Overview
The Reports section consolidates your Attack Surface data — subdomains, ports, IPs, certificates, and exposures — into structured PDF deliverables for executives, auditors, and stakeholders.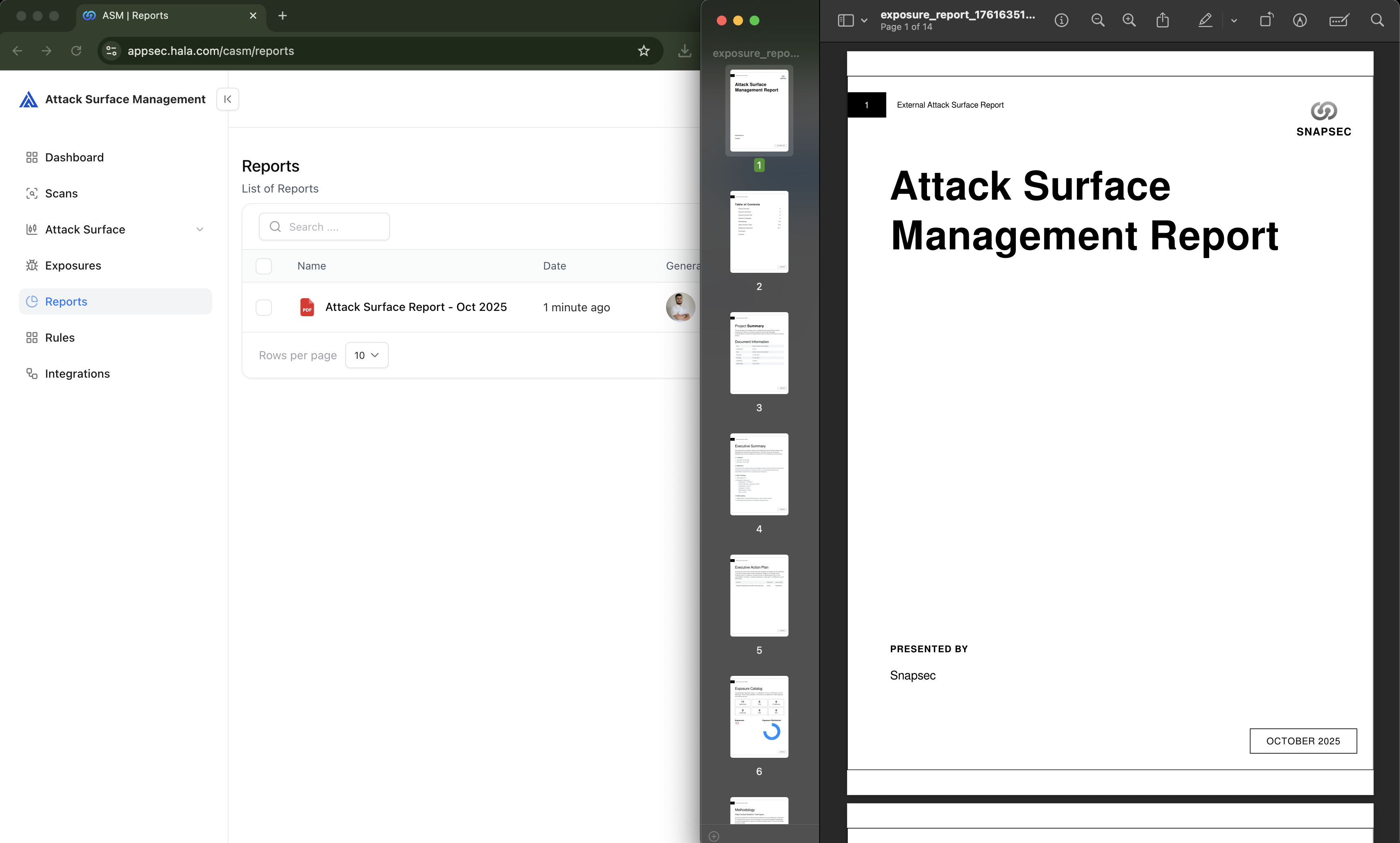
Overview
The Reports page in Attack Surface Management (ASM) allows you to generate and view detailed and compliance-ready security reports.Each report contains a full summary of your organization’s external attack surface, exposures, and actionable remediation steps. Generated reports are automatically archived for auditing and tracking purposes, ensuring transparency and repeatability for quarterly or ad-hoc assessments.
Key Capabilities
Generate PDF Reports
Export detailed Attack Surface summaries with one click using the Generate Report button.
Comprehensive Breakdown
Reports include project summary, exposure catalog, key findings, methodology, and tools used.
Audit Trail
Track when and by whom each report was generated, providing complete audit visibility.
Executive Insights
Each report contains executive-level summaries and recommendations to aid leadership decisions.
Report Structure
Each generated report follows a consistent and compliance-focused layout:| Section | Description |
|---|---|
| Project Summary | Outlines scope, objectives, and key dates. |
| Executive Summary | High-level overview of findings, exposure counts, and priorities. |
| Executive Action Plan | A clear roadmap for remediation priorities and accountability. |
| Exposure Catalogue | Summarizes all detected assets (subdomains, IPs, ports, etc.) with severity. |
| Methodology | Explains how assets and exposures were identified, including detection techniques. |
| Tools Used | Lists open-source and enterprise tools used for discovery (Subfinder, Nmap, CRT.sh, etc.). |
| Detailed Exposure Tables | Provides structured data for each exposure type (e.g., invalid certs, open ports). |
| Conclusion & Contacts | Closes with analyst notes, conclusions, and key contact details. |
Actions
Each report can be viewed, downloaded, or deleted directly from the dashboard.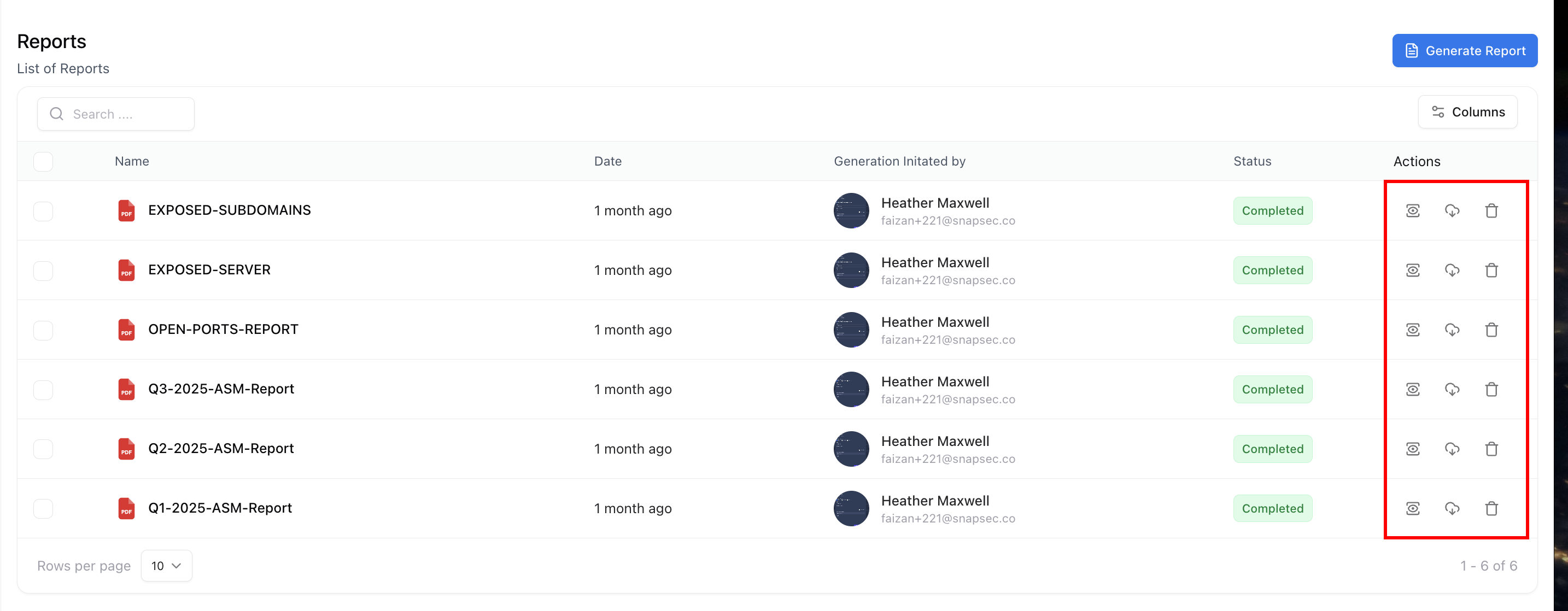
- 👁️ Preview — View the report inline before downloading.
- ⬇️ Download — Export a local PDF copy for archiving or sharing.
- 🗑️ Delete — Remove outdated or test reports to keep your workspace clean.
Workflow Example
- Click Generate Report after your latest ASM scan is complete.
- The platform compiles all assets, exposures, and analytics into a structured PDF.
- Review the document online or download it for internal distribution.
- Present the findings to your executive or compliance team for review.
Benefits
✅ Audit-ready documentation for security and compliance reviews✅ Automated and consistent report formatting
✅ Executive-ready summaries for leadership briefings
✅ Complete visibility into attack surface trends over time
Explore Live Demo
Explore ASM Live — No Signup Needed
Instantly explore how Snapsec Attack Surface Management (ASM) discovers external assets, identifies exposures, enriches attack surface data, and visualizes risk — all in real time, without creating an account.