Overview
The Employee Inventory dashboard provides a high-level view of all employee-linked identities discovered across your organization.It helps security and IAM teams understand workforce exposure, vendor usage, and identity distribution at a glance.
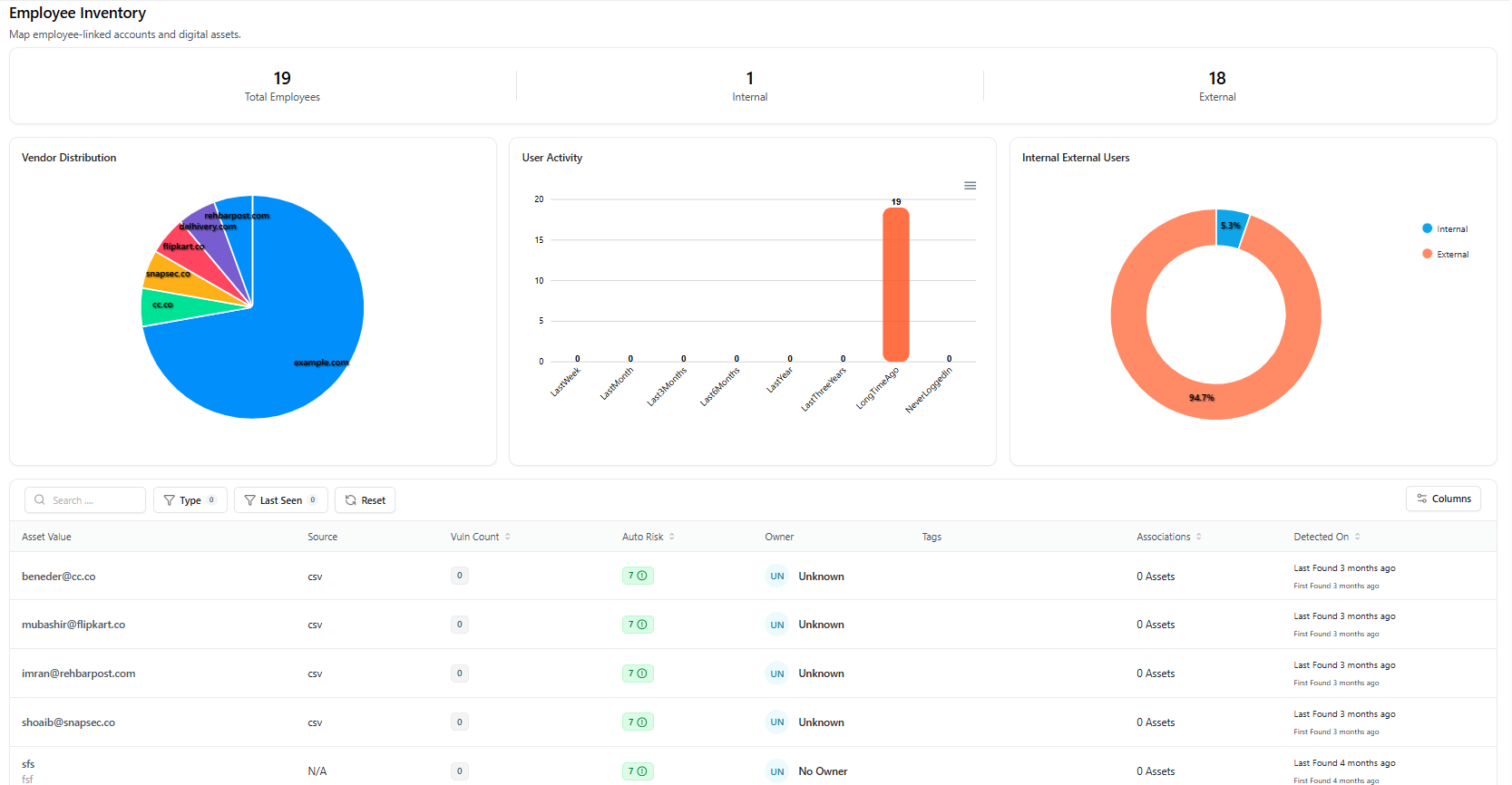
What the Dashboard Shows
- Total Employees — Count of all discovered employee identities
- Internal Employees — Identities using organization-managed domains
- External Employees — Vendor, contractor, or partner identities
Visual Insights Available
- Vendor Distribution — Breakdown of identity providers and associated domains
- User Activity — Login activity timelines (inactive, long-dormant, recently active)
- Internal vs External Users — Proportional view of workforce composition
Employee Inventory Table
Each row represents a discovered employee identity with:- Employee Email / Identity
- Source (CSV, vendor, or integration)
- Vulnerability Count
- Auto Risk Score
- Owner
- Tags
- Asset Associations
- Detection Timeline
Employee Asset View
Clicking an employee opens the Employee Asset Detail View, providing full visibility into that identity’s risk, activity, and relationships.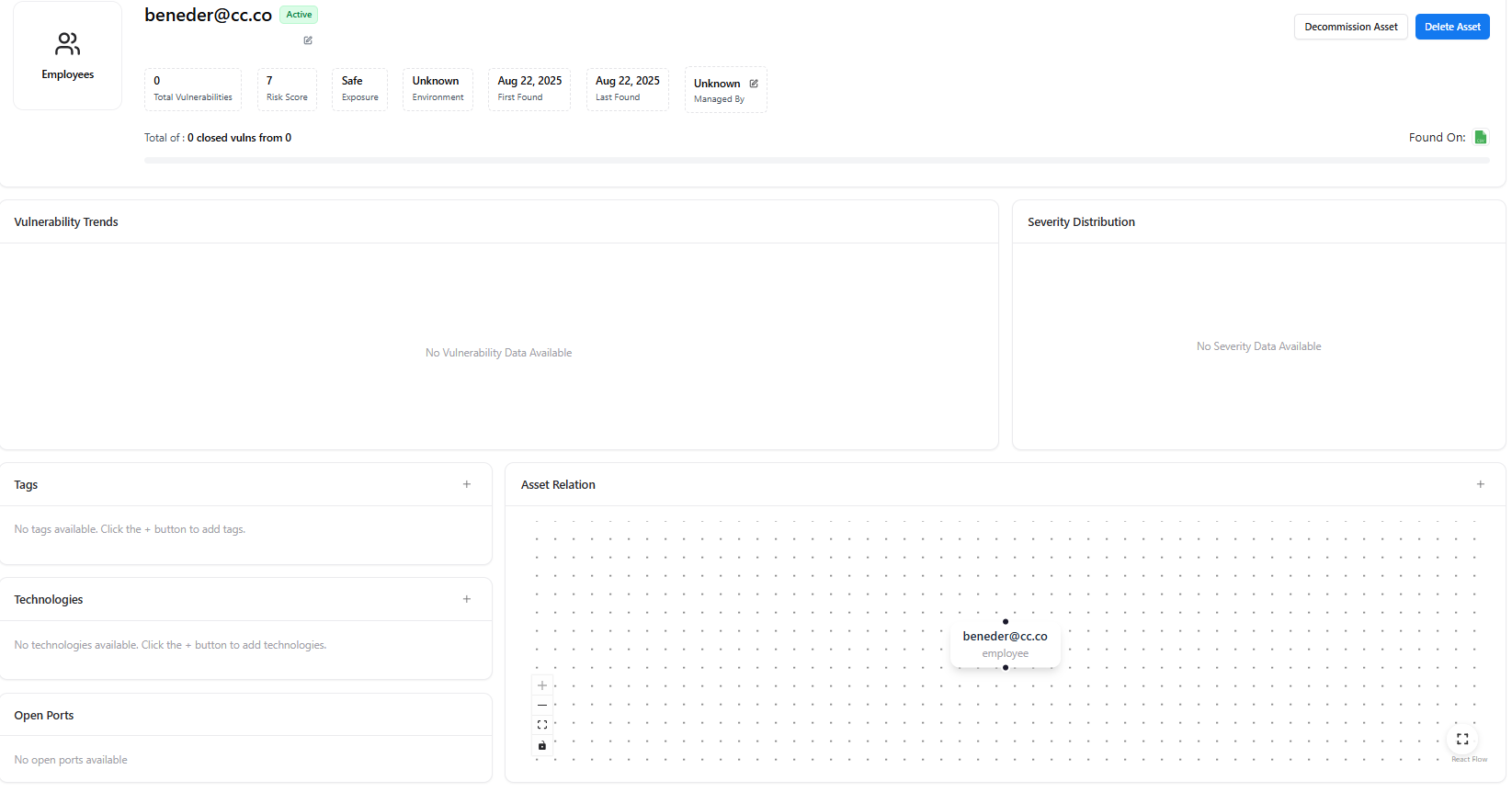
Employee Summary
Each employee asset displays:- Identity Value (email or username)
- Status (Active / Decommissioned)
- Total Vulnerabilities
- Risk Score
- Exposure Status
- Environment
- First Found / Last Found
- Managed By
Available Actions
- Decommission Asset — Mark the employee identity as inactive
- Delete Asset — Permanently remove the identity
Asset Intelligence Sections
- Vulnerability Trends — Historical vulnerability data (if available)
- Severity Distribution — Risk severity breakdown
- Tags — Classification labels (employee, internal, external, vendor)
- Technologies — Associated platforms (if detected)
- Open Ports — Network exposure (if applicable)
Asset Relation Graph
The Asset Relation graph visually maps how the employee identity connects to:- Applications
- Domains
- Other assets
Explore AIM Live — No Signup Needed
Instantly explore how Snapsec AIM discovers, enriches, and tracks employee identities and assets — all without creating an account.