Overview
The Web Application Scanner (WAS) Dashboard provides a unified, real-time view of your application’s security health — including vulnerability distribution, endpoints analyzed, active rules, and scan activity.It serves as the central location for understanding your exposure, tracking trends, and prioritizing remediation.
Overview
The WAS Dashboard aggregates data from:- API request analysis
- Automated security scans
- Rule-based vulnerability detections
- Endpoint discovery
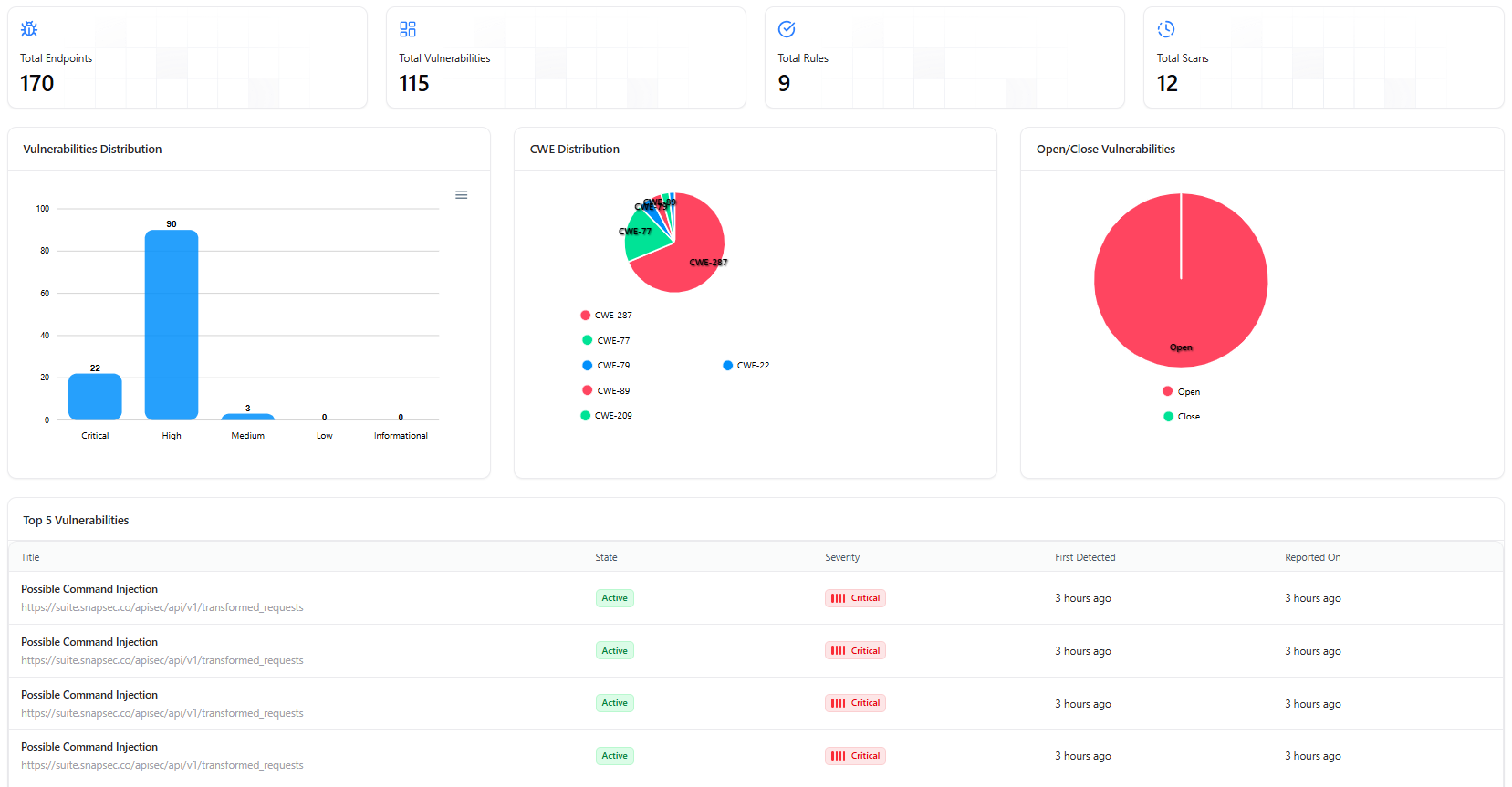
- Total Endpoints
- Total Vulnerabilities
- Total Rules Active
- Total Scans Executed
Key Metrics & Analytics
Total Endpoints
Number of API endpoints discovered and analyzed.
Total Vulnerabilities
Total number of vulnerabilities detected across all API endpoints.
Total Rules
Count of rule checks currently active for detection.
Total Scans
Total number of scans executed in the workspace.
Visual Analytics & Security Trends
Vulnerability Severity Distribution
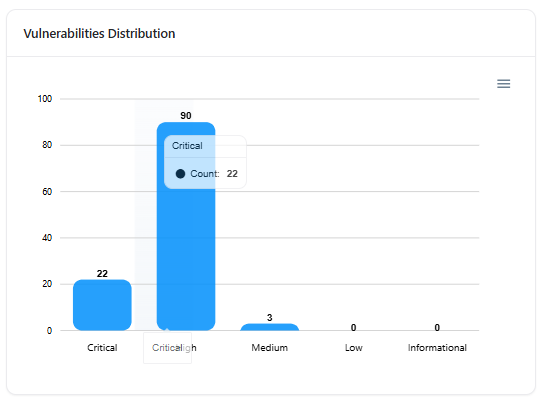
- Critical
- High
- Medium
- Low
- Informational
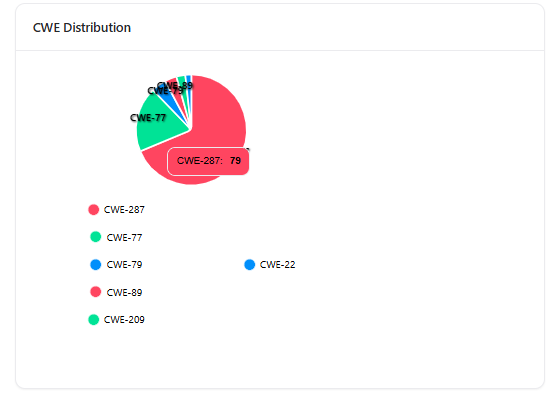
CWE Distribution
Open/Closed Vulnerabilities
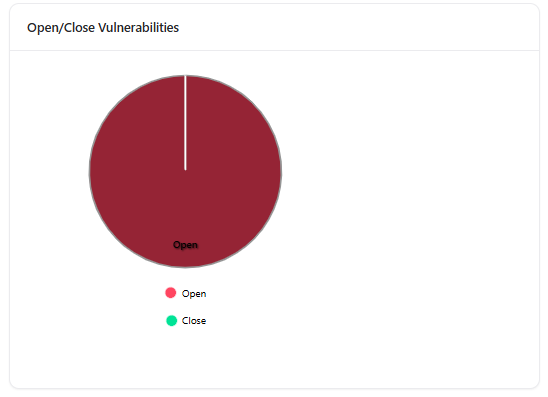
- Active vulnerabilities
- Resolved vulnerabilities
Top Vulnerabilities
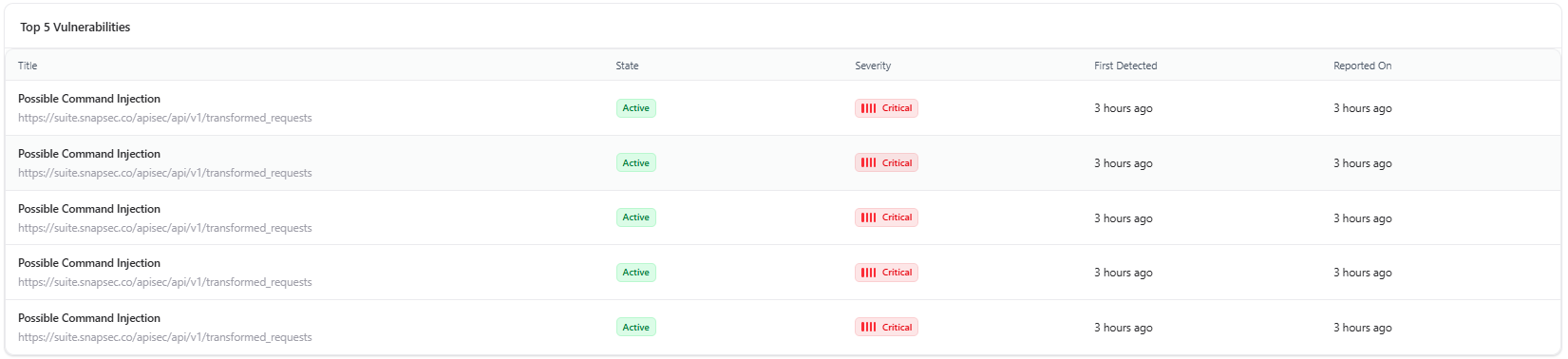
- Most frequent vulnerabilities
- Affected endpoints
- Severity
- Detection timestamps
- Title
- State
- Severity
- First Detected
- Reported On
How to Use the Dashboard
Track Security Posture
Monitor trends across vulnerabilities, endpoints, severity, and detection rules.
Identify High-Risk Endpoints
Quickly detect endpoints repeatedly affected by access control or logic flaws.
Validate Detection Rules
Ensure rules are triggering correctly across environments and projects.
Improve Scan Efficiency
Use scan frequency and vulnerability density metrics to adjust scan profiles.
Explore Live Demo
Explore Snapsec Live — No Signup Needed
Jump straight into the live environment and see how Snapsec unifies asset intelligence, threat detection, and vulnerability tracking — all in one dashboard.