Overview
The Registries Dashboard provides a centralized view of all container registries discovered across your organization, including cloud-based and on-prem registries. This view helps security and platform teams quickly understand registry exposure, vulnerability posture, and ownership status.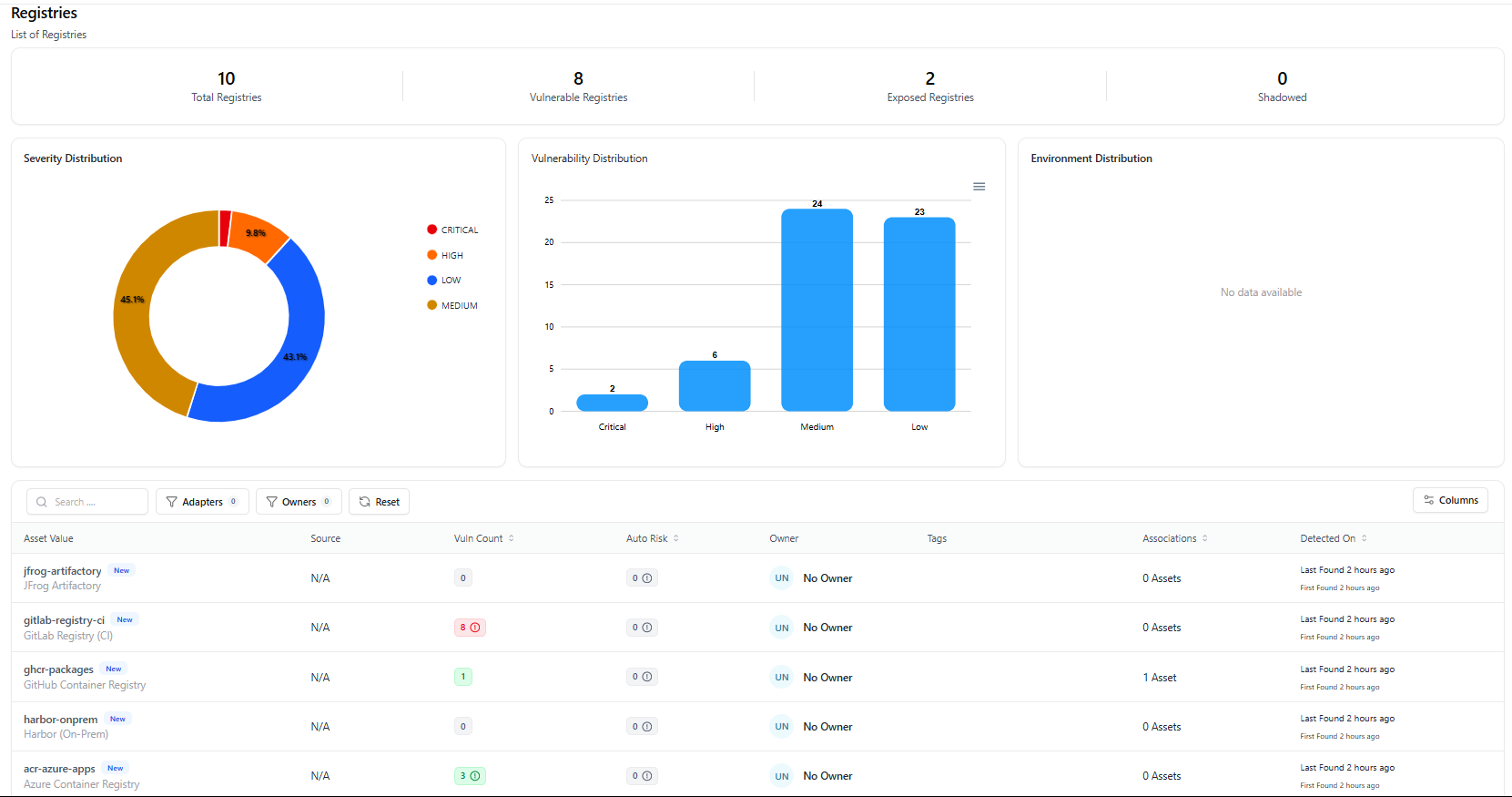
What the Dashboard Shows
- Total Registries — All detected container registries
- Vulnerable Registries — Registries with associated vulnerabilities
- Exposed Registries — Internet-facing or externally reachable registries
- Shadowed Registries — Unmanaged or unknown registries
- Severity Distribution — Critical, High, Medium, Low breakdown
- Vulnerability Distribution — Count by severity
- Environment Distribution — Prod, Dev, Staging (when available)
- Search registries by name
- Filter by adapters and owners
- Sort by vulnerability count or detection time
Total Vulnerabilities View
Clicking on the Vulnerability Count opens a focused breakdown of vulnerabilities associated with registries.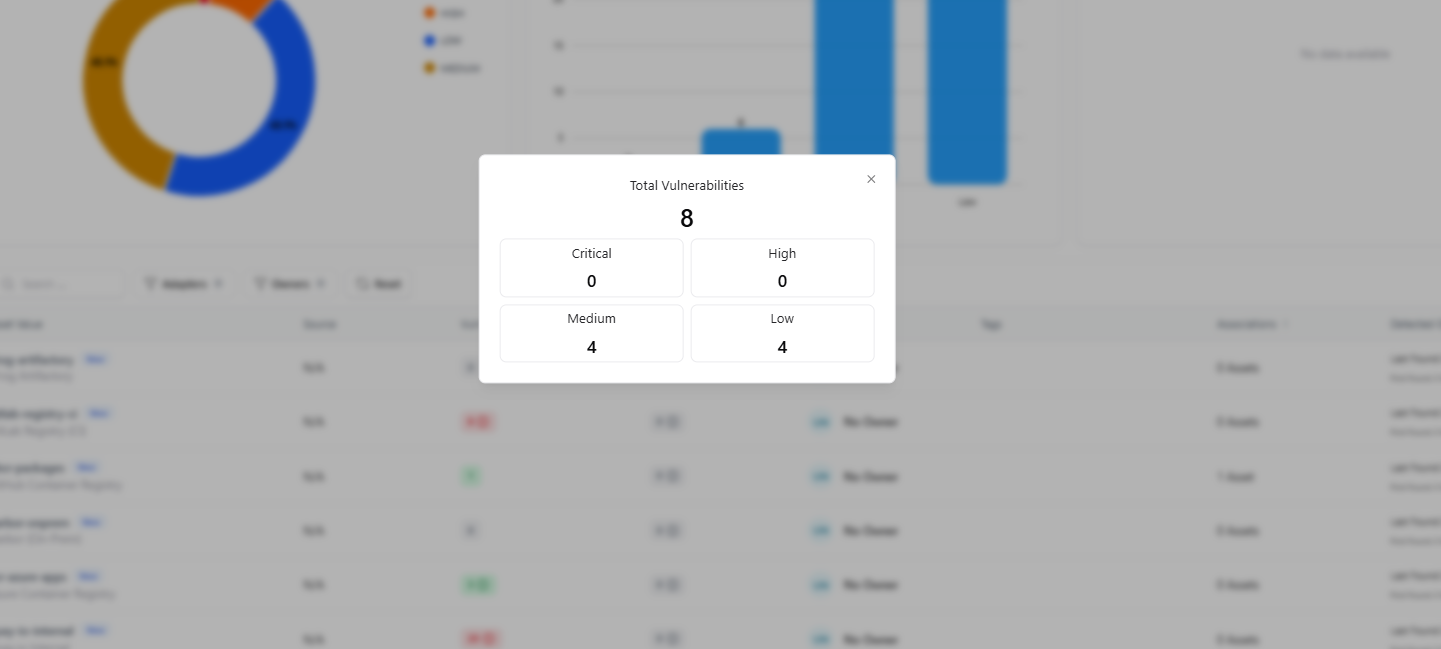
Vulnerability Summary
This modal provides:- Total Vulnerabilities Count
- Critical Vulnerabilities
- High Vulnerabilities
- Medium Vulnerabilities
- Low Vulnerabilities
Registry Asset View
Selecting a specific registry opens its Registry Asset View, providing deep visibility into that individual registry.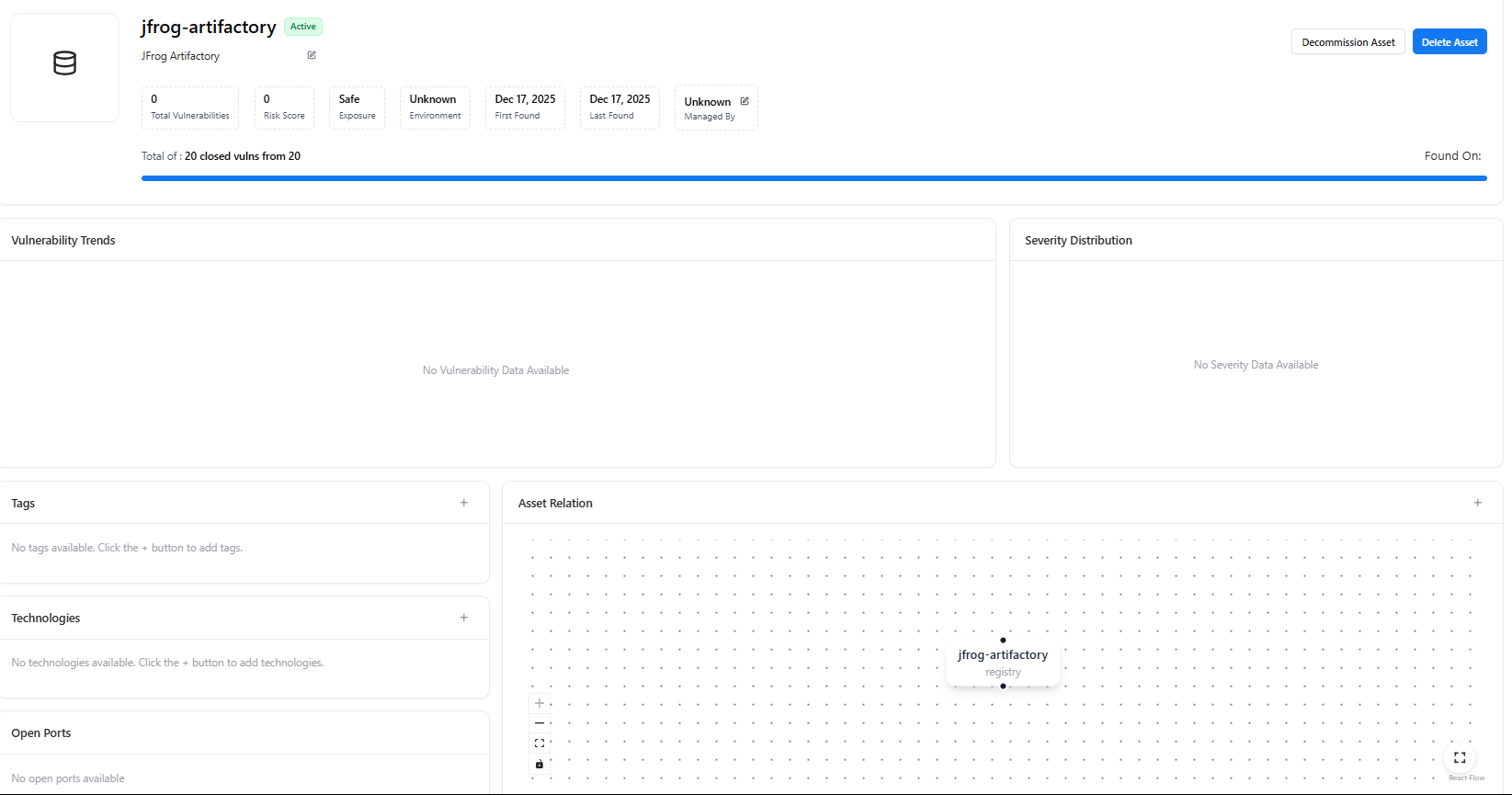
Registry Summary Panel
Each registry asset includes:- Registry Name & Status (Active / Inactive)
- Total Vulnerabilities
- Risk Score
- Exposure Status (Safe / Exposed)
- Environment
- First Found / Last Found
- Managed By
- Decommission Asset
- Delete Asset
Registry Insights
Within the asset view, AIM provides:- Vulnerability Trends — Historical vulnerability data (if available)
- Severity Distribution — Severity breakdown for the registry
- Tags — Classification labels
- Technologies — Detected technologies (when available)
- Asset Relations Graph — Visual mapping of how the registry connects to:
- Images
- Applications
- CI/CD pipelines
- Other AIM assets
Explore Live Demo
Explore AIM Live — No Signup Needed
Instantly explore how Snapsec AIM discovers, enriches, and tracks registries and other assets in real time — all without creating an account.