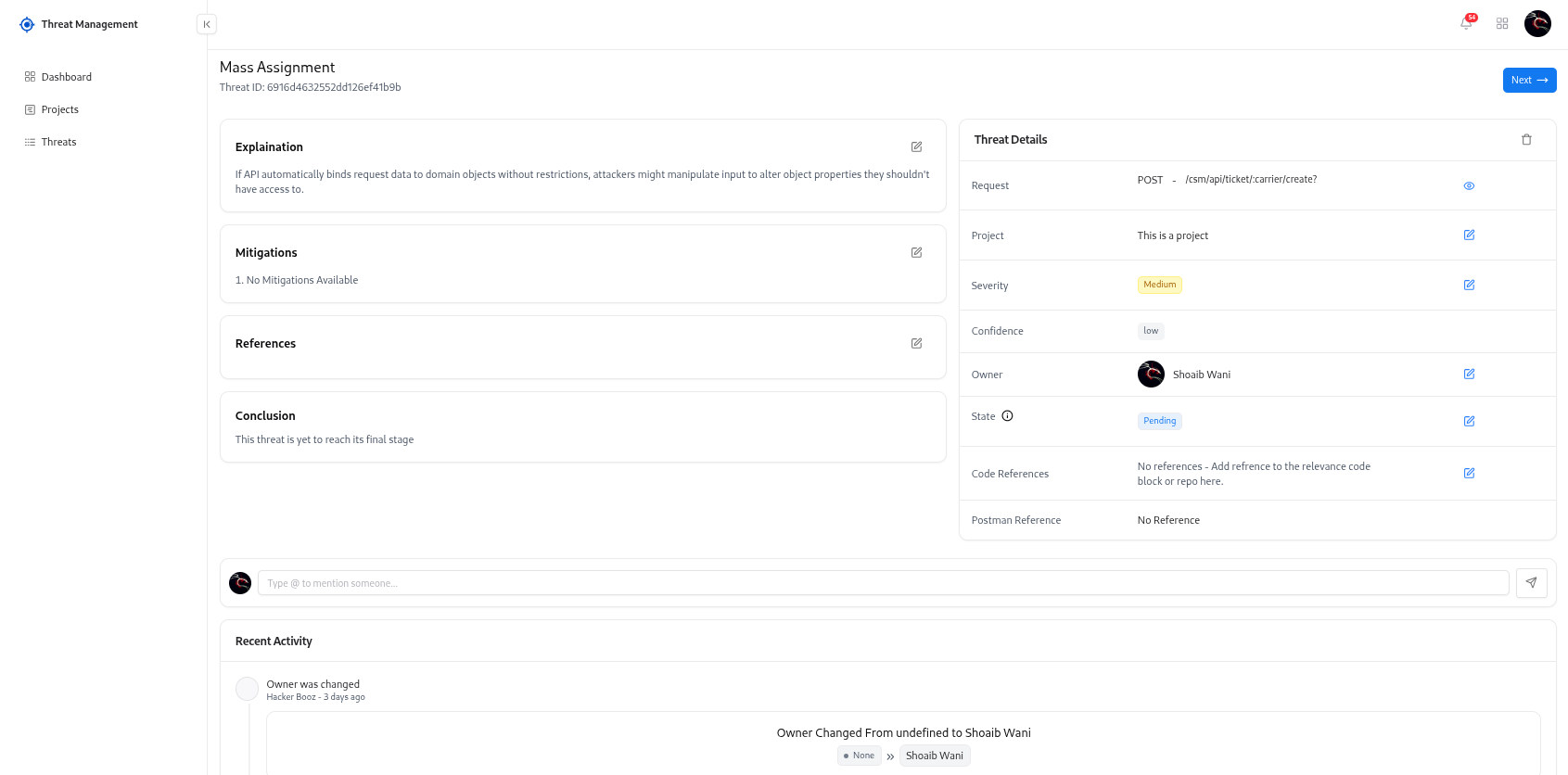
Overview
Threat Analysis provides deep, structured insight into every identified threat.Each threat contains full context — including explanations, severity, confidence, evidence, request metadata, mitigations, and activity history — enabling teams to investigate effectively and resolve issues with precision.
Key Capabilities
Comprehensive Threat Breakdown
View complete explanations detailing what the threat is, how it occurs, and the impact it creates.
Mitigation Guidance
Access actionable remediation steps aligned with industry best practices and API security principles.
Reference Links & CWE Mapping
Review CWE IDs, OWASP categories, documentation links, and additional references for deeper research.
Request Metadata
Analyze originating request details including method, URL, payload, headers, and environment context.
Severity & Confidence
View severity and confidence ratings to understand prioritization and threat reliability.
Audit & Activity Logs
Track every change, update, discussion, and verification event within the threat’s history.
Value
Threat Analysis equips teams with everything they need to understand, validate, and remediate threats effectively.With structured explanations, evidence, request context, and full audit history, teams can make accurate decisions and resolve issues faster.
Next Steps
Explore Live Demo Now
Dive deeper into threat analysis with Snapsec.