Overview
The Workstation Directory provides a centralized dashboard of all employee-linked devices such as laptops, desktops, and virtual workstations discovered across the environment. This dashboard gives security and IT teams immediate visibility into device posture, vulnerability presence, exposure status, and ownership.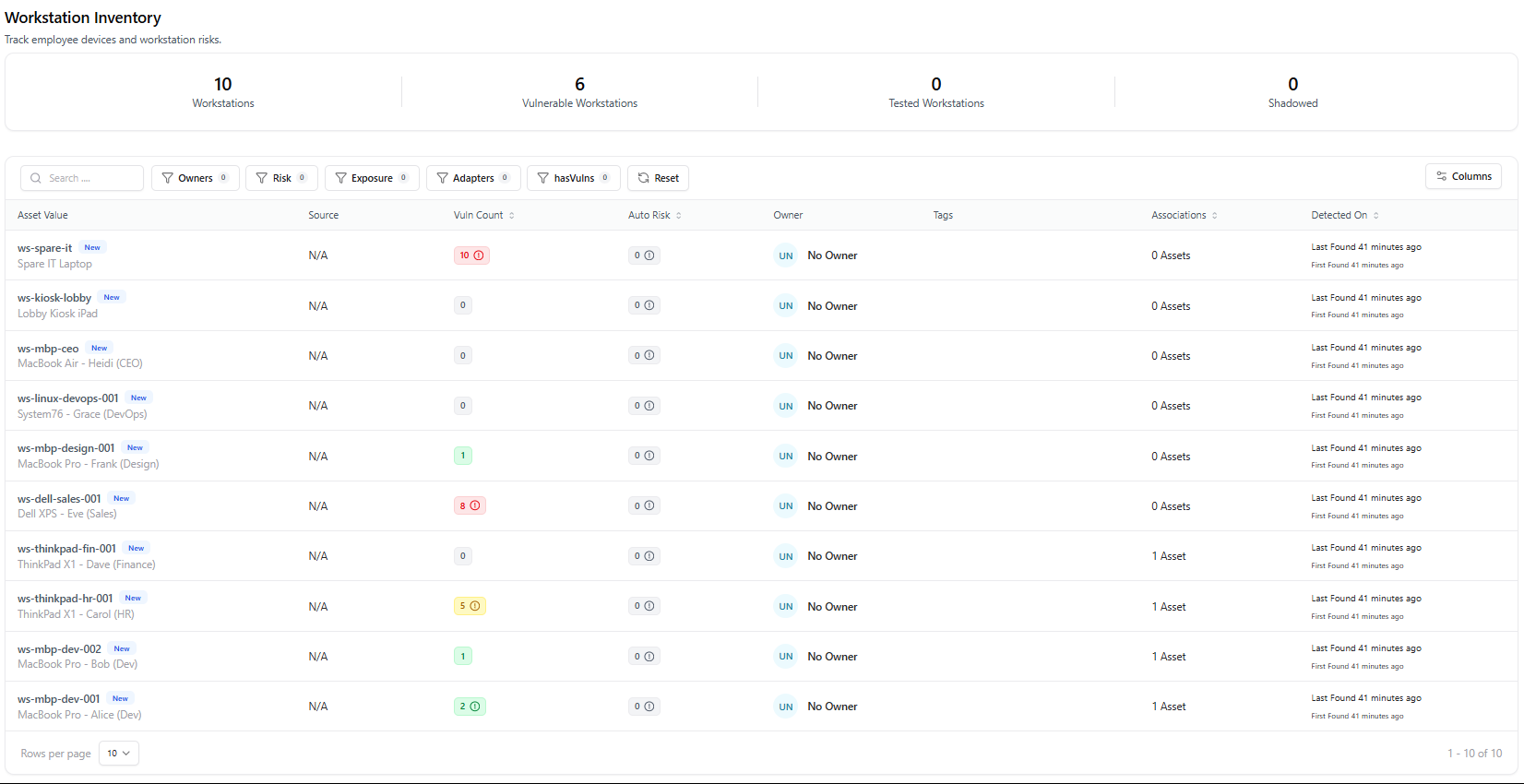
What the Dashboard Shows
- Total Workstations — All discovered employee devices
- Vulnerable Workstations — Devices with one or more security findings
- Exposure Status — Safe vs exposed workstations
- Risk Distribution — Risk scoring across devices
- Vulnerability Trends — High-level trend view (when data exists)
- Severity Distribution — Breakdown of Critical, High, Medium, and Low findings
- Search devices by name or identifier
- Filter by owner, risk, exposure, adapters, or vulnerability presence
- Sort devices by risk score, discovery date, or vulnerability count
Asset Risk Calculation
Each workstation includes a transparent and explainable Asset Risk Calculation, showing exactly how its final risk score is derived.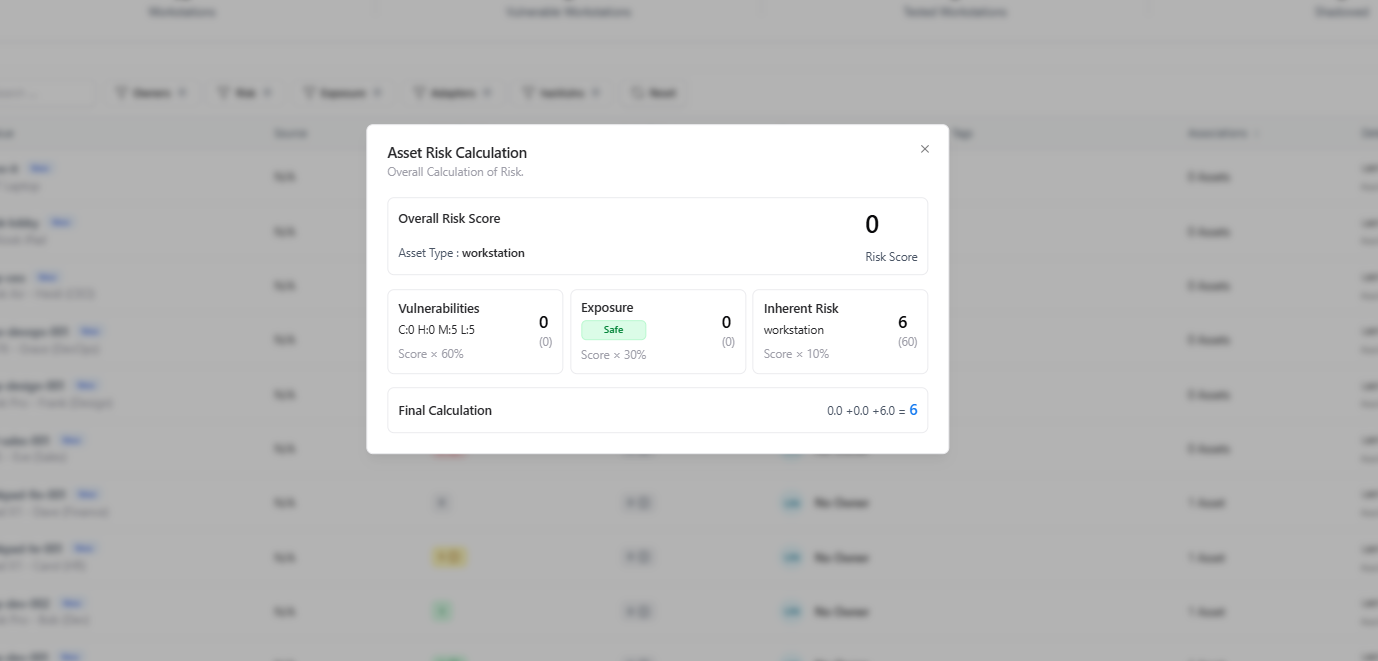
How Risk Is Calculated
AIM computes workstation risk using weighted components:-
Vulnerabilities (60%)
Based on severity counts:- Critical
- High
- Medium
- Low
-
Exposure (30%)
Whether the workstation is externally reachable or safely contained. -
Inherent Asset Risk (10%)
Baseline risk associated with the asset type (workstation, laptop, VM).
Final Risk Score
All components are combined into a final numerical risk score, giving teams:- Clear prioritization
- Consistent scoring across asset types
- Defensible risk justification for audits and reporting
Workstation Asset View (Inside a Workstation)
Clicking any workstation opens its Workstation Asset View, providing deep visibility into that specific device.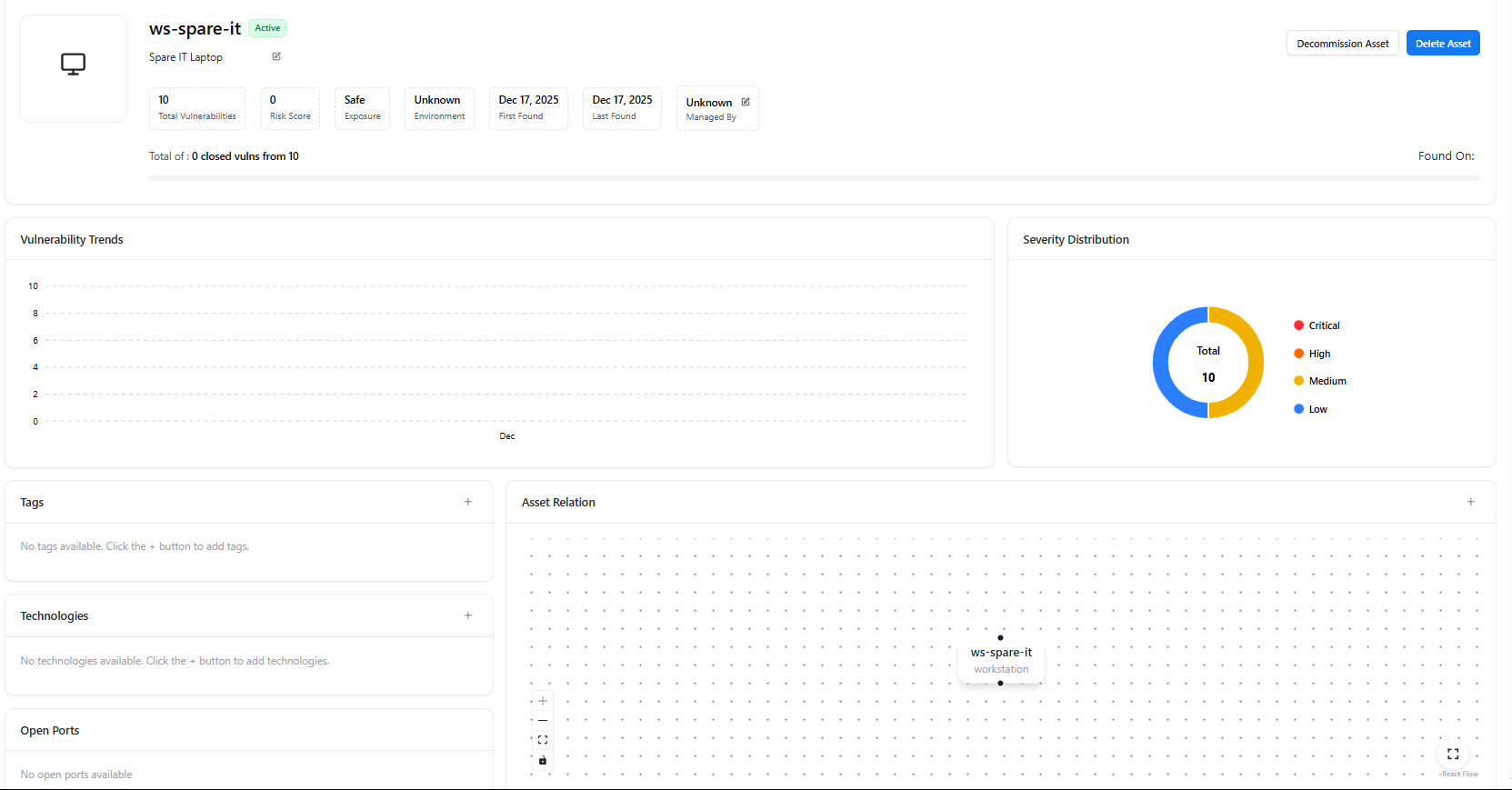
Workstation Summary Panel
Each workstation asset displays:- Device Name & Status (Active / Decommissioned)
- Total Vulnerabilities
- Risk Score
- Exposure Status
- Environment (Prod, Dev, Unknown)
- First Found / Last Found
- Managed By (Owner or team)
- Decommission Asset
- Delete Asset
Workstation Insights
Within the asset view, teams can access:- Vulnerability Trends — Historical vulnerability changes
- Severity Distribution — Severity breakdown for findings
- Tags — Labels such as
workstation,laptop,employee-device - Technologies — Installed or detected technologies (if available)
- Asset Relations Graph — Visual mapping of relationships with:
- Employees
- Applications
- Repositories
- Certificates
- Other infrastructure assets
Explore Live Demo
Explore AIM Live — No Signup Needed
Instantly explore how Snapsec AIM discovers, enriches, and tracks workstations and other assets in real time — all without creating an account.