Overview
The Object Storage dashboard provides a centralized view of all cloud storage buckets discovered across supported cloud providers such as AWS S3, Azure Blob Storage, and Google Cloud Storage (GCS). This dashboard helps security and cloud teams quickly understand storage exposure, ownership gaps, and potential risk signals.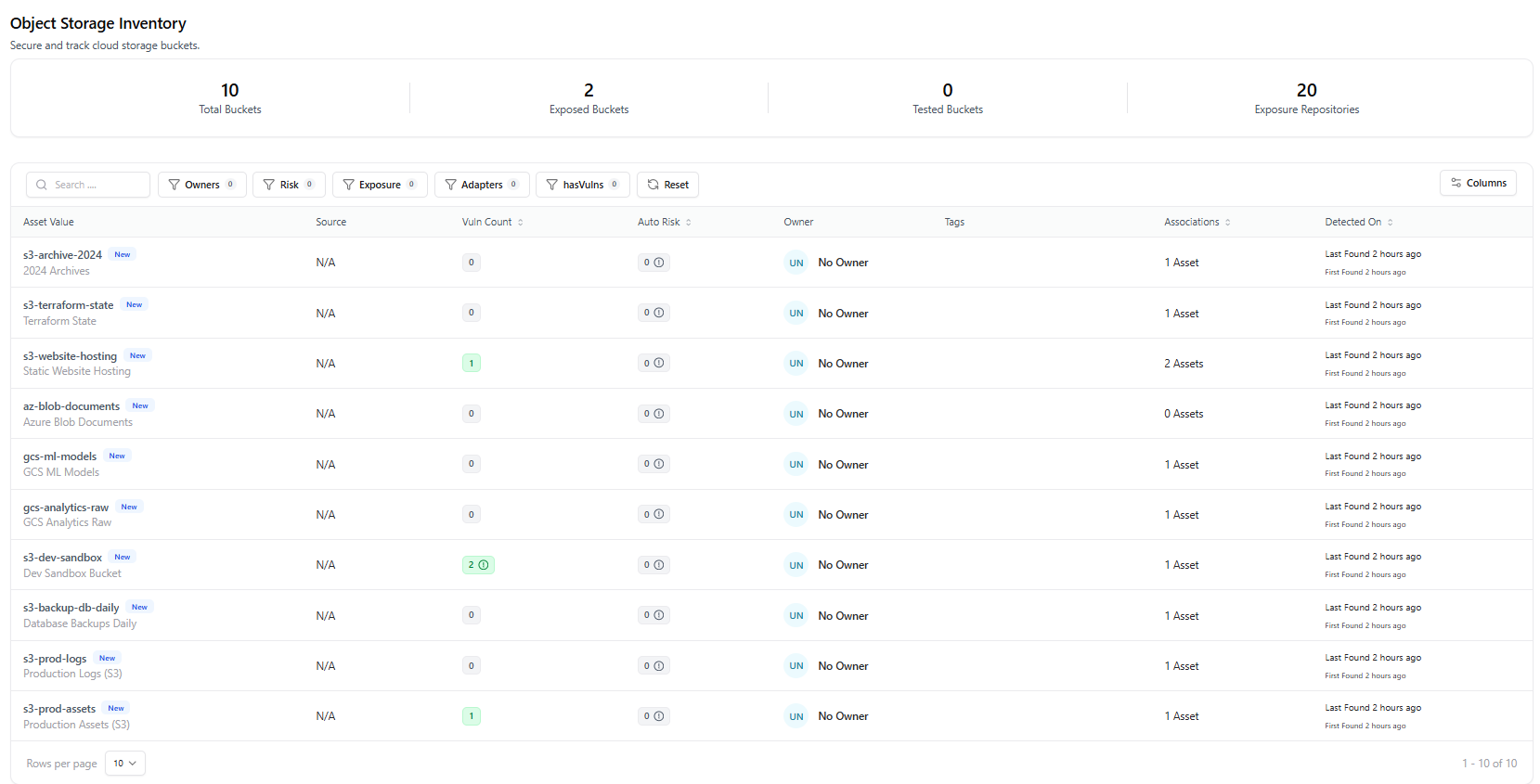
What the Dashboard Shows
- Total Buckets — Total number of discovered object storage buckets
- Exposed Buckets — Buckets that may be publicly accessible or misconfigured
- Tested Buckets — Buckets assessed through connected security scanners
- Exposure Repositories — Linked assets or services interacting with buckets
- Search buckets by name
- Filter by Owner, Risk, Exposure, Adapters, or Vulnerability presence
- View vulnerability count, auto risk score, and associations
- Track first found and last found timestamps
Object Storage Asset View (Inside a Bucket)
Selecting a bucket opens its Object Storage Asset View, offering detailed visibility into configuration, risk posture, and relationships.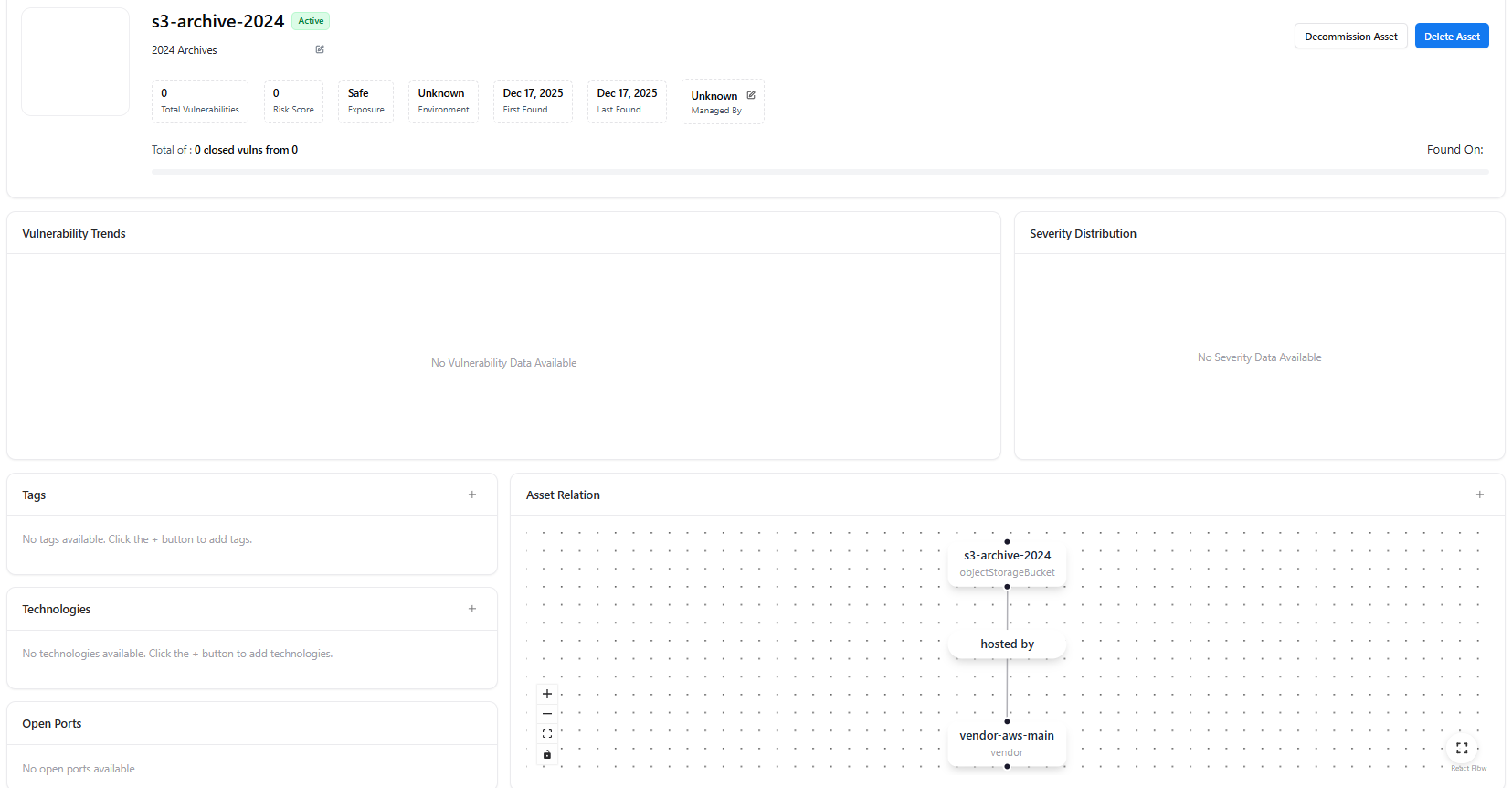
Bucket Summary Panel
Each object storage asset includes:- Bucket Name & Status (Active / Inactive)
- Total Vulnerabilities
- Risk Score
- Exposure Status (Safe / Exposed)
- Environment (Prod, Dev, Unknown)
- First Found / Last Found
- Managed By (Owner or team)
- Decommission Asset
- Delete Asset
Bucket Insights
Within the asset view, AIM provides:- Vulnerability Trends — Historical vulnerability data (when available)
- Severity Distribution — Breakdown of detected issues by severity
- Tags — Classification labels for governance and filtering
- Technologies — Related services or storage technologies
- Asset Relations Graph — Visual mapping showing how the bucket is:
- Hosted by cloud vendors
- Connected to applications or services
- Related to other assets in the environment
Example Use Cases
Cloud Exposure Management
Identify publicly exposed or misconfigured storage buckets before data leakage occurs.
Data Security Governance
Maintain visibility into where critical data is stored and who owns each bucket.
Incident Investigation
Quickly trace compromised buckets and understand their relationships with other assets.
Explore Live Demo
Explore AIM Live — No Signup Needed
Instantly explore how Snapsec AIM discovers, enriches, and tracks object storage assets in real time — all without creating an account.