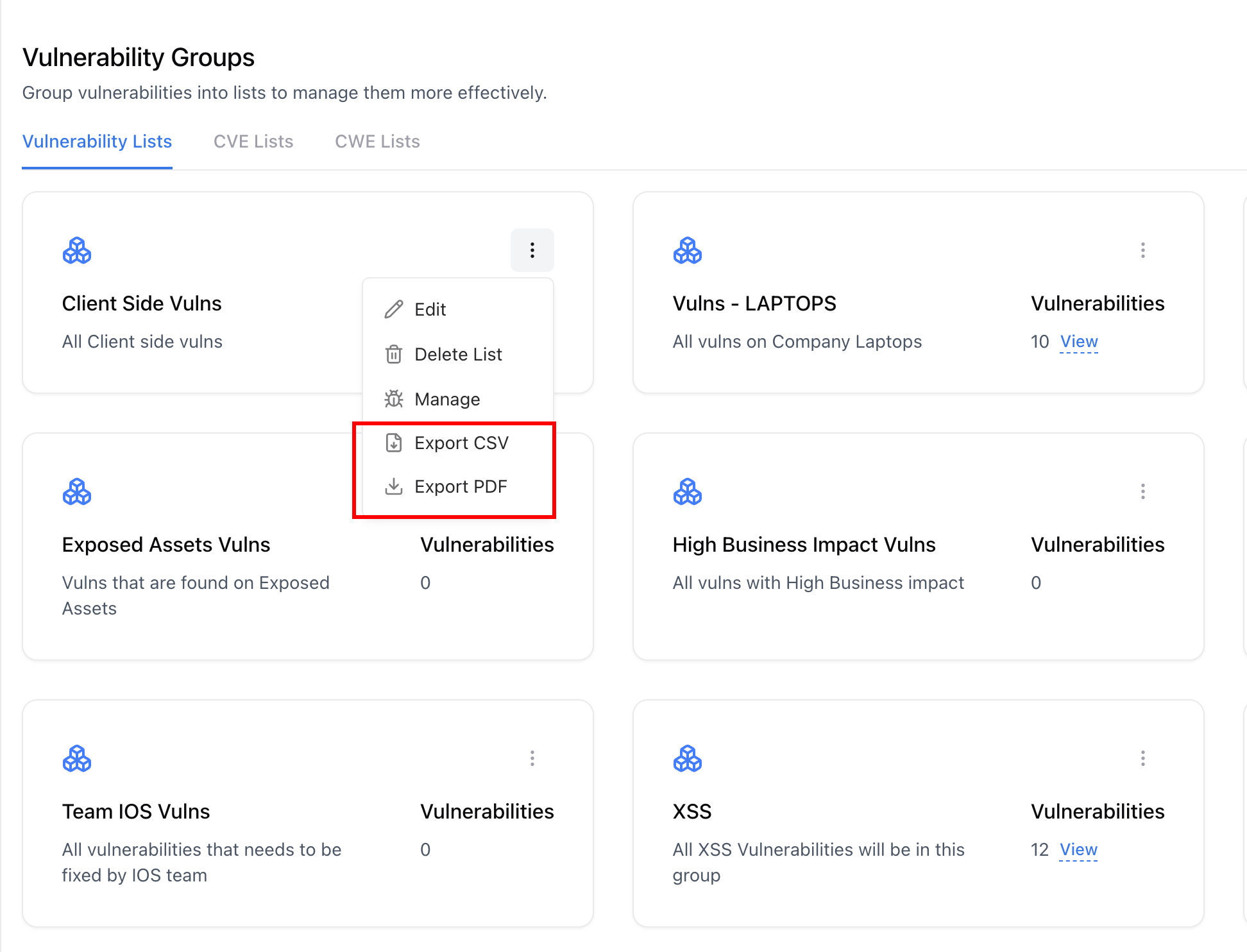
Export CSV
Export PDF Report
Select ‘Export PDF’
Generate a detailed Consolidated Vulnerability Report with full details, affected assets, CVSS scores, and remediation steps.
CWE-Based Grouping
Vulnerability Groups support organizing findings using CWE (Common Weakness Enumeration) classifications.This allows teams to group vulnerabilities based on root cause patterns, not just individual findings.
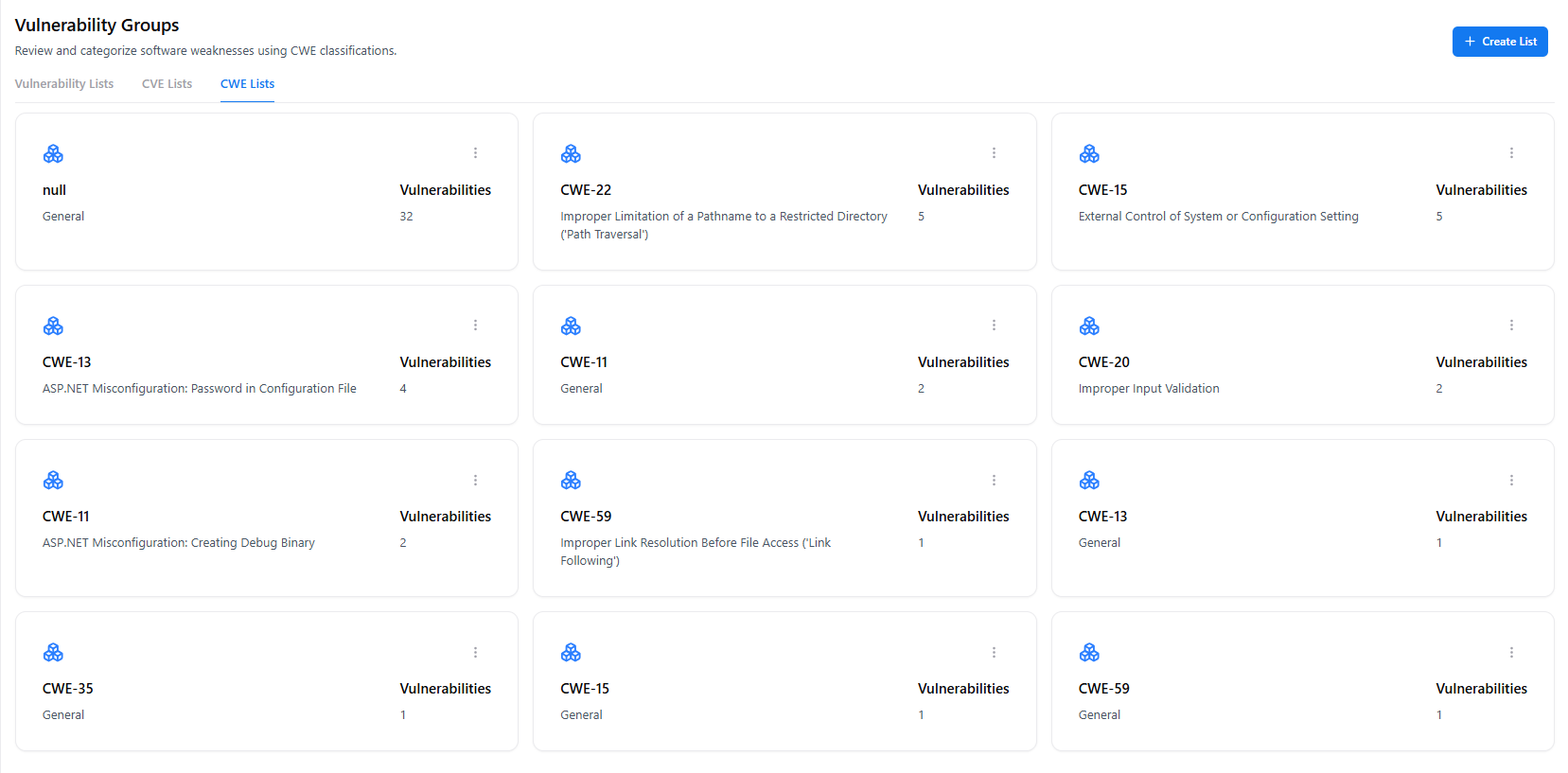
How CWE Grouping Helps
CWE-based grouping enables teams to:- Track recurring weakness classes (e.g., CWE-79, CWE-89, CWE-287) across applications
- Identify systemic security flaws instead of isolated bugs
- Prioritize remediation based on root causes, not just severity
- Align remediation efforts with secure coding standards and training programs
Creating a CWE-Based Group
Select CWE Criteria
Choose one or more CWE IDs (e.g., CWE-79: Cross-Site Scripting, CWE-287: Improper Authentication).
Example CWE Use Cases
- CWE-79 (XSS): Track all cross-site scripting issues across web applications
- CWE-89 (SQL Injection): Monitor database-related injection risks
- CWE-287 (Authentication): Review identity and access control weaknesses
- CWE-22 (Path Traversal): Identify file system exposure risks
Reporting with CWE Context
When exporting a Vulnerability Group:- CSV exports include CWE IDs for each vulnerability
- PDF reports summarize findings by CWE category, severity, and affected assets
- Secure coding reviews
- Engineering retrospectives
- Compliance and audit reporting
- Long-term risk reduction initiatives
Best Practices
- Create functional groups (e.g., API Issues, Auth Flaws) to align with engineering teams.
- Use CSV exports for bulk remediation tracking in external tools.
- Use PDF exports for client reporting or audit documentation.
- Review and refresh groups regularly to ensure updated vulnerability context.
Explore Live Demo
Explore Snapsec Live — No Signup Needed
Jump straight into the live environment and see how Snapsec unifies asset intelligence, threat detection, and vulnerability tracking — all in one dashboard.