Overview
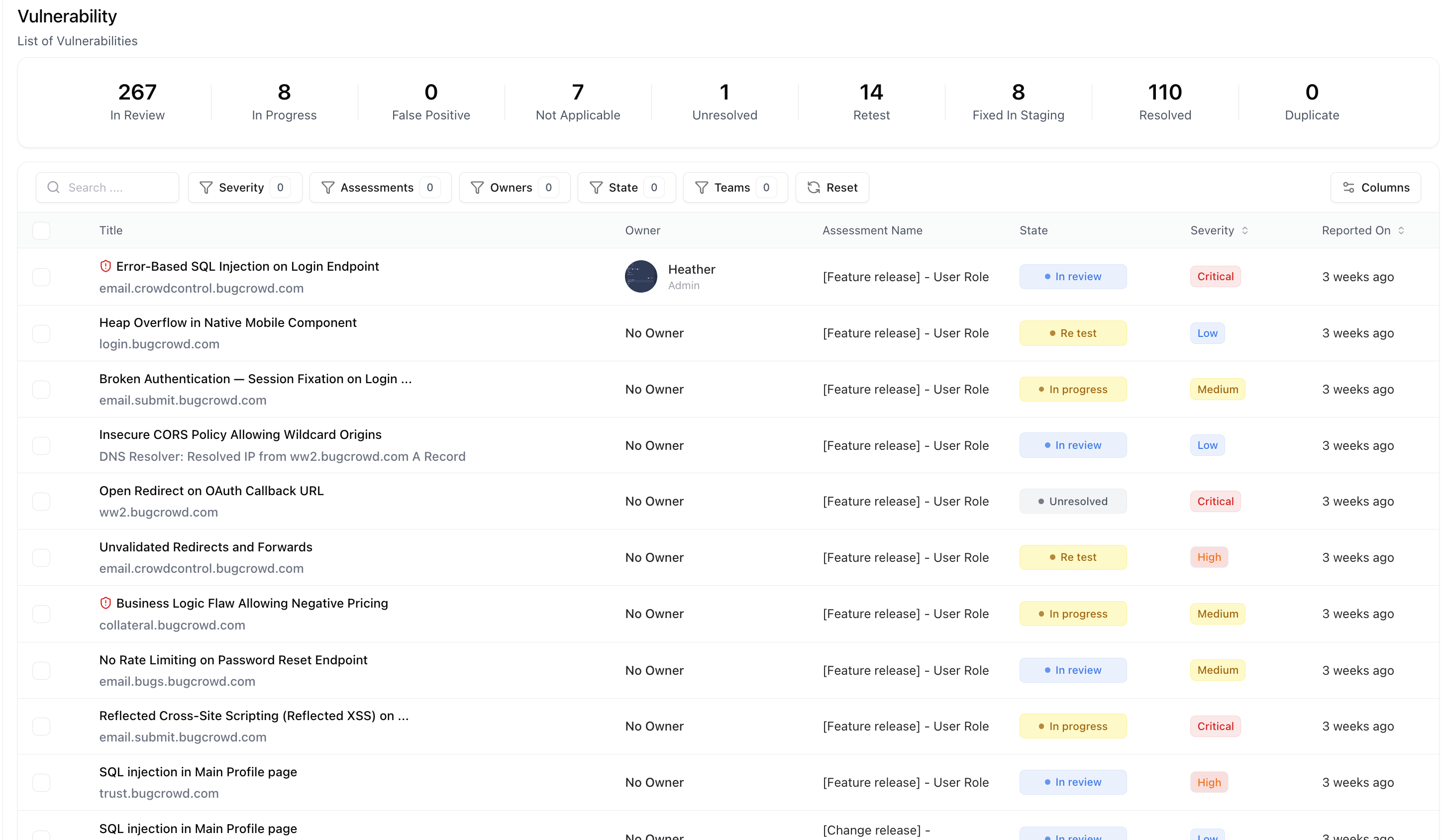
The Centralized Vulnerability List provides a single, comprehensive view of all vulnerabilities identified across your entire organization — from assessments, assets, and integrated scanners.It enables teams to track, prioritize, and manage vulnerabilities efficiently, all from one place. With intelligent filters, real-time states, and ownership visibility, this unified view removes the need to navigate multiple reports or dashboards. Every vulnerability is synced automatically from assessments and integrations, ensuring complete and current visibility.
Key Capabilities
Unified View
View all vulnerabilities from every source — assessments, integrations, and manual imports — in one consolidated table.
Real-Time Sync
Vulnerability data is continuously updated as new assessments complete or integrations refresh.
Advanced Filtering
Use granular filters to find vulnerabilities by severity, assessment, state, team, or owner.
Ownership & Assignment
See who owns each vulnerability and its current remediation progress.
Filtering and Search
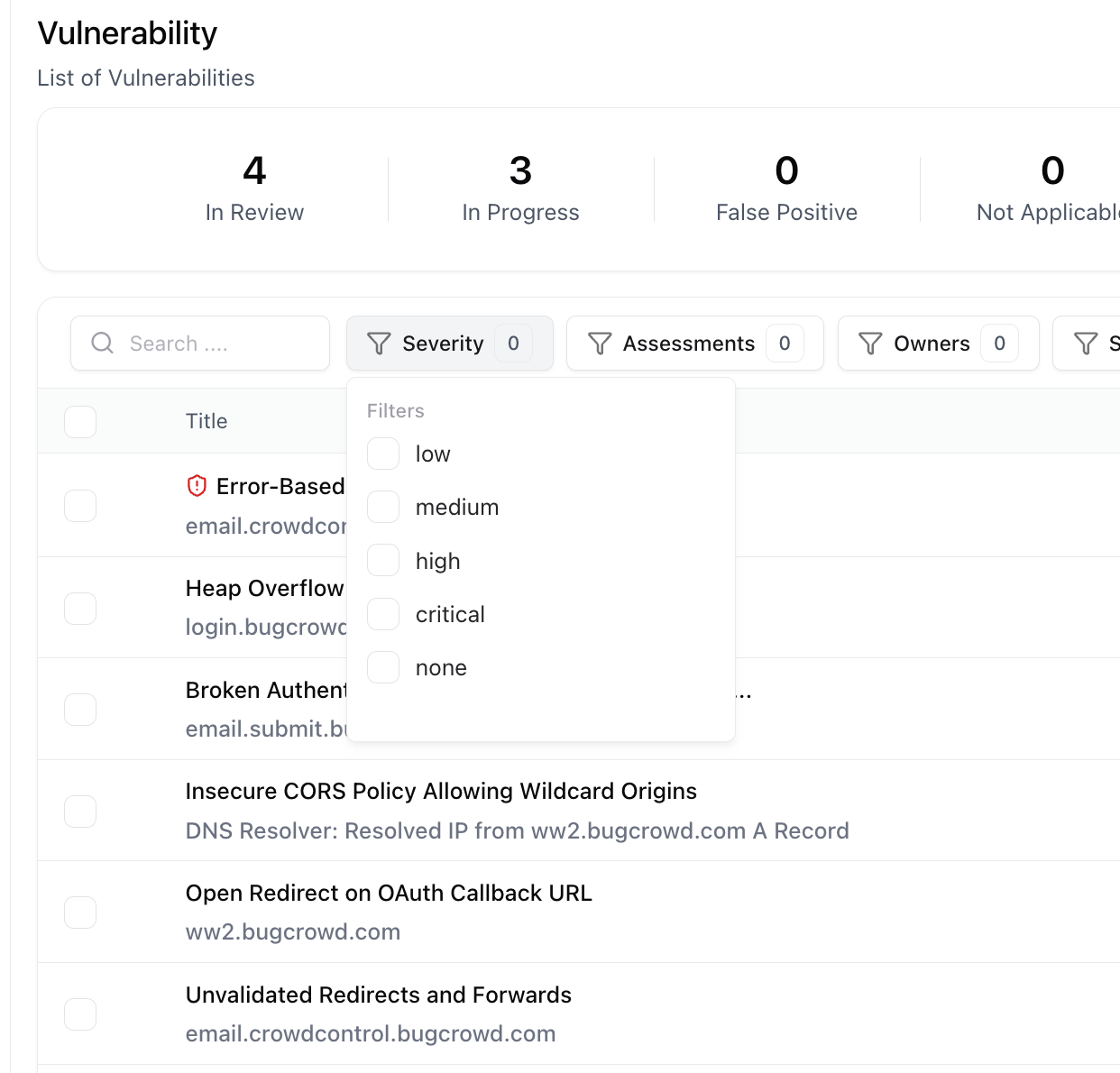
- Severity – Critical, High, Medium, Low
- Assessment – Specific assessments or projects
- Owners – Filter by assigned remediation owners
- State – In review, In progress, Re-test, Resolved, etc.
- Teams – View vulnerabilities assigned to particular departments
Combine multiple filters for advanced queries — for example, Critical vulnerabilities in Docker assessments assigned to Team A.
Vulnerability States
Each vulnerability moves through clear, trackable states — making it easy to monitor progress and identify bottlenecks in remediation:| State | Description |
|---|---|
| In Review | Under review by analysts or awaiting validation. |
| In Progress | Actively being worked on by developers or engineers. |
| Re-Test | Undergoing validation after remediation. |
| Resolved | Verified as fixed and no longer exploitable. |
| Unresolved | Not yet addressed or awaiting confirmation. |
| False Positive / Not Applicable | Marked as invalid or irrelevant to the environment. |
Sorting and Prioritization
Vulnerabilities can be sorted by severity, state, owner, or date reported — helping teams prioritize their response efficiently.You can also group by assessments or filter by remediation responsibility.
Linking to Context
Each vulnerability record links directly to:- The originating assessment (for traceability)
- Associated asset or endpoint (for impact analysis)
- Evidence and remediation notes
Vulnerability Details View
Clicking on any vulnerability from the Vulnerability List opens a detailed view that consolidates context, discussion, metadata, and evidence into a single page. This view is designed to help security teams, developers, and auditors collaborate on remediation without switching screens.
Vulnerability Description
The top section presents the full vulnerability narrative, written in a structured and readable format.Included Sections
- Title — Clear, standardized vulnerability name
- Description — Explanation of the issue and why it exists
- Steps to Reproduce — Actionable steps to validate the finding
- Impact — Security and business consequences if left unresolved
Comments & Recent Activity
All collaboration and system actions related to the vulnerability are tracked in a live activity feed.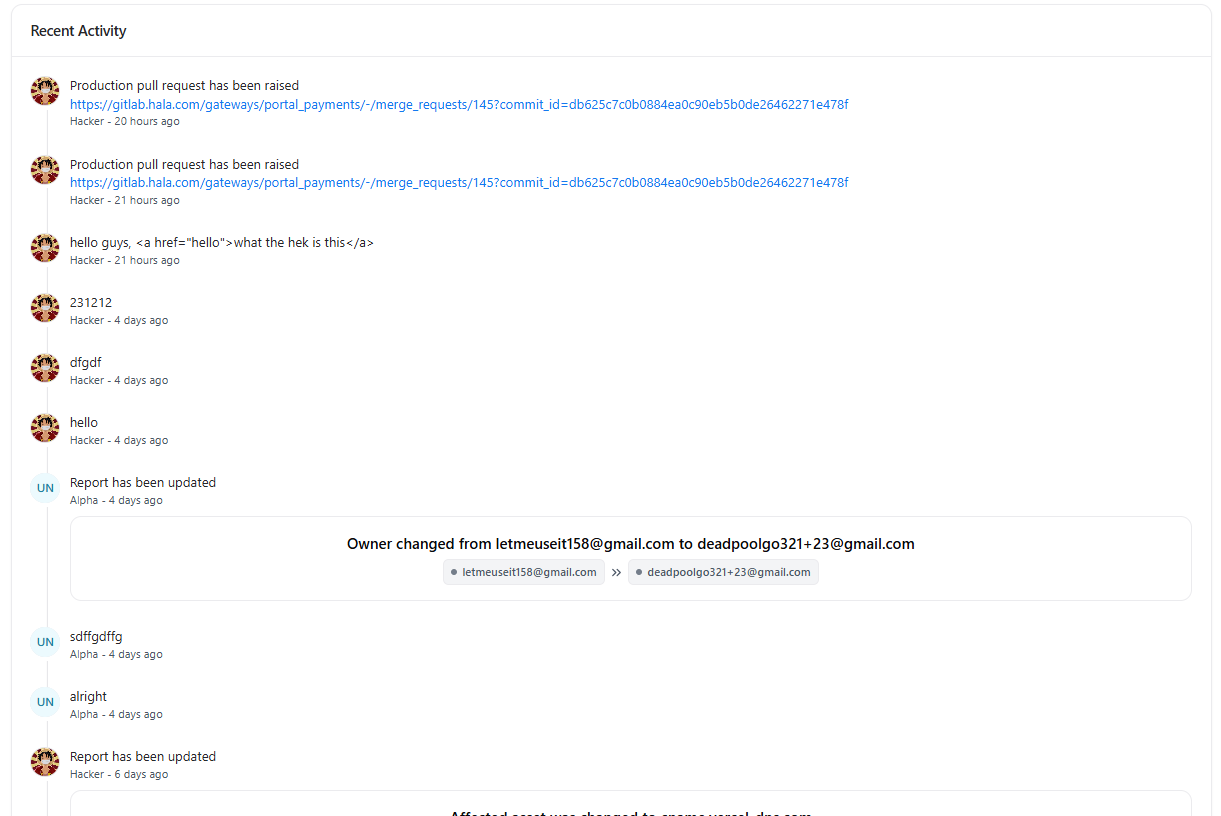
What’s Tracked
- User comments and discussions
- Owner or state changes
- Assessment updates
- External references (e.g., PRs, commits, tickets)
Use comments to tag teammates, clarify fixes, or request re-tests — all context stays tied to the vulnerability.
Report Details Panel
A side panel summarizes all critical metadata required for prioritization, ownership, and compliance.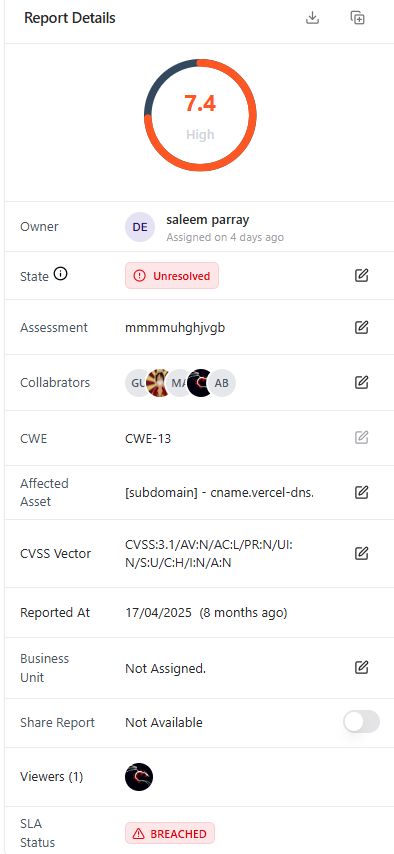
Key Metadata Displayed
- Severity & CVSS Score (visualized)
- Owner & Collaborators
- Current State (Unresolved, In Progress, Resolved, etc.)
- Assessment Source
- Affected Asset
- CWE & CVSS Vector
- SLA Status (Compliant / Breached)
- Reported Date & Business Unit
Attachments & Evidence
Evidence supporting the vulnerability can be uploaded directly within the same view.
Evidence Capabilities
- Upload screenshots, logs, PoCs, or videos
- Drag-and-drop or browse upload
- Up to 10 files, 12 MB per file
- Evidence remains permanently linked to the vulnerability
Why This Matters
This unified vulnerability view ensures that every issue is:- Clearly explained for developers
- Collaboratively discussed by all stakeholders
- Fully contextualized with severity and ownership
- Backed by evidence for validation and audits
- Tracked end-to-end from discovery to resolution
Explore Live Demo
Explore Snapsec Live — No Signup Needed
Jump straight into the live environment and see how Snapsec unifies asset intelligence, threat detection, and vulnerability tracking — all in one dashboard.