Overview
The Vulnerabilities section provides a centralized view of all findings discovered across your scanned applications.It allows analysts to filter, investigate, and manage vulnerabilities by severity, scan source, suppression status, and more — ensuring complete visibility of application security risks.
Overview
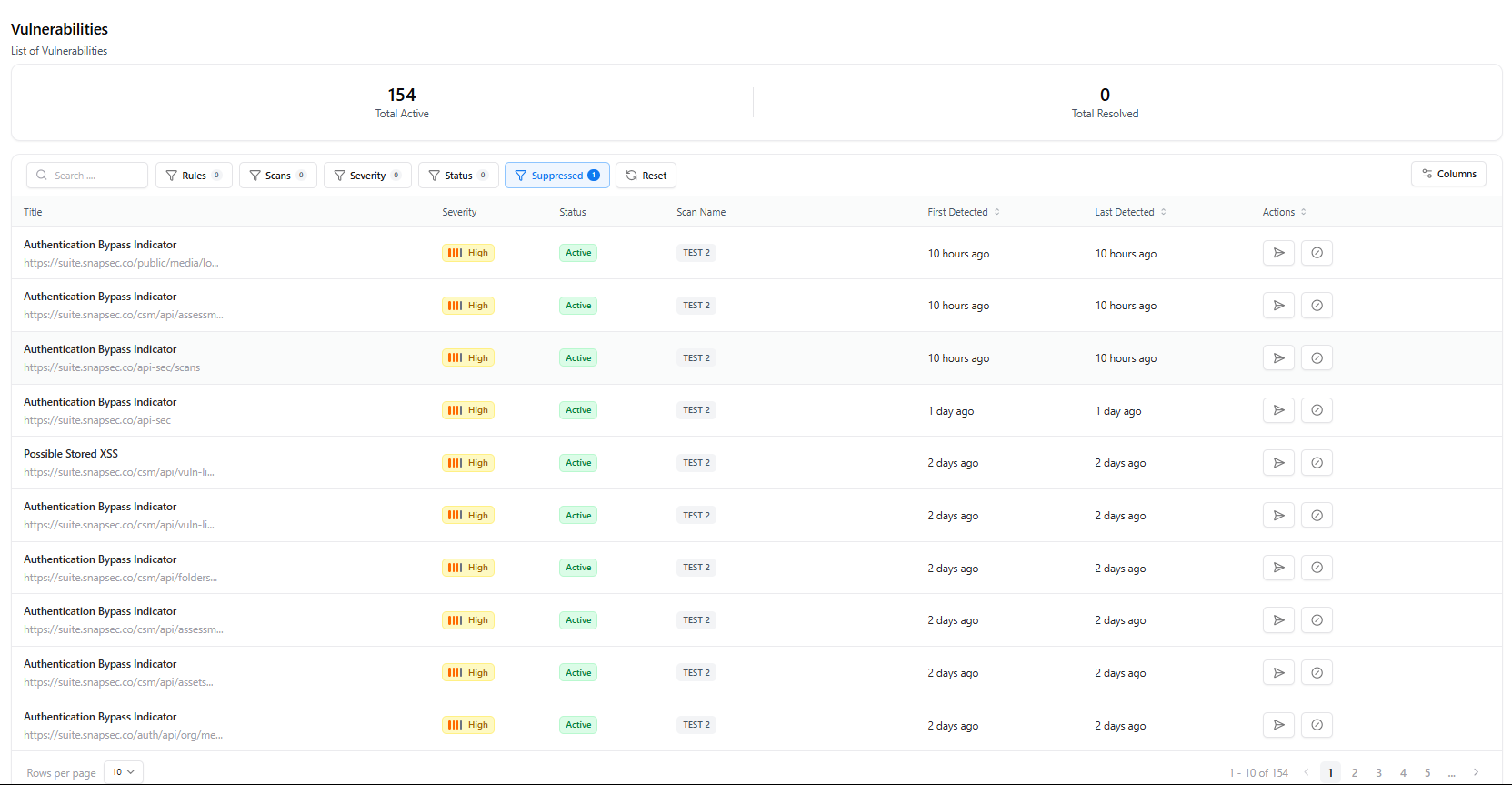
The Vulnerabilities module aggregates every issue detected across all WAS scans and presents:- Total active vulnerabilities
- Total resolved vulnerabilities
- Severity distribution
- Recent scan detections
- Suppressed vs. active vulnerability counts
- Full vulnerability listing with sorting, filtering, and triage actions
Key Metrics
Total Active
Displays the number of unresolved vulnerabilities currently open.
Total Resolved
Shows how many findings have been marked as resolved.
Suppressed
Count of findings manually suppressed or programmatically muted.
Filters & Search
The Vulnerabilities table supports deep filtering to quickly locate findings of interest:Filter by Severity
Narrow results to Critical, High, Medium, Low, or Informational.
Filter by Scan Source
View findings tied to specific scans or rescans.
Filter by Status
Switch between Active, Resolved, or Suppressed issues.
- Rule Type
- Request/Endpoint
- Detection timeframe
- Workspace or project context
Vulnerability Table
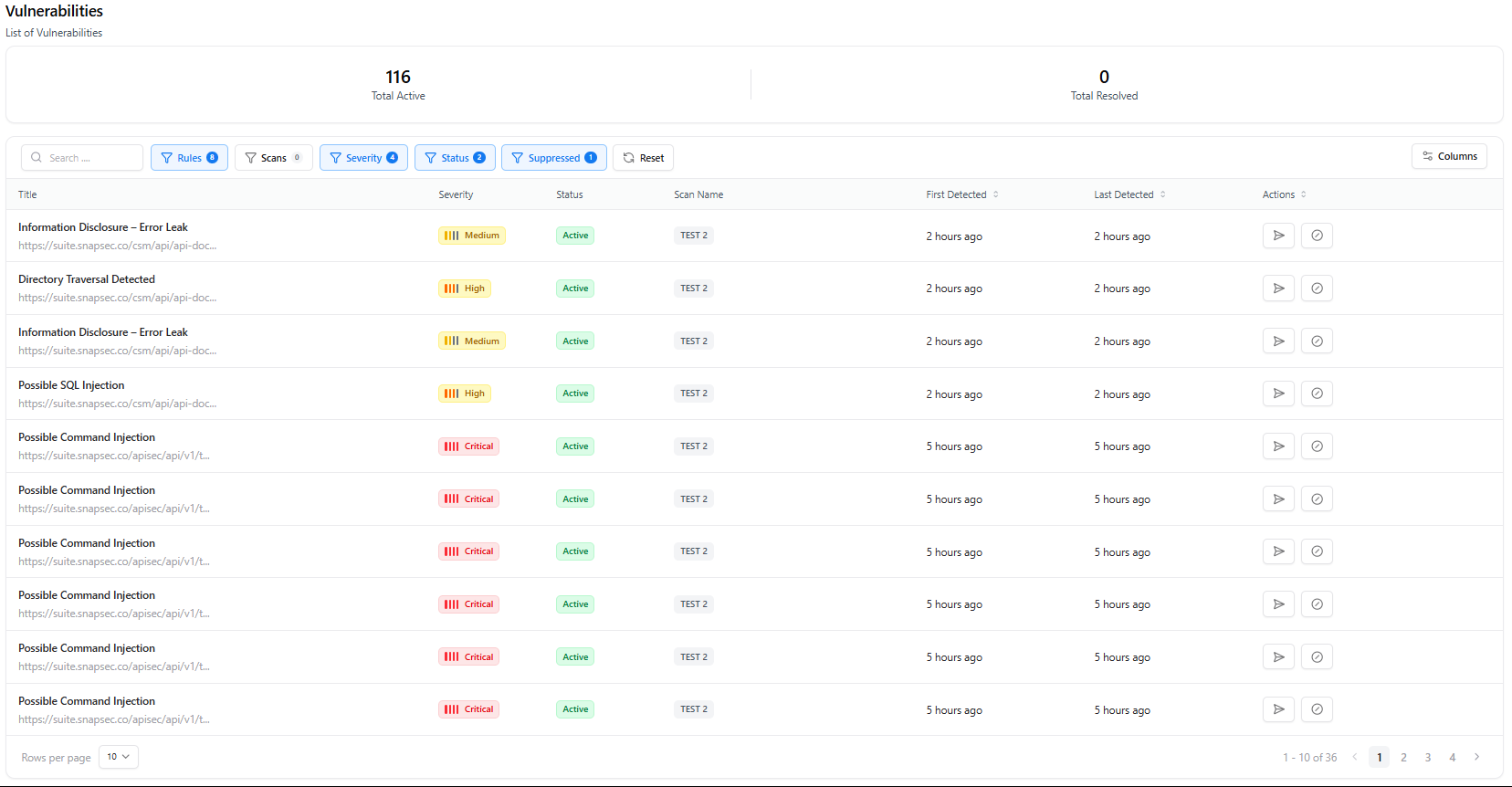
- Title — Name of the vulnerability
- Severity — Risk classification
- Status — Active, suppressed, or resolved
- Scan Name — Which project/scan identified it
- Timestamps — First detected & last detected
- Actions — Drill-down, suppress, resolve
Vulnerability Details Page
When clicking a vulnerability row, WAS provides an in-depth view including:🔍 Technical Details
- Description of the issue
- Impact assessment
- CWE mapping
- Evidence from request/response logs
- Reproduction steps
🛠 Recommended Fixes
- Framework-specific remediation guidance
- Secure coding patterns
- Validation, authentication, or sanitization strategies
📊 Affected Endpoints
- Each endpoint where the vulnerability was detected
- Associated request methods
- Count of occurrences
🚦 Status & Workflow
- Mark as Resolved
- Mark as False Positive
- Suppress with optional expiration
- View historical detection timeline
Bulk Actions
Analysts can take actions at scale:Bulk Suppress
Hide multiple vulnerabilities at once from dashboards and reporting.
Bulk Resolve
Mark multiple findings as resolved for program tracking.
Best Practices
Prioritize by Severity
Address Critical and High findings promptly to reduce attack surface.
Review Detection Trends
Compare first/last detection timestamps to identify recurring issues.
Use Suppression Wisely
Suppress only intentional behavior or accepted risks.
Investigate Endpoint Clusters
Multiple vulnerabilities on the same endpoint often indicate deeper flaws.
Explore Live Demo
Explore Snapsec Live — No Signup Needed
Jump straight into the live environment and see how Snapsec unifies asset intelligence, threat detection, and vulnerability tracking — all in one dashboard.