Overview
The Application Inventory dashboard provides a centralized view of all applications discovered across your organization, including internal apps, APIs, and externally exposed services. It helps teams understand application exposure, vulnerability concentration, and ownership at a glance.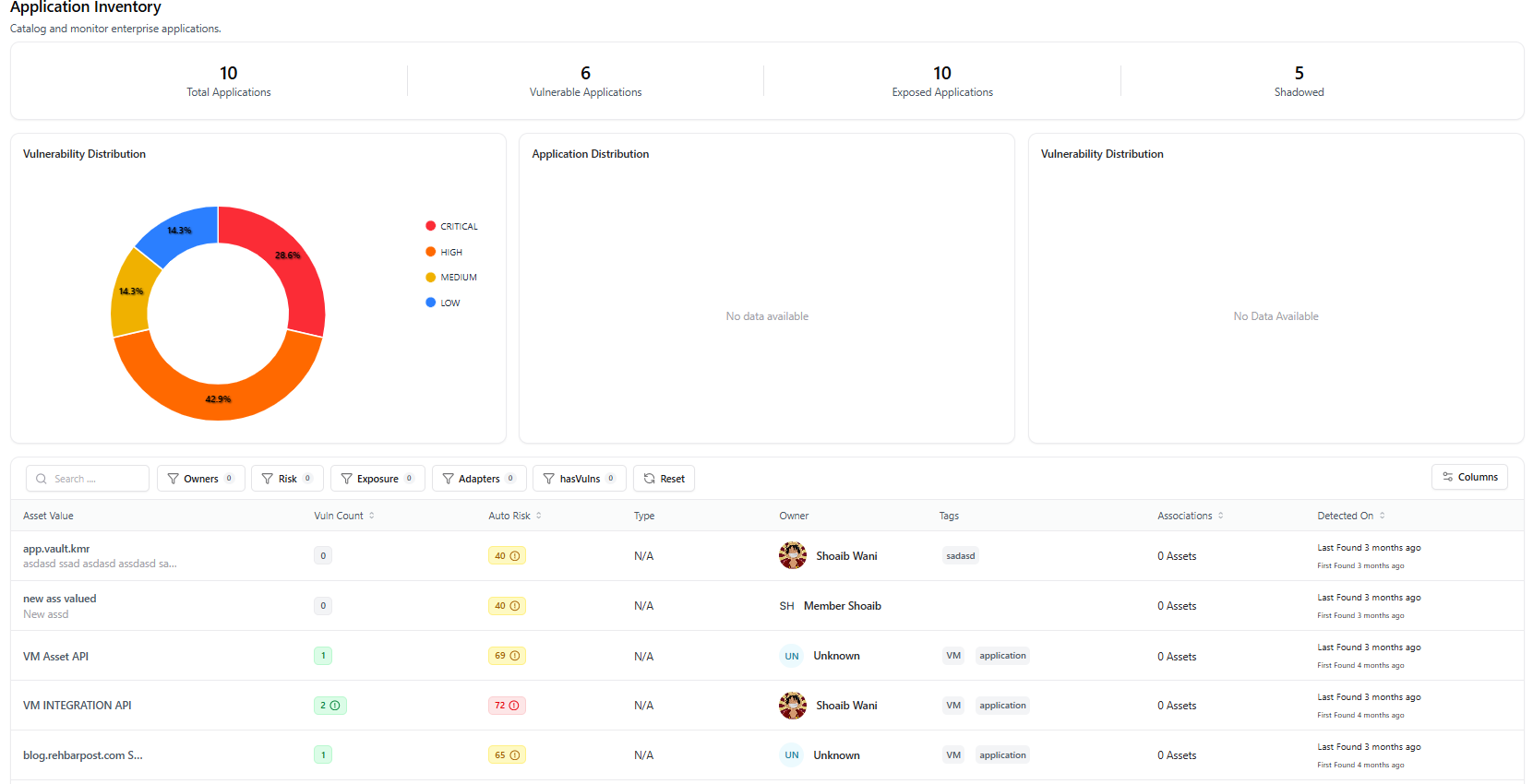
What the Dashboard Shows
- Total Applications discovered
- Vulnerable Applications with linked security findings
- Exposed Applications reachable from external networks
- Shadowed Applications without clear ownership or classification
Visual Insights
- Vulnerability Distribution by severity (Critical, High, Medium, Low)
- Application Distribution across environments
- Exposure-based breakdown for prioritization
Application Table
The table lists all discovered applications with key metadata:| Column | Description |
|---|---|
| Asset Value | Application name or identifier |
| Vuln Count | Number of linked vulnerabilities |
| Auto Risk | System-calculated risk score |
| Type | Application type |
| Owner | Assigned application owner |
| Tags | Labels such as vm, application |
| Associations | Linked assets |
| Detected On | First and last discovery timestamps |
Application Asset Detail View
Clicking an application opens its asset-level view, providing full context about that specific application.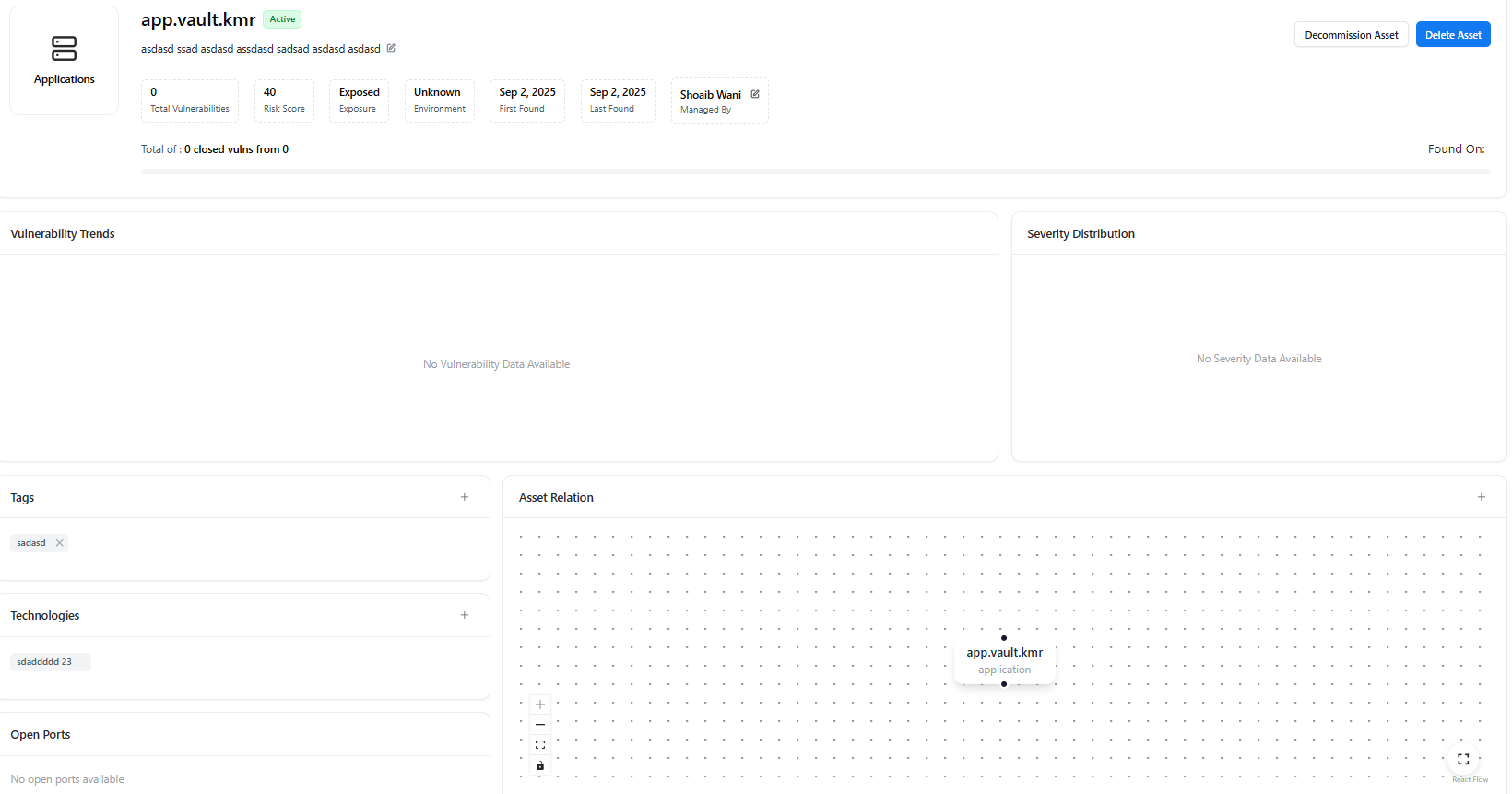
Application Summary
Each application asset includes:- Status (Active)
- Total Vulnerabilities
- Risk Score
- Exposure (Exposed or Safe)
- Environment
- First Found / Last Found
- Managed By (Owner)
- Decommission Asset
- Delete Asset
Vulnerability Insights
- Vulnerability trend panel
- Severity distribution panel
(Displayed when vulnerability data is available)
Metadata & Relationships
Inside an application asset, you can view and manage:- Tags for classification
- Technologies associated with the application
- Open Ports (if detected)
- Asset Relations Graph showing connections to:
- Domains
- APIs
- Certificates
- Other linked assets
Explore AIM Live — No Signup Needed
Instantly explore how Snapsec AIM discovers, enriches, and tracks applications and assets in real time — all without creating an account.