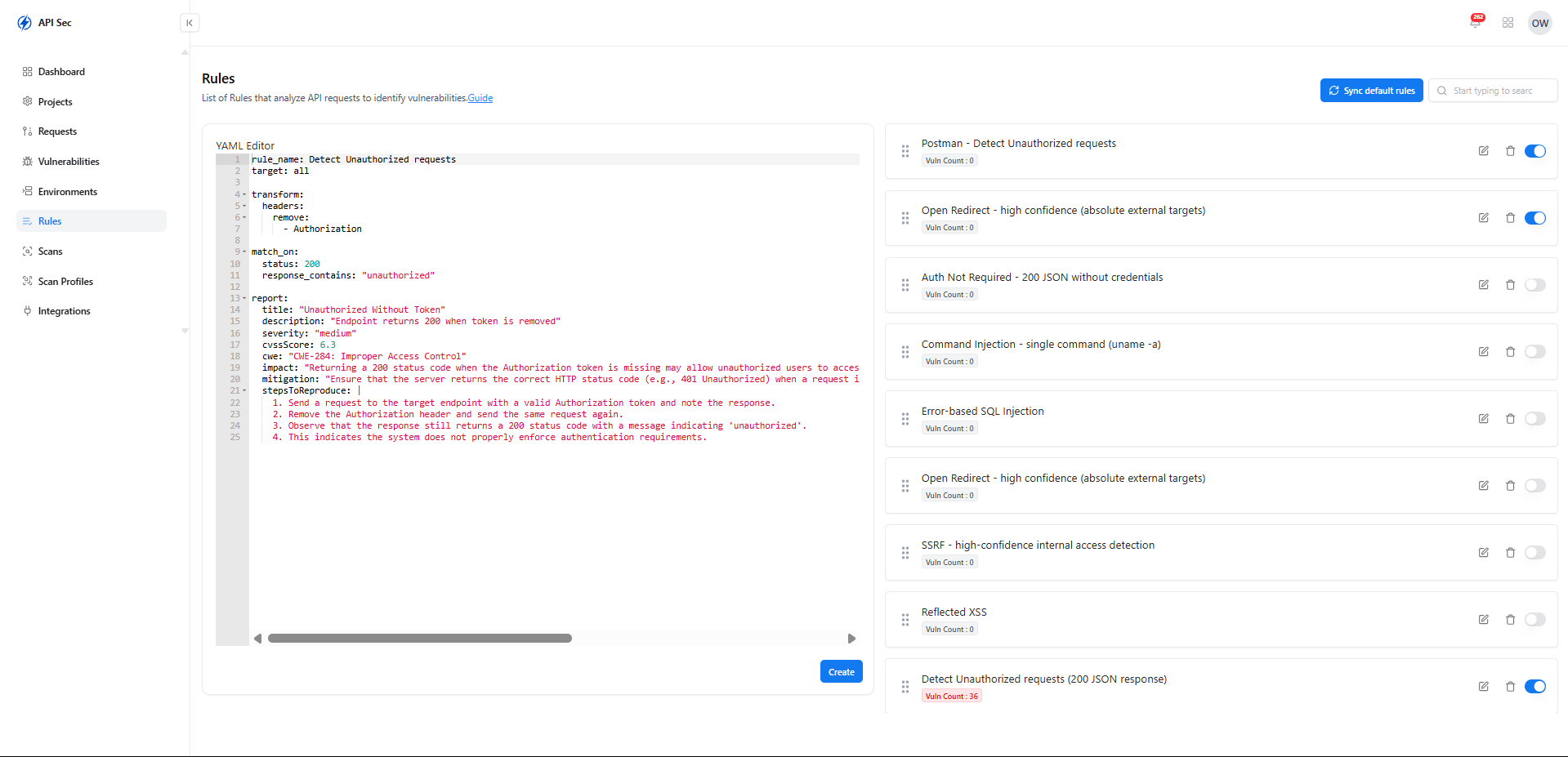
Overview
The Customizable YAML Rule Engine empowers teams to define their own API security testing logic using a flexible YAML-based syntax.From request transforms and behavioral validations to CWE-driven response analysis, the engine enables deep, customizable, and highly targeted API vulnerability detection for any endpoint or workflow.
Key Capabilities
Flexible YAML-Based Rules
Write and modify security rules using a clean YAML structure designed for clarity and extensibility.
Custom Transforms
Apply request transforms, payload modifications, or dynamic injections to simulate advanced attack patterns.
Response Validation Logic
Define expected or forbidden behaviors and validate API responses with custom matchers and conditions.
CWE & Category Mapping
Map rules to CWE categories to ensure structured, industry-aligned vulnerability classification.
Reusable Detection Modules
Build modular rules that can be shared across projects, collections, and environments.
Rule Activation & Versioning
Enable, disable, or version rules to maintain control over testing logic as APIs evolve.
Value
Unlock complete flexibility in API security testing.The YAML rule engine enables precise control, deeper coverage, and tailored detection paths — ensuring your testing adapts to evolving API behaviors and business logic.
Next Steps
Explore Live Demo Now
See how YAML-based rules enable advanced, customizable API security testing.