Overview
Integrations bridge the Attack Surface Management (ASM) and Vulnerability Management (VM) modules.They allow all detected exposures to be automatically synced into VM as tickets for centralized tracking and remediation.
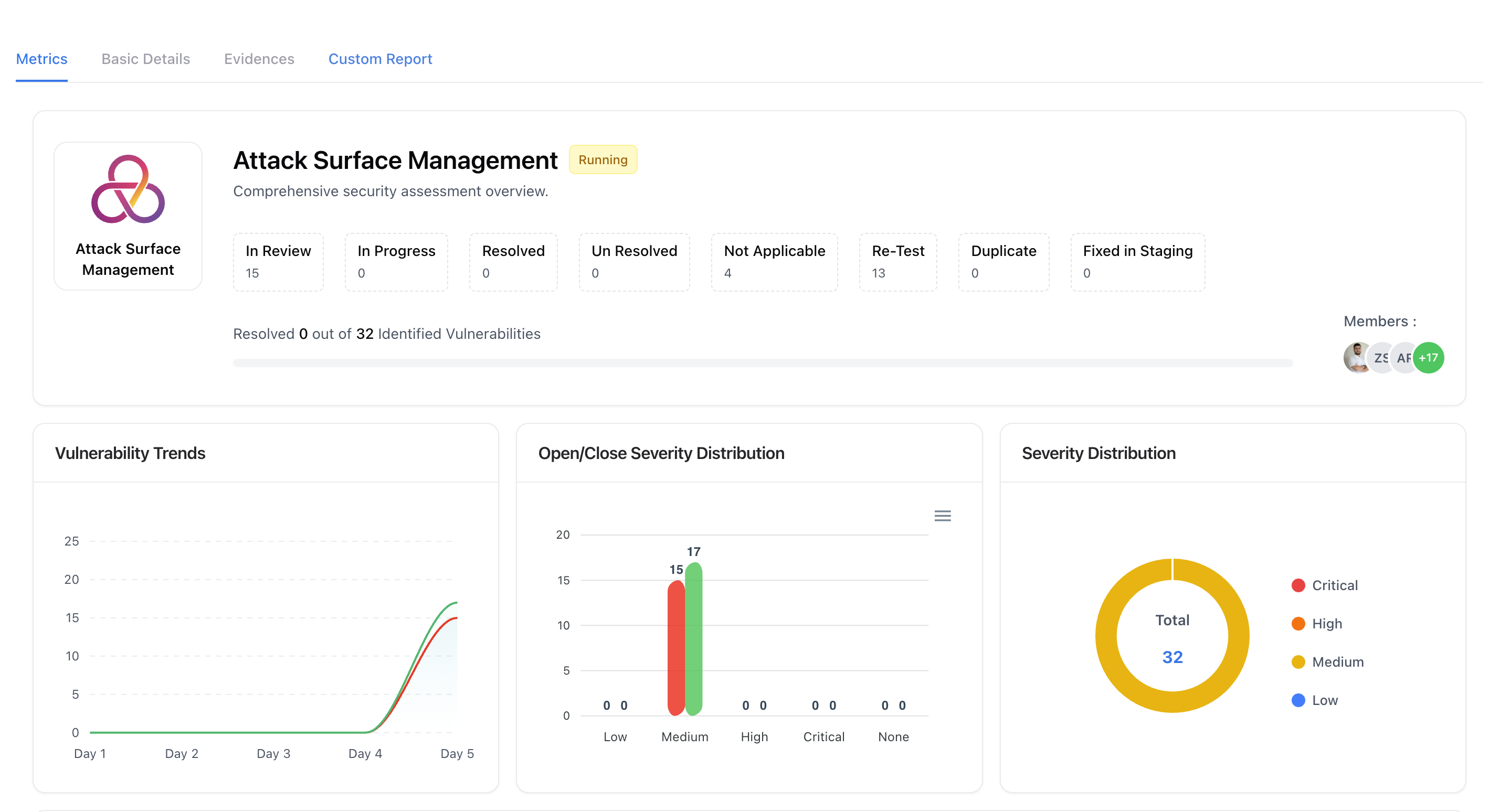
Overview
The Integrations page enables organizations to link their ASM findings to a specific assessment in VM.Once linked, all detected exposures are sent as tickets, allowing unified monitoring and lifecycle tracking — from detection to closure.
Key Capabilities
Assessment Selection
Choose an active VM assessment where all ASM exposures should be sent.
This could be a quarterly assessment, continuous scan, or any custom project.
This could be a quarterly assessment, continuous scan, or any custom project.
One-Click Sync
Use the Sync Vulns button to immediately push all exposures into VM.
Each exposure is converted into a ticket with its reason, severity, and asset context.
Each exposure is converted into a ticket with its reason, severity, and asset context.
Auto Status Tracking
ASM automatically tracks exposure resolution back from VM.
When an exposure ticket is marked as resolved in VM, the ASM status updates in real-time.
When an exposure ticket is marked as resolved in VM, the ASM status updates in real-time.
Centralized Visibility
View your entire attack surface and remediation status across both products from one place.
Workflow Example
- Select your desired assessment (e.g., Q1 - Attack Surface Management).
- Click Sync Vulns to export all ASM exposures to VM.
- Each exposure becomes a ticket with full context (asset, reason, severity, etc.).
- Once developers fix the issue and close the ticket in VM, ASM reflects the change automatically.
Example Use Case
- ASM detects several IPs with open SSH ports (22) and expired SSL certificates.
- You sync them to VM under Continuous Vulnerability Scanning.
- The VM team triages, assigns owners, and tracks SLAs.
- When tickets are closed, ASM marks those exposures as Resolved automatically.
Benefits
✅ Unified visibility between ASM discovery and VM remediation✅ Automated exposure tracking and closure validation
✅ Reduced manual overhead in managing attack surface risks
✅ Cross-module consistency for reporting and compliance
Explore Live Demo
Explore ASM Live — No Signup Needed
Instantly explore how Snapsec Attack Surface Management (ASM) discovers external assets, identifies exposures, enriches attack surface data, and visualizes risk — all in real time, without creating an account.