Overview
The Repositories Catalog provides a centralized dashboard showing all code repositories discovered across connected Git platforms such as GitHub, GitLab, or Bitbucket. This dashboard helps security and engineering teams understand repository posture at a glance — including activity, archive status, ownership, and risk.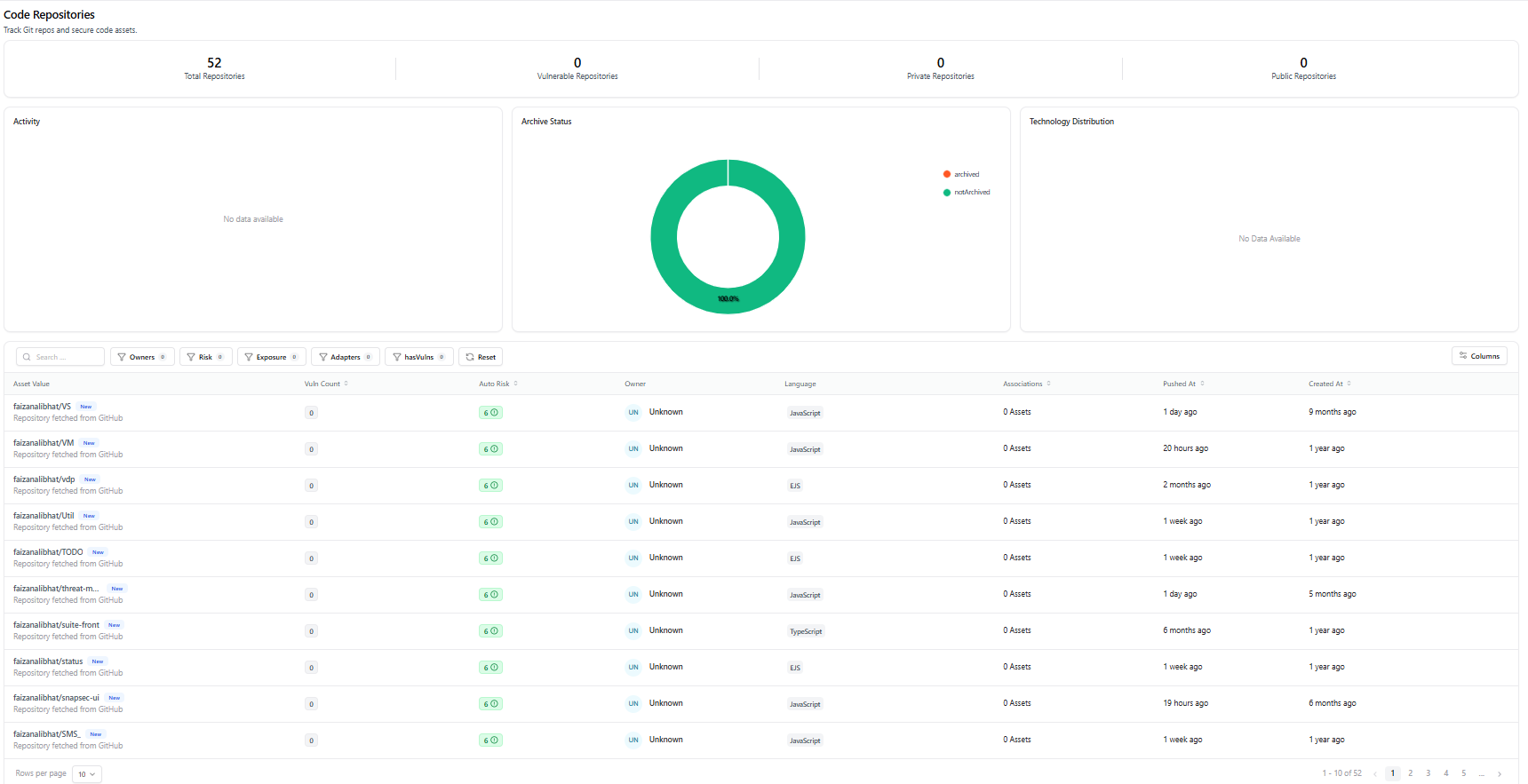
What the Dashboard Shows
- Total Repositories — Complete count of repositories discovered
- Vulnerable Repositories — Repositories linked to security findings
- Private Repositories — Internal or restricted repositories
- Public Repositories — Internet-facing repositories
- Activity Panel — Repository update or commit activity
- Archive Status — Archived vs active repositories
- Technology Distribution — Languages and tech stacks used (when available)
- Search repositories by name
- Filter by owner, risk, exposure, adapters, or vulnerability presence
- Sort by activity, creation date, or risk score
Repository Asset View (Inside a Repository)
Clicking any repository opens its Repository Asset View, providing deep visibility into that specific codebase.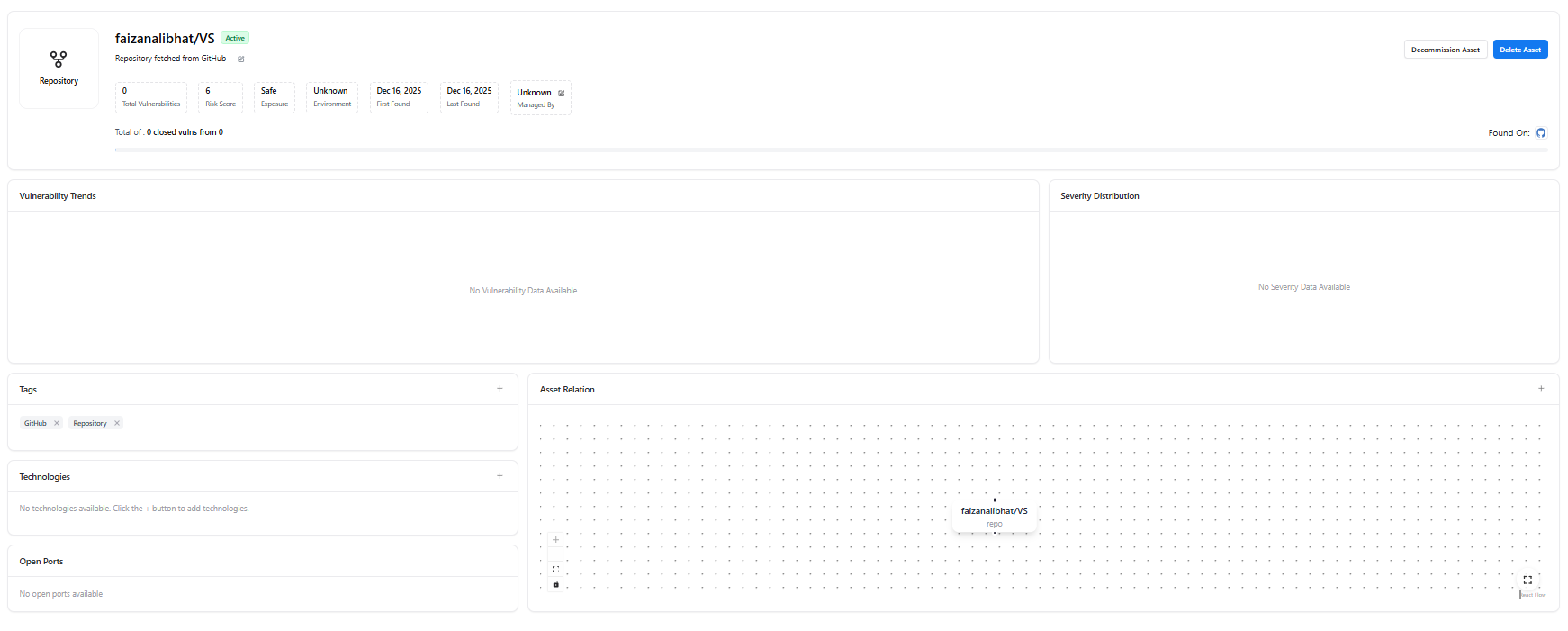
Repository Summary Panel
Each repository asset includes:- Repository Name & Status (Active / Inactive)
- Total Vulnerabilities
- Risk Score
- Exposure Status (Safe / Exposed)
- Environment (Prod, Dev, Unknown)
- First Found / Last Found
- Managed By (Owner or team)
- Decommission Asset
- Delete Asset
Repository Insights
Within the repository asset view, AIM provides:- Vulnerability Trends — Historical vulnerability changes (if available)
- Severity Distribution — Breakdown of vulnerability severity
- Tags — Labels such as
GitHub,Repository - Technologies — Detected languages or frameworks (when available)
- Asset Relations Graph — Visual mapping of how the repository connects to:
- Applications
- APIs
- Domains
- Other assets
Explore Live Demo
Explore AIM Live — No Signup Needed
Instantly explore how Snapsec AIM discovers, enriches, and tracks repositories and other assets in real time — all without creating an account.