Overview
The Subdomain Catalog in AIM provides a unified inventory of every subdomain discovered across your organization.It helps you track vulnerability exposure, risk scores, ownership, and environment classification — all within one centralized view.
Overview
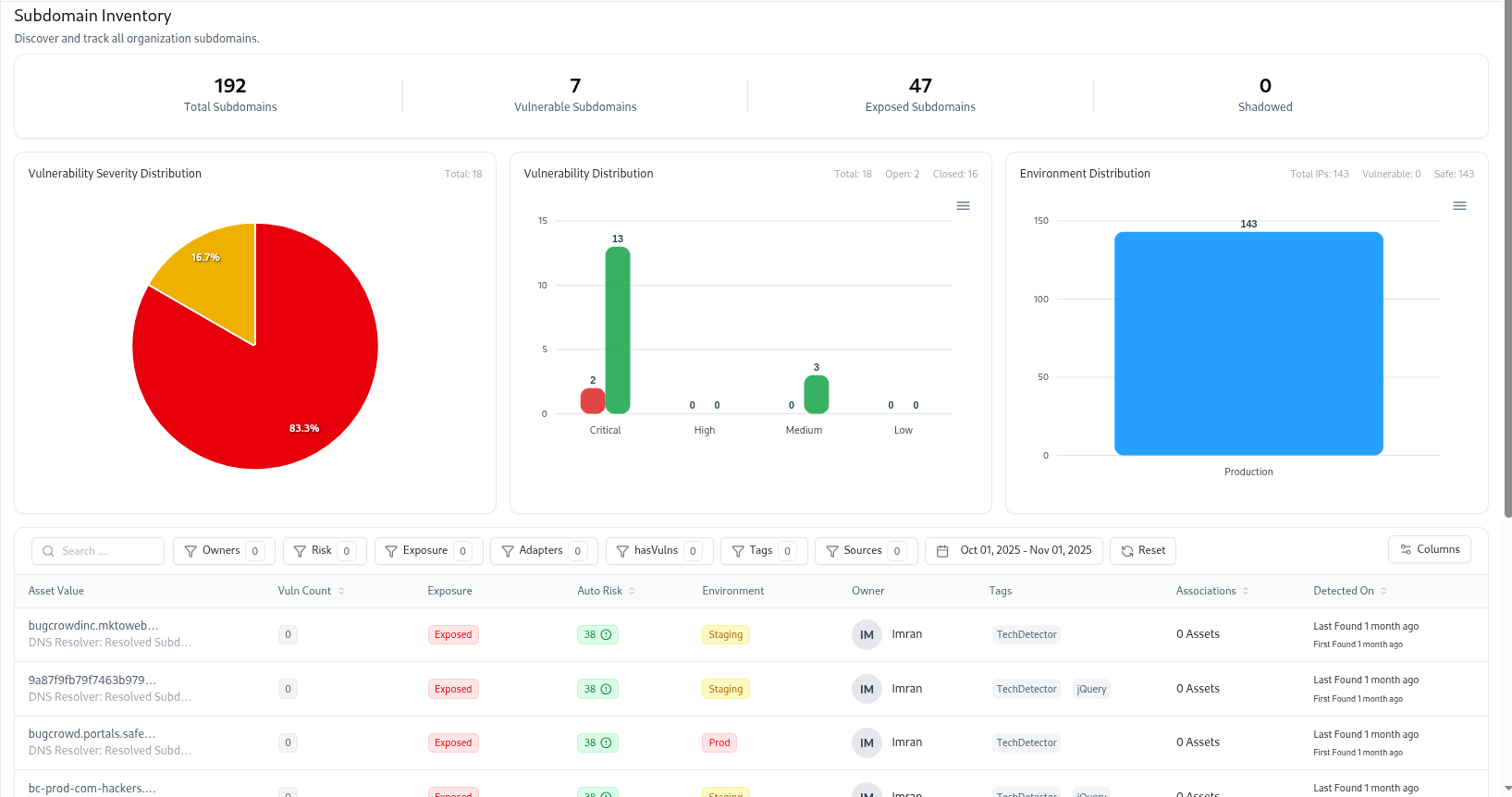
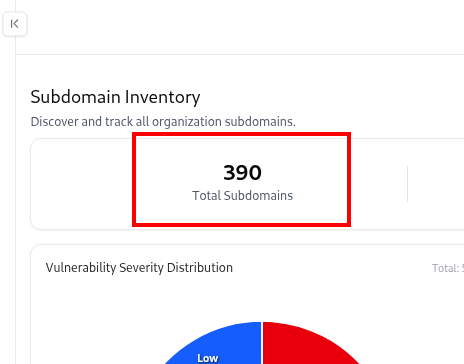
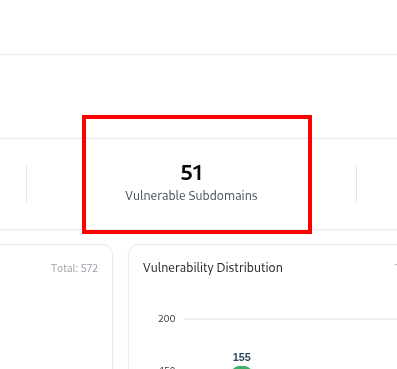
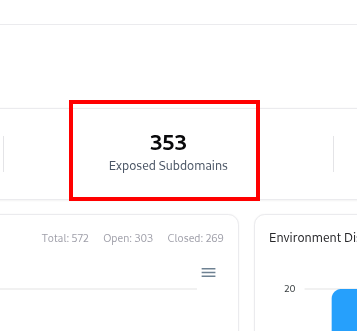
The Subdomain Catalog lists every subdomain identified through integrations, scans, or adapters (like DNS, CRT, TechDetect, or VM).It provides analytics-driven visualizations at the top — summarizing total subdomains, exposed assets, vulnerable entries, and environment distribution — followed by an interactive table of subdomain details. This page serves as the primary discovery layer before diving into each subdomain’s detailed profile page.
Key Metrics and Analytics
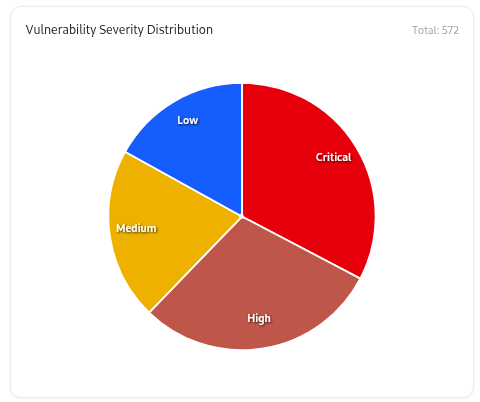
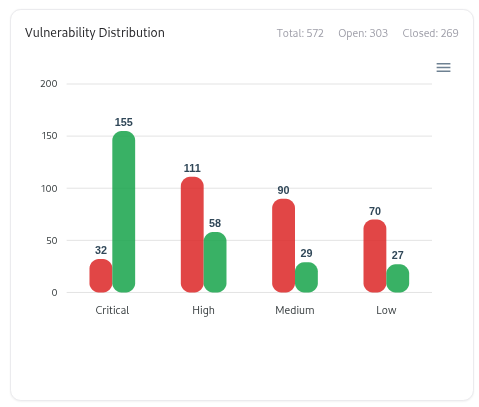
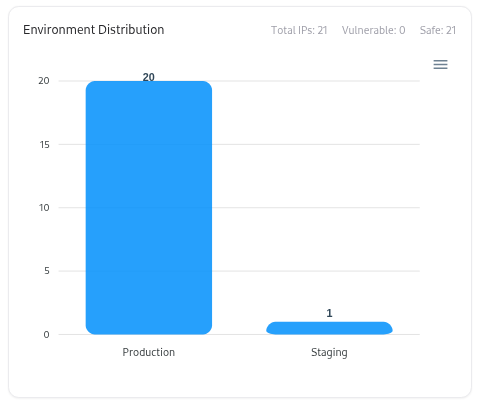
Search, Filters, and Sorting
The catalog offers advanced search and filter options to locate specific subdomains:| Filter | Description |
|---|---|
| Owners | Filter by assigned owner or responsible user. |
| Risk | Sort or filter by automatic risk score. |
| Exposure | Show only subdomains marked as Exposed or Safe. |
| Environment | Filter by environment tag such as Prod, Staging, or Dev. |
| Adapters | Show subdomains discovered via specific adapters (e.g., DNS, CRT). |
| Tags | Filter by applied business or technology tags. |
| Sources | View which data source originated the discovery. |
| Date Range | Filter by first or last detection date to focus on new findings. |
Subdomain Table Columns
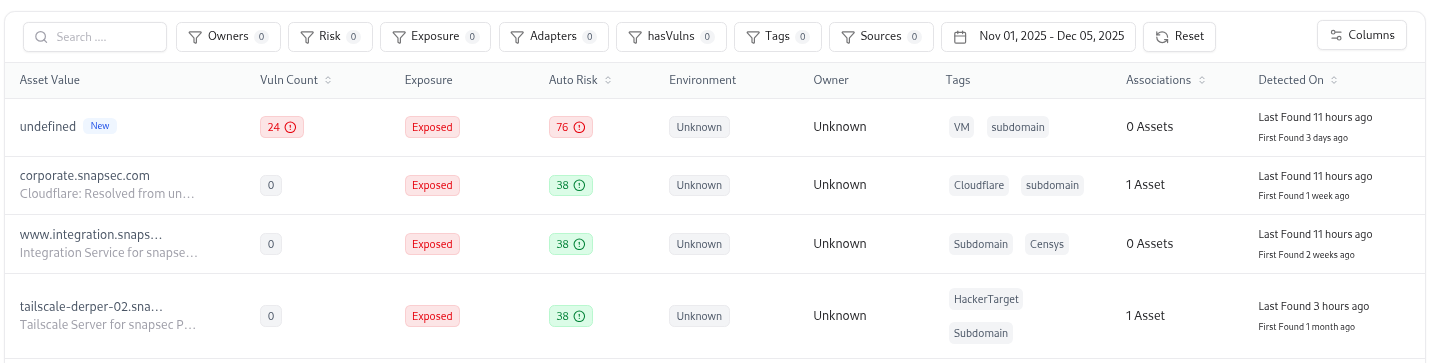
| Column | Description |
|---|---|
| Asset Value | Subdomain name (with DNS resolver info). |
| Vuln Count | Number of vulnerabilities linked with the subdomain. |
| Exposure | Current exposure status (Exposed, Safe, Shadowed). |
| Auto Risk | Auto-calculated score based on associated vulnerabilities and rules. |
| Environment | Environment classification (Production, Staging, Dev). |
| Owner | Assigned individual responsible for this subdomain. |
| Tags | Labels like TechDetect, jQuery, or business-specific tags. |
| Associations | Number of related assets or dependencies. |
| Detected On | Timeline of when the asset was first and last found. |
Subdomains Full View
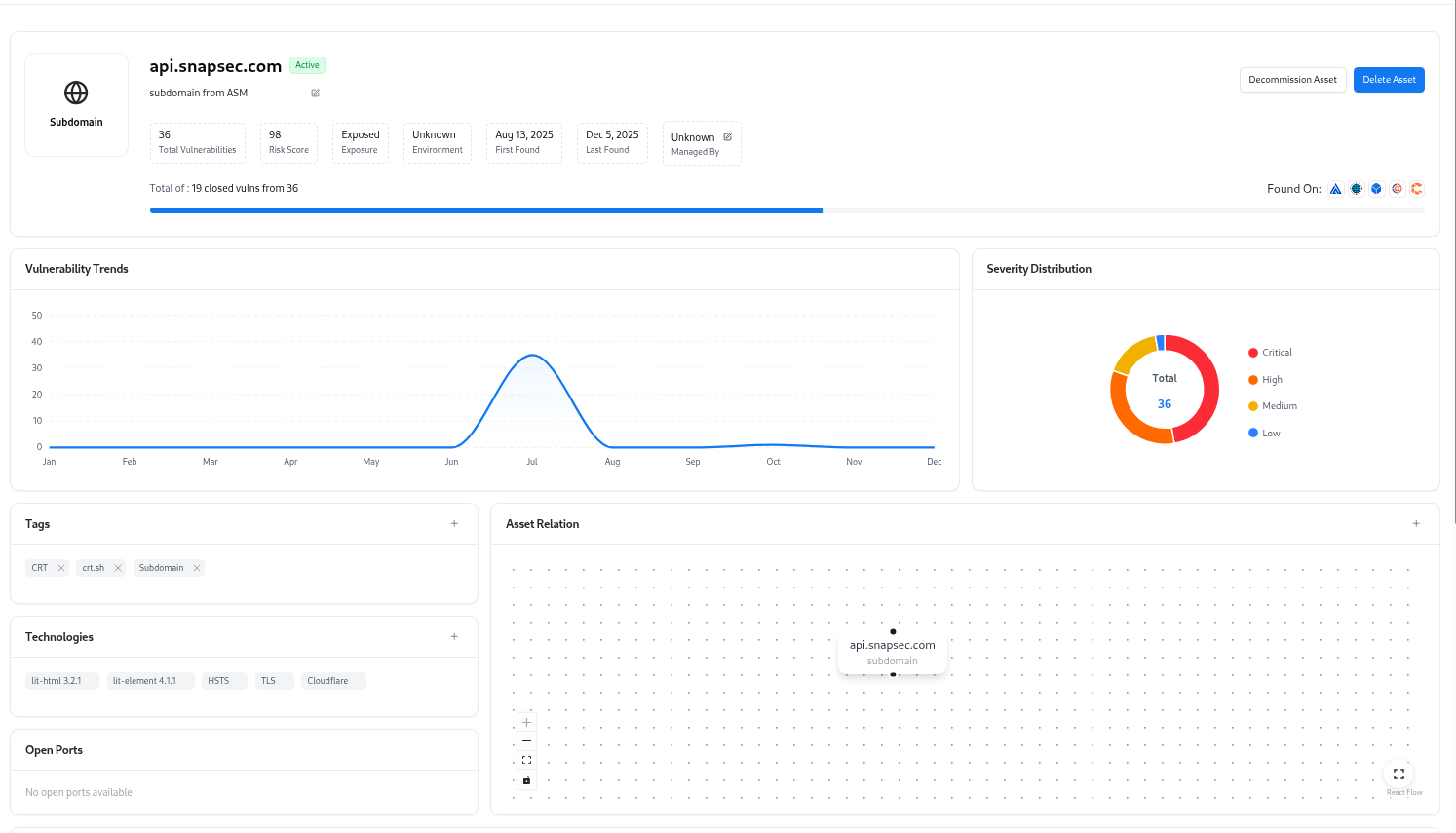
- Vulnerability risk and trends over time
- Severity distribution (Critical, High, Medium, Low)
- Technology and service fingerprinting
- Open port visibility and relation mapping
- Tags, ownership details, and adapter discovery sources
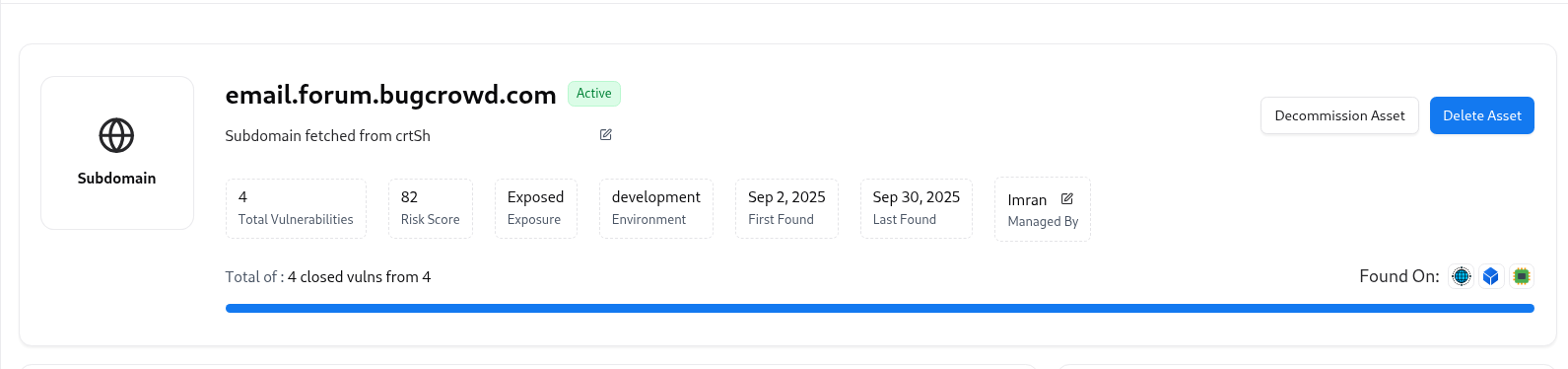
Subdomain Summary
At the top, you’ll find an overview of the subdomain, including:| Field | Description |
|---|---|
| Subdomain Name | Fully qualified domain name (e.g., email.forum.bugcrowd.com). |
| Status | Shows if the subdomain is Active, Decommissioned, or Deleted. |
| Source | Indicates which adapter discovered it (e.g., CRTsh, DNS, VM). |
| Exposed | Marks whether the subdomain is externally exposed. |
| Environment | Classification such as production, staging, or development. |
| Risk Score | Calculated automatically based on asset classifiers. |
| Managed By | Owner or team responsible for maintaining this subdomain. |
| Detection History | Displays “First Found” and “Last Found” timestamps. |
Vulnerability Insights
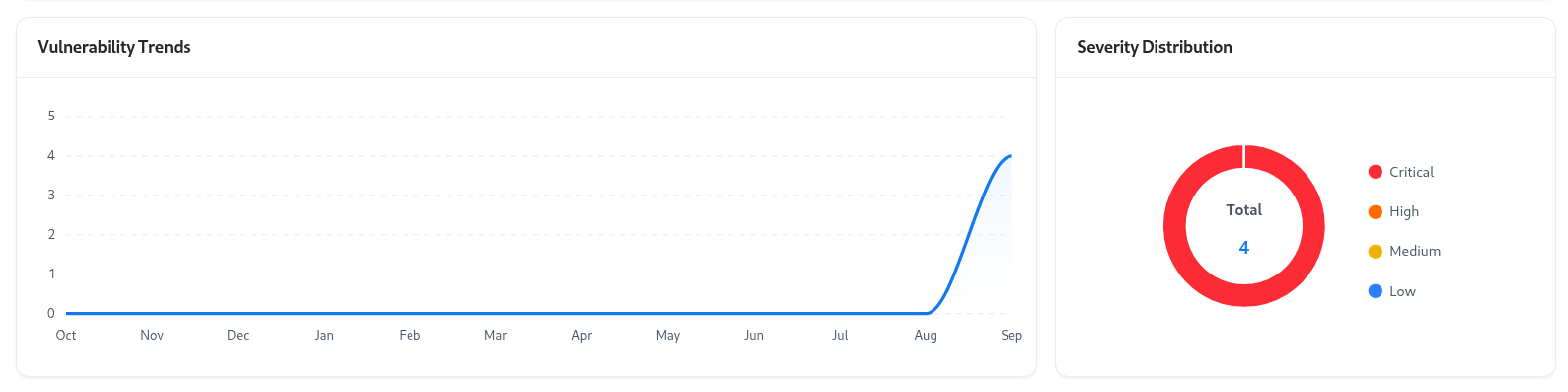
Vulnerability Trends
Displays how vulnerabilities have changed over time for this specific subdomain.
It helps visualize the impact of remediation or new findings.
It helps visualize the impact of remediation or new findings.
Severity Distribution
A breakdown of vulnerabilities by severity — Critical, High, Medium, and Low — giving instant insight into overall risk posture.
- Vulnerability title
- Assessment name
- Severity level
- Current remediation state (In Review, Resolved, Retest)
- Detection timeline
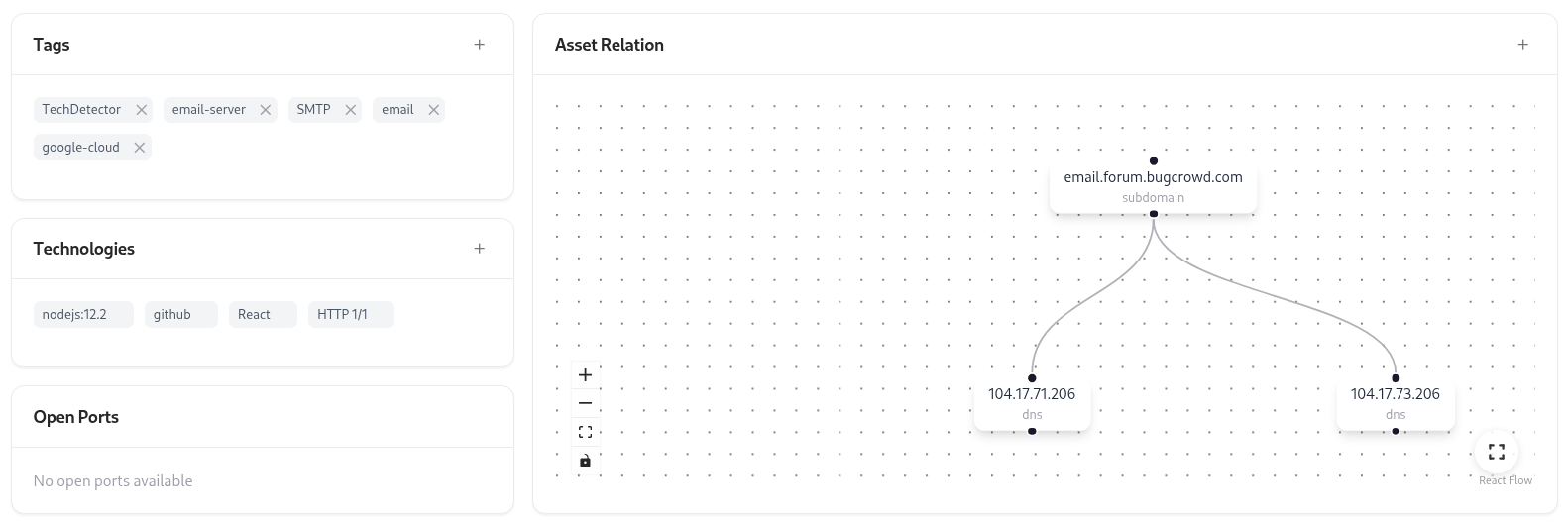
Tags and Technologies
Tags
Tags help categorize assets by business unit, product, or technology.
Examples:
Examples:
email-server, google-cloud, smtp, production.Detected Technologies
Lists technologies identified via asset fingerprinting — including languages, frameworks, and services (e.g., NodeJS, React, HTTP/1.1, GitHub).
Open Ports & Asset Relations
Open Ports
Shows real-time visibility into network exposure:- Identifies open ports with status, service type, and security risk.
- Helps network teams close unnecessary or unsafe ports.
Asset Relations Graph
Visualizes how this subdomain is connected to other assets like IP addresses or parent domains.It allows easy tracing of asset lineage and network topology for impact analysis.
Ownership & Management Actions
- Assign or Change Owner – ensure accountability.
- Decommission Asset – mark a subdomain as inactive or migrated.
- Delete Asset – permanently remove deprecated entries.
How Subdomains Are Discovered
AIM continuously updates subdomain data using multiple adapters such as:- CRTsh Adapter – pulls SSL certificate records for domain enumeration.
- DNS Adapter – maps DNS record structures.
- VM Adapter – enriches assets with linked vulnerabilities.
- TechDetect Adapter – fingerprints technologies and open services.
Example Use Cases
- Security Analysts: Track critical or high-risk subdomains and their associated vulnerabilities.
- Asset Managers: Assign ownership, tag business units, and ensure coverage across cloud and on-premises assets.
- Developers: Understand which staging or dev environments are publicly exposed.
- Compliance Teams: Validate that production domains have no unmanaged external exposure.
Explore Live Demo
Explore AIM Live — No Signup Needed
Instantly explore how Snapsec AIM discovers, enriches, and tracks every asset in real time — all without creating an account.