Overview
The Threat Mitigation workspace helps teams validate, remediate, and verify threats effectively.It centralizes exploitation evidence, remediation steps, replayable request data, and lifecycle tracking — ensuring no threat is overlooked during mitigation.
Overview
Threat Mitigation provides a full-resolution workflow for each identified threat, combining:- Technical analysis
- Reproduction steps
- Remediation guidance
- Team ownership & collaboration
- Evidence attachments
- Lifecycle and activity history
Mitigation Workflow
Review Threat Details
Analyze the threat description, impacted endpoints, severity, CWE category, and attack scenario.
Verify Evidence
Inspect captured requests, payloads, parameters, and attached proof to validate the risk.
Apply Fix or Patch
Developers apply backend, permission, validation, or logic fixes to remove the vulnerability.
Mark as Ready for Verification
Once developers push the fix, the threat moves to Fix Verified for security review.
Key Features
Replayable Attack Evidence
Snapsec stores full request/response pairs so teams can reproduce attacks instantly.
AI-Assisted Remediation Guidance
Receive system-specific, endpoint-aware guidance on how to eliminate the threat.
Lifecycle Tracking
Every threat moves through states: Pending → Acknowledged → In Progress → Fixed → Verified.
Developer Collaboration
Add comments, attach files, assign owners, and track activity in a shared workspace.
Automatic Fix Verification
Automated re-testing ensures that patches correctly remove the vulnerability.
Audit & Compliance Ready
Full history of who fixed what, when, and how — ideal for audits and compliance.
Example Mitigation Insights
Injection payloads replayed against the patched endpoint showing sanitized responses.
Logic-flaw threat marked fixed after re-testing validates authorization checks.
Broken authentication threat closed after password-reset flow was redesigned.
CWE-639 (IDOR) threat resolved after implementing object-level access validation.
Search, Filtering & Sorting
Threat Mitigation supports advanced investigation controls:| Filter | Description |
|---|---|
| Severity | Critical, High, Medium, or Low threats |
| State | Acknowledged, In Progress, Fixed, Verified |
| Owner | Filter by responsible developer or analyst |
| Endpoint | API route or functionality impacted |
| CWE | Common Weakness Enumeration category |
| Confidence | Confidence level of the threat detection |
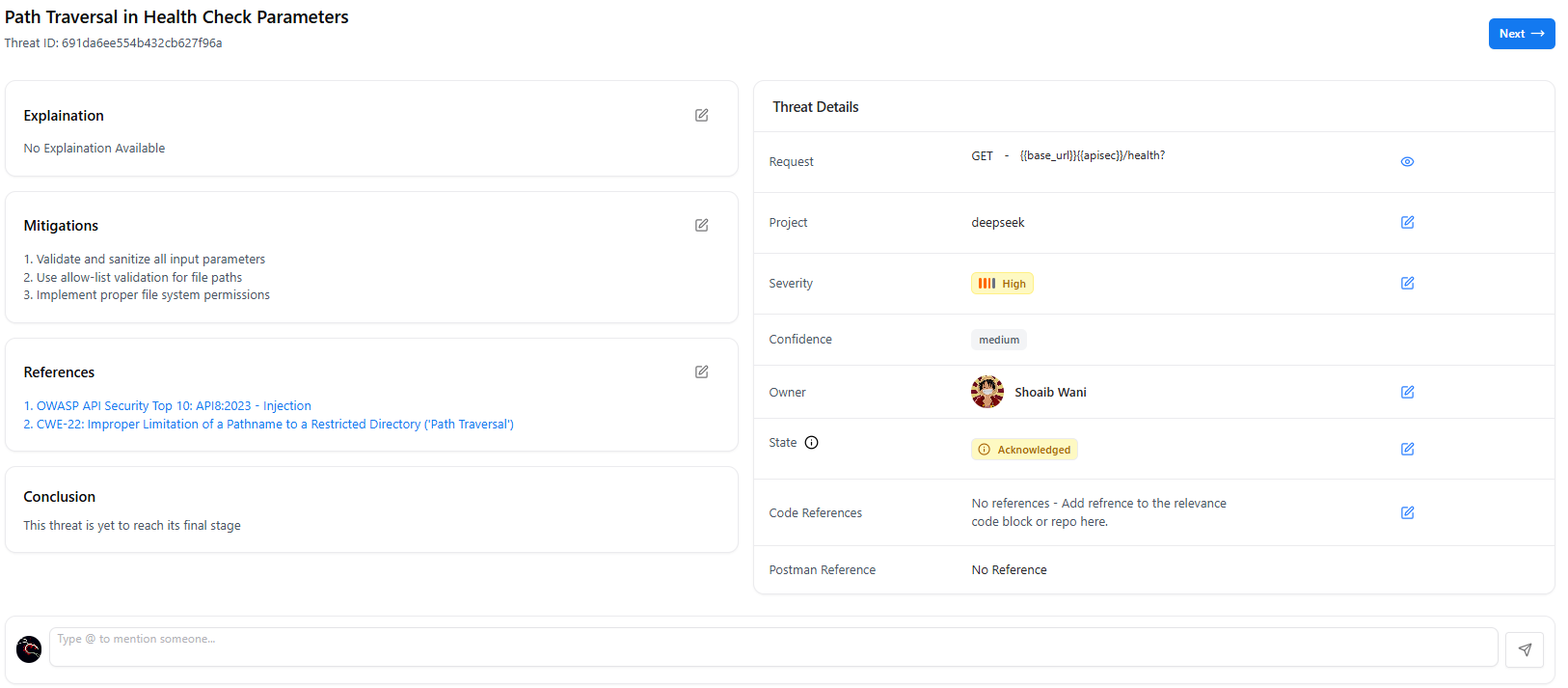
Full Threat View
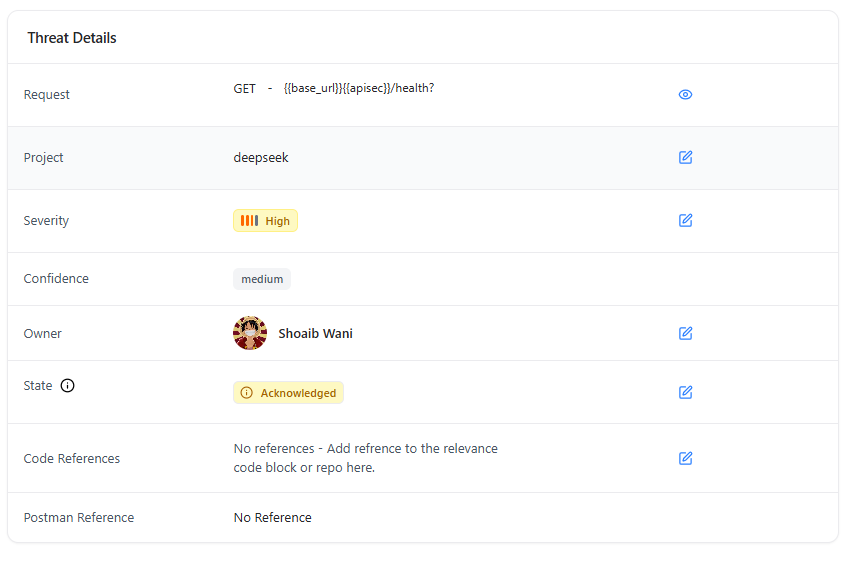
- Threat impact & explanation
- Request/response evidence
- CWE & severity
- Confidence score
- Endpoint details
- Owner & assigned team
- Activity history
- Comments & attachments
- Fix verification logs
Integrations
Snapsec Threat Mitigation integrates with:- VM for ticket syncing
- CI/CD for auto-verification
- GitHub / GitLab for linked pull requests
- Jira for task creation and tracking
Example Use Cases
Developer Fix Validation
Automatically validate whether a code fix truly removes the threat.
Security Review Workflows
Analysts confirm correctness, attach evidence, and move threats to Verified.
Team-Based Remediation
Assign threats to backend, frontend, or API teams with clear ownership.
Compliance Evidence
Export complete mitigation trails for SOC2, PCI, and internal audits.
Explore Live Demo
Explore Snapsec Live — No Signup Needed
Jump straight into the live environment and see how Snapsec unifies asset intelligence, threat detection, and vulnerability tracking — all in one dashboard.