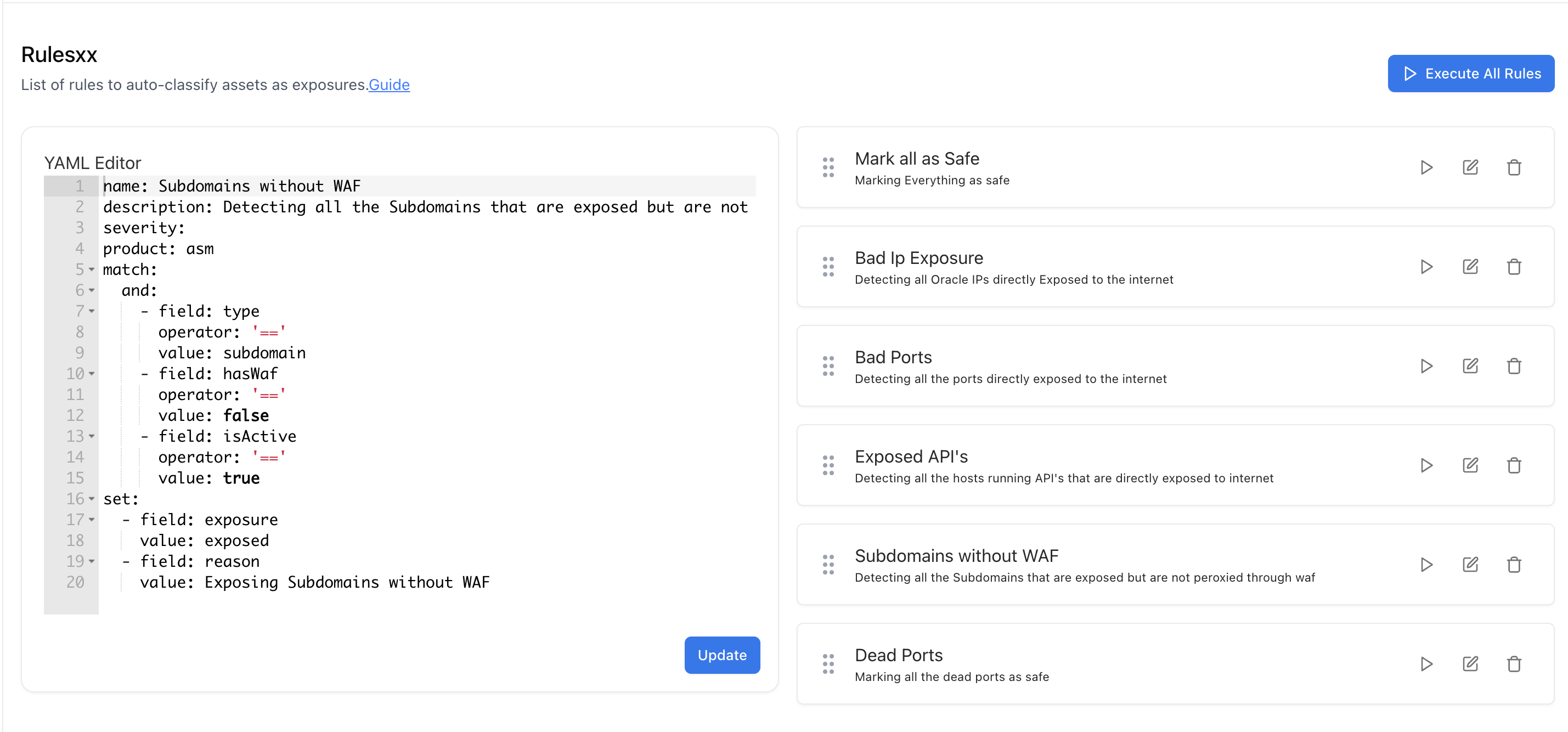
Overview
Exposure Rules use our YAML Rule Engine to translate human-readable policy into executable queries.Each rule inspects asset metadata (subdomains, IPs, ports, tech, certs, DNS, screenshots, etc.) and, when matched, marks the asset/exposure, assigns severity, and optionally sets attributes (e.g., category, ownerHint, runbookLink).
- Input: Discovered assets from ASM scans (Subdomains, IPs, Web Servers, Ports, DNS, Certificates, Technologies…).
- Logic: YAML rules (match + optional set).
- Output: Standardized Exposures in the Exposures module, ready for triage, dashboards, and reporting.
How it Works (Evaluation Cycle)
- Scan completes → assets are normalized & enriched.
- Rules execute in order (you can reorder; most specific first is recommended).
- If a rule’s
matchis satisfied:- An exposure is created/updated and fields in
setare applied (severity/category/notes/etc.). - The asset keeps the exposure tag for history & trend charts.
- An exposure is created/updated and fields in
- Conflicts: If multiple rules match, we merge
setfields; the highest severity wins.
The syntax and operators are the same as the YAML Rule Engine used across Suite. Full guide below.
YAML Rule Guide (quick-start)
Rules follow the same structure described in the Rule Engine docs you provided:Exampe Rules
Explore Live Demo
Explore ASM Live — No Signup Needed
Instantly explore how Snapsec Attack Surface Management (ASM) discovers external assets, identifies exposures, enriches attack surface data, and visualizes risk — all in real time, without creating an account.