Overview
The API Catalog provides a unified registry of every API endpoint discovered across your applications and services. It enables complete visibility into routes, methods, linked threats, metadata, and real-time behavioral insights — powering accurate threat modelling and secure API development.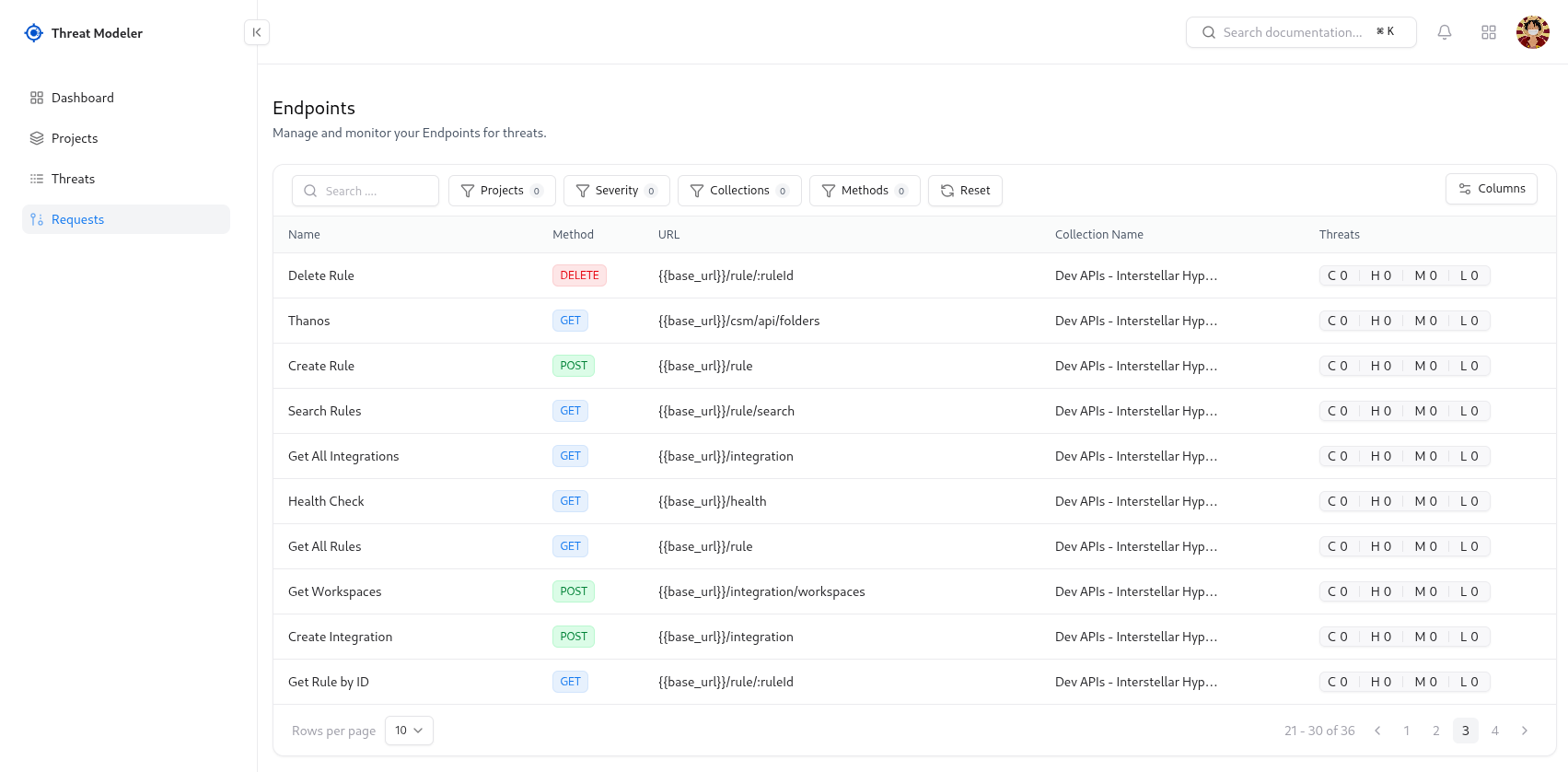
Overview
The API Catalog aggregates all endpoints detected through:- Postman collections
- Swagger/OpenAPI specifications
- Threat-generation scans
- Application imports
- Live traffic datasets (where applicable)
- Route path
- HTTP method
- Host/service association
- Threat count & severity
- Generation state
- Metadata & parameters
- Linked project
Key Metrics & Analytics
Total Endpoints
Shows the complete number of API endpoints discovered across all projects.
Endpoints With Threats
Highlights endpoints that have one or more threats associated with them.
High-Risk Routes
Shows the number of endpoints linked to Critical or High-severity threat patterns.
Endpoint Distribution
Visual breakdown of:- HTTP method usage
- Project grouping
- Endpoint complexity levels
- Threat density across routes
Search, Filters & Sorting
The powerful API filtering system lets analysts narrow down endpoints by:| Filter | Description |
|---|---|
| Method | GET, POST, PUT, DELETE, etc. |
| Threats | Filter by severity or count |
| Owner | Assigned engineering team |
| Path Contains | Partial route matching |
| Generation State | Generated, Pending, Failed |
| Tags | Custom metadata |
| Project | Associated application or service |
API Table Columns
| Column | Description |
|---|---|
| Route | API path including dynamic parameters |
| Method | HTTP verb for the endpoint |
| Host / Service | Linked backend service |
| Threat Count | Total threats mapped to this endpoint |
| State | Generation status (Generated, Pending, Skipped) |
| Owner | Assigned team or engineer |
| Tags | API-specific metadata |
| Detected On | First and last discovery timestamps |
Example Use Cases
Threat Modelling
Map threats to endpoints and visualize high-risk routes.
API Security Testing
Use endpoint catalog to drive automated scans and fuzzing.
Service Ownership
Assign owners to routes and track accountability.
API Governance
Maintain a clean, structured, and up-to-date API inventory.
Explore Live Demo
Explore Snapsec Live — No Signup Needed
Jump straight into the live environment and see how Snapsec unifies asset intelligence, threat detection, and vulnerability tracking — all in one dashboard.