Overview
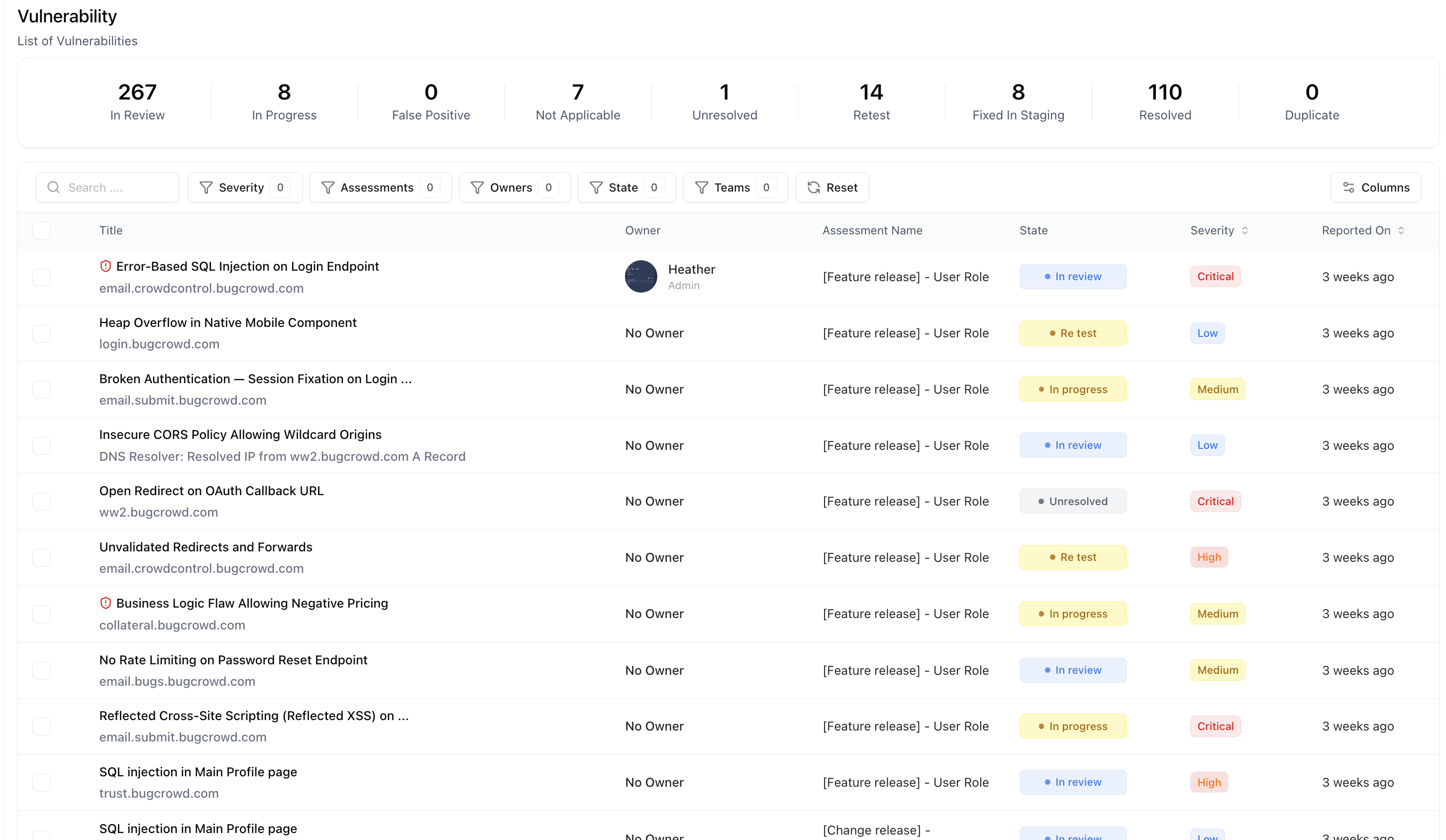
The Vulnerability Lifecycle feature ensures every finding is captured, validated, assigned, and resolved in a structured flow.It gives complete visibility into the journey of a vulnerability — from initial discovery to successful remediation.
Key Capabilities
End-to-End Tracking
Follow vulnerabilities through defined states like Open, In Progress, Retest, and Resolved — ensuring nothing slips through.
Ownership & Accountability
Assign findings to responsible owners and track progress with live status updates and due dates.
State Automation
Automate transitions based on SLA breaches, retest results, or integrated issue tracker updates.
Historical Context
Access complete timelines, changes, and comments for every finding to maintain audit-ready records.
Value
Achieve full control and traceability over every vulnerability, ensuring faster fixes, reduced risk, and stronger compliance.Next Steps
Explore Live Demo Now
Follow our quickstart guide to set up your organization and start securing your assets today.